Safe intercommunication method and apparatus between two isolated networks
A network-to-network, security technology, applied in the field of security intercommunication, can solve the problem of huge server system cost, etc., and achieve the effect of communication security, convenient installation, and complete functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described in detail below with reference to the embodiments of the drawings.
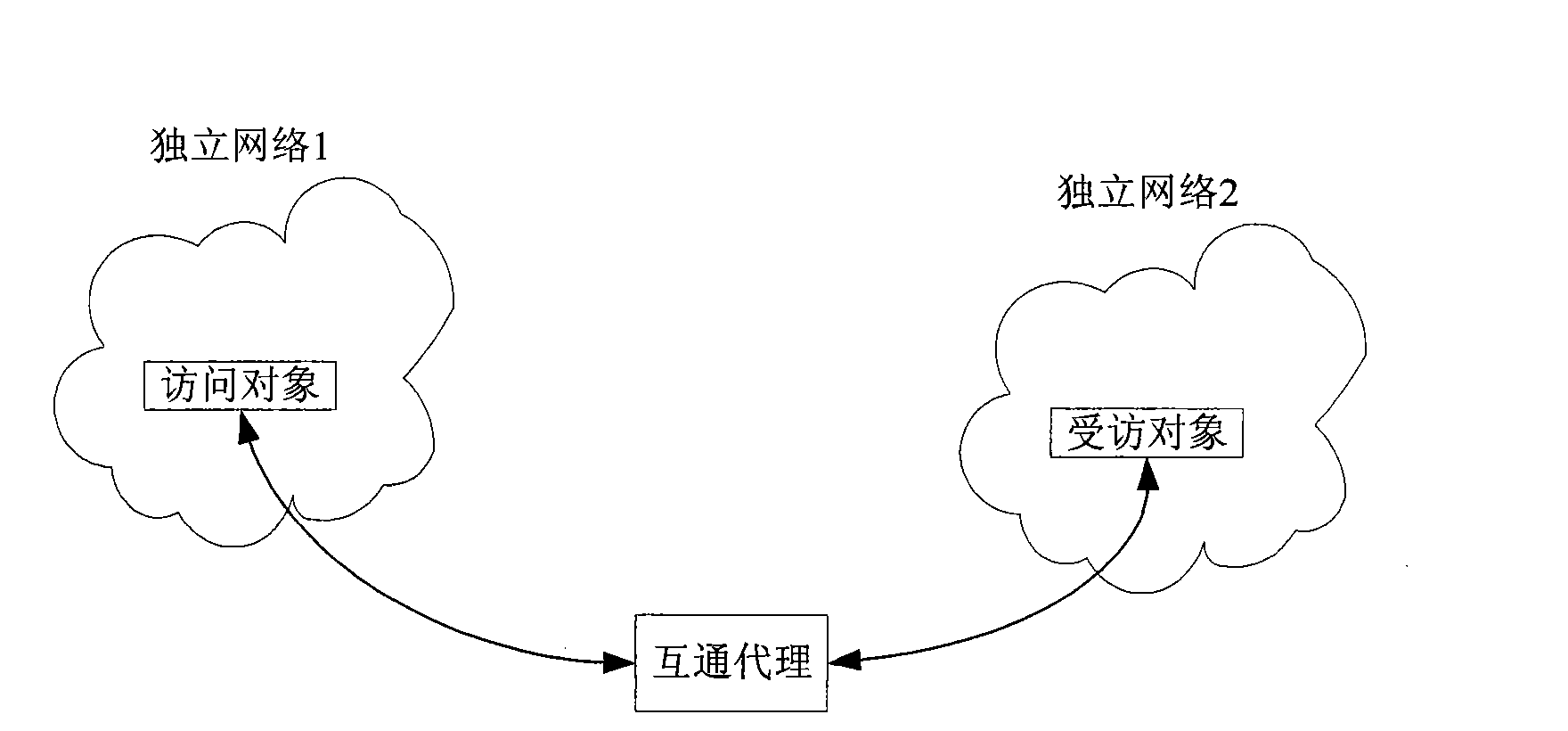
[0033] On the one hand, the present invention provides an improved method for providing safe access to resources maintained on independent networks, and establishes secure communication for devices between two independent networks. This method can be accessed by the access object through the use of a standard web browser. The intercommunication agent transfers to authorize specific operations to the interviewed object. The intercommunication agent can be in two independent networks—independent network 1 and independent network 2, or in a public network outside the two independent networks, but the intercommunication network must maintain communication with the outside world through the public network ,see figure 1 .
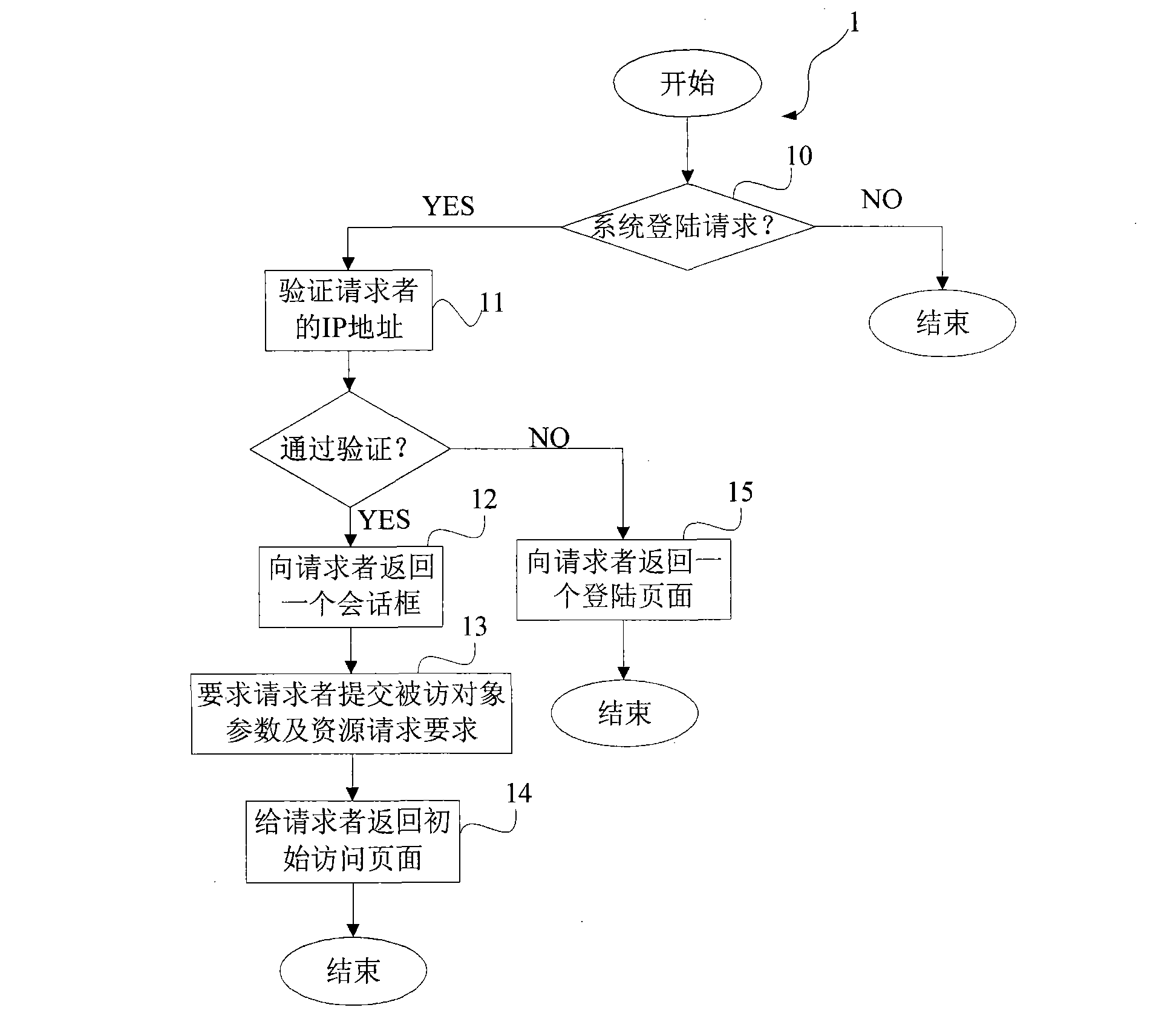
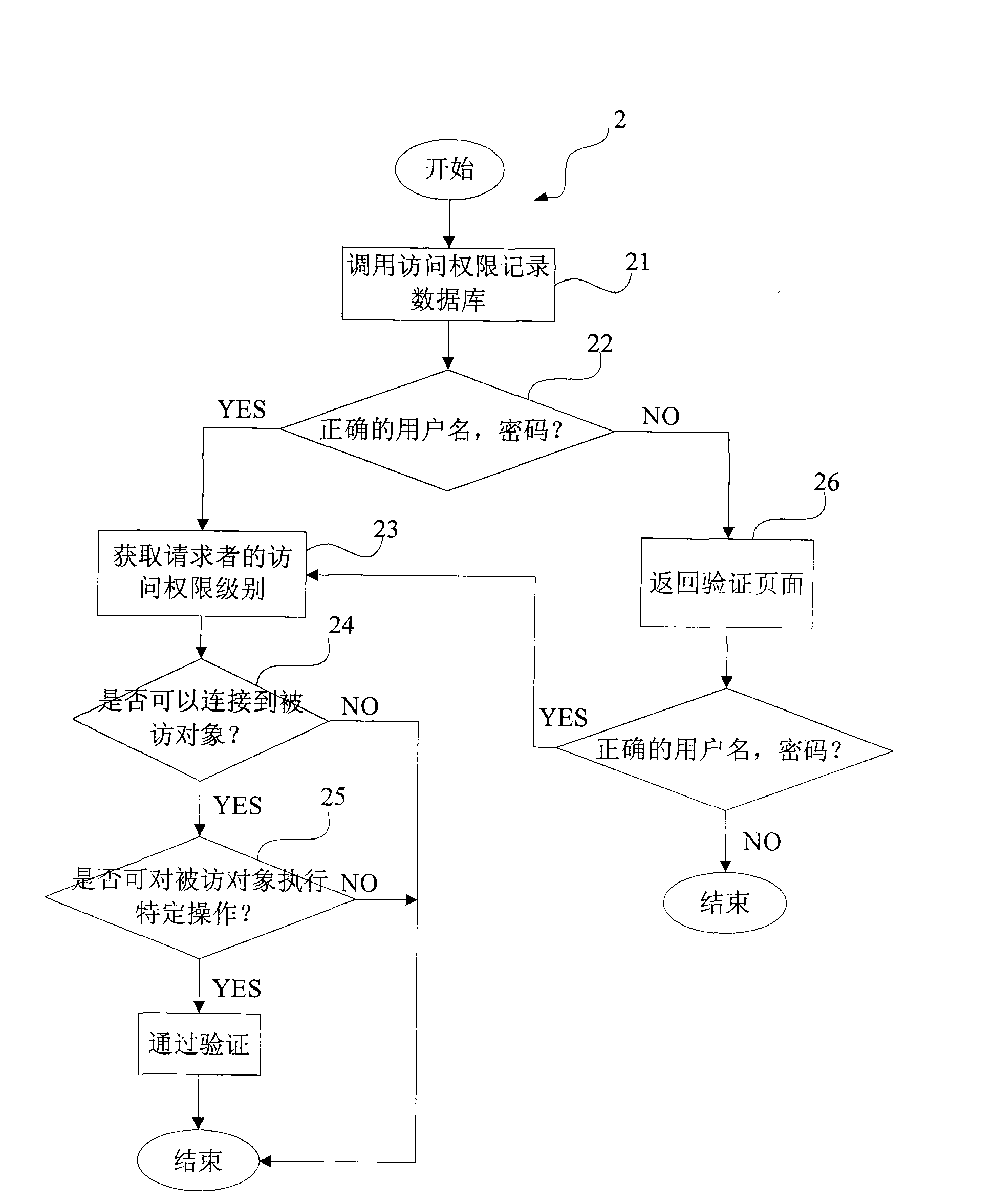
[0034] Such as figure 2 As long as the above-mentioned interworking agent receives the access request of the access object, it will automatic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com