Computer starting up identifying system and method
An identity authentication and authentication method technology, applied in the computer boot identity authentication system and its authentication field, can solve the problems of easy intrusion and low security, and achieve the effect of not easy to illegally intrude and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
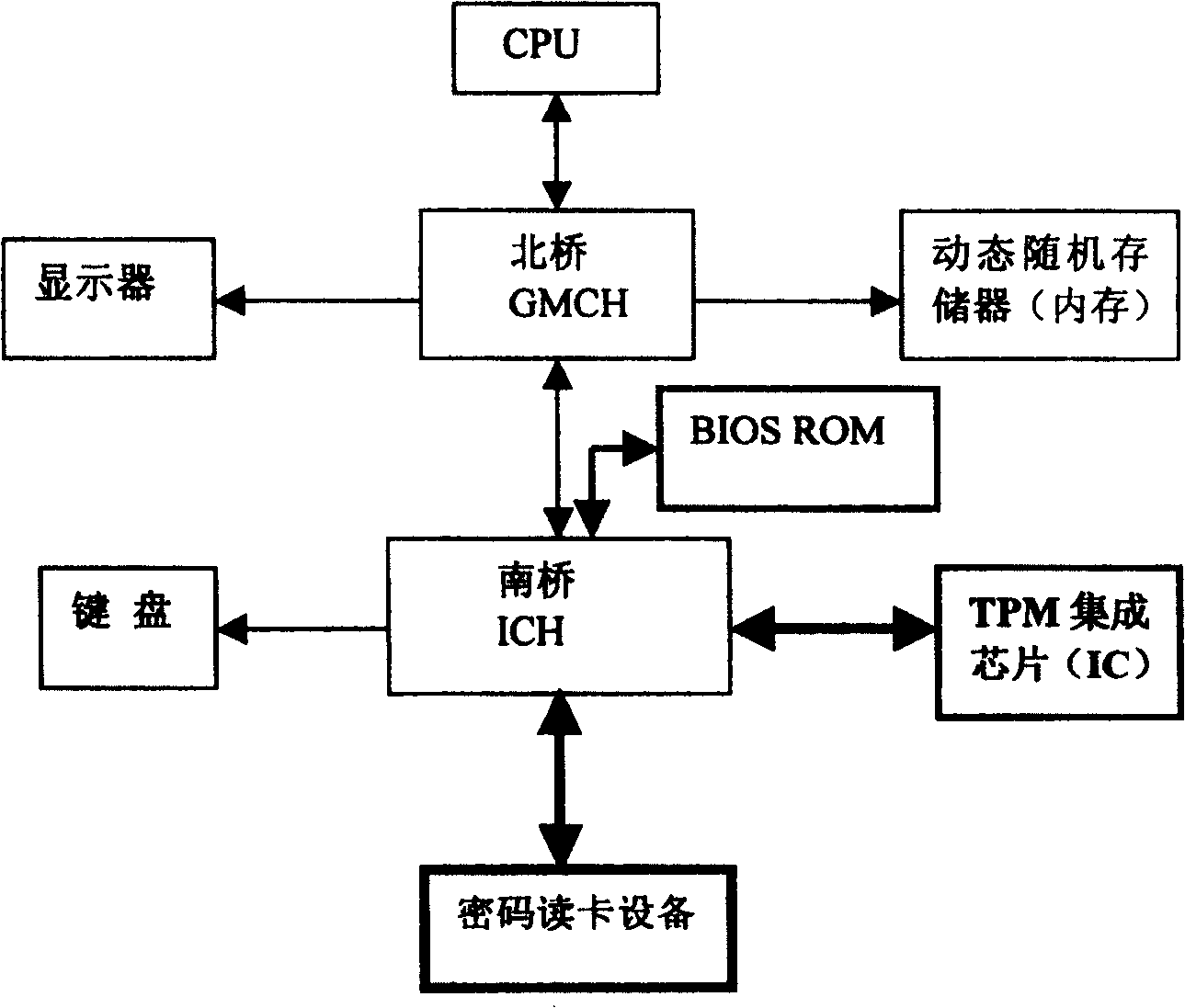
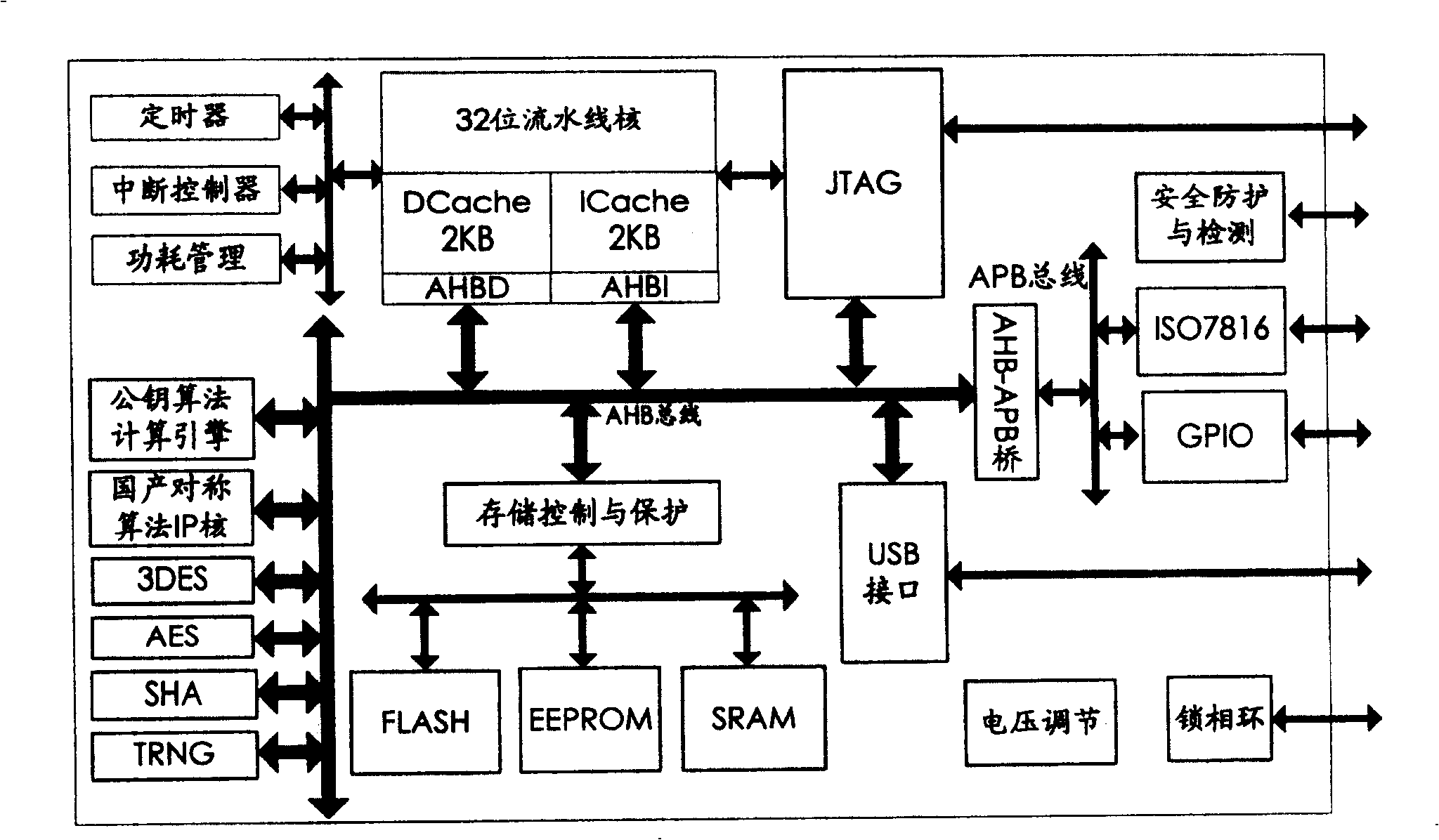
[0039] see Figure 4, the computer power-on identity authentication system of the present invention comprises sequentially connected CPU, graphics and storage centralized controller (hereinafter referred to as North Bridge) and peripheral equipment integrated centralized controller (hereinafter referred to as South Bridge), display and DRAM (hereinafter referred to as internal memory) respectively Connect with North Bridge, keyboard, BIOS ROM and trusted embedded system (hereinafter referred to as TPM module) are respectively connected with South Bridge, and a password card reader device is connected with TPM module. Wherein, the TPM module includes the TPM hardware integrated circuit and micro-operating system (μOS) software that can set and operate the bottom layer of the hardware. The password card reader device in this embodiment can be an IC card reader drive device or a fingerprint photoelectric collector.
[0040] The password card reading device of the computer startup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com