Digital evidence integrality preserving method based on computer evidence
A technology of computer forensics and digital evidence, applied in digital data protection, electronic digital data processing, computer security devices, etc., to prevent modification, avoid malicious damage, and achieve objectivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
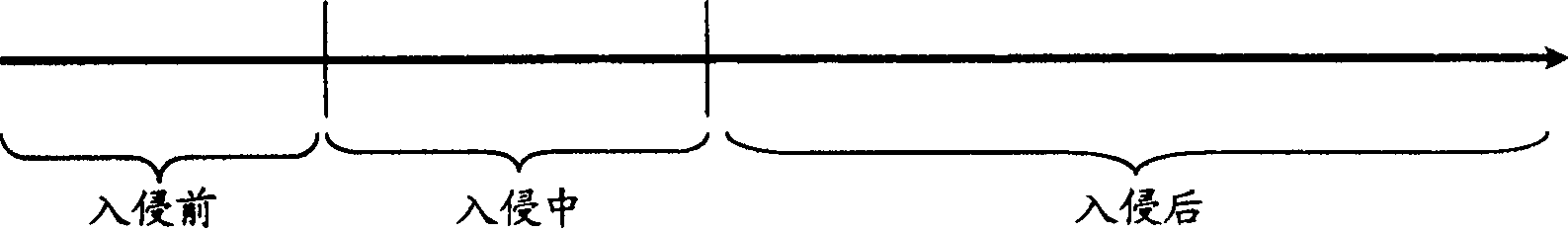
[0059] Such as Figure 1-4 As shown, the integrity verification of computer evidence is a key issue in computer evidence identification. One of the most difficult aspects of computer forensics is proving that the evidence collected by the forensic investigator has not been altered. figure 1 Describes the whole process of computer being invaded, which can be divided into three stages: before intrusion, during intrusion, and after intrusion. Among them, in the early stage of the invasion, the intruder first determines the attack target, and uses various scanning tools to remotely scan the target system to obtain the vulnerability of the target system and collect information for the next stage of successful intrusion; during the intrusion, the intruder According to the information collected in the first stage, various intrusion techniques or tools are used to successfully invade the target system; after the computer system is found to have been successfully invaded or is being i...
Embodiment 2
[0095] Test Effects of Forensic Information Integrity Protection Protocol
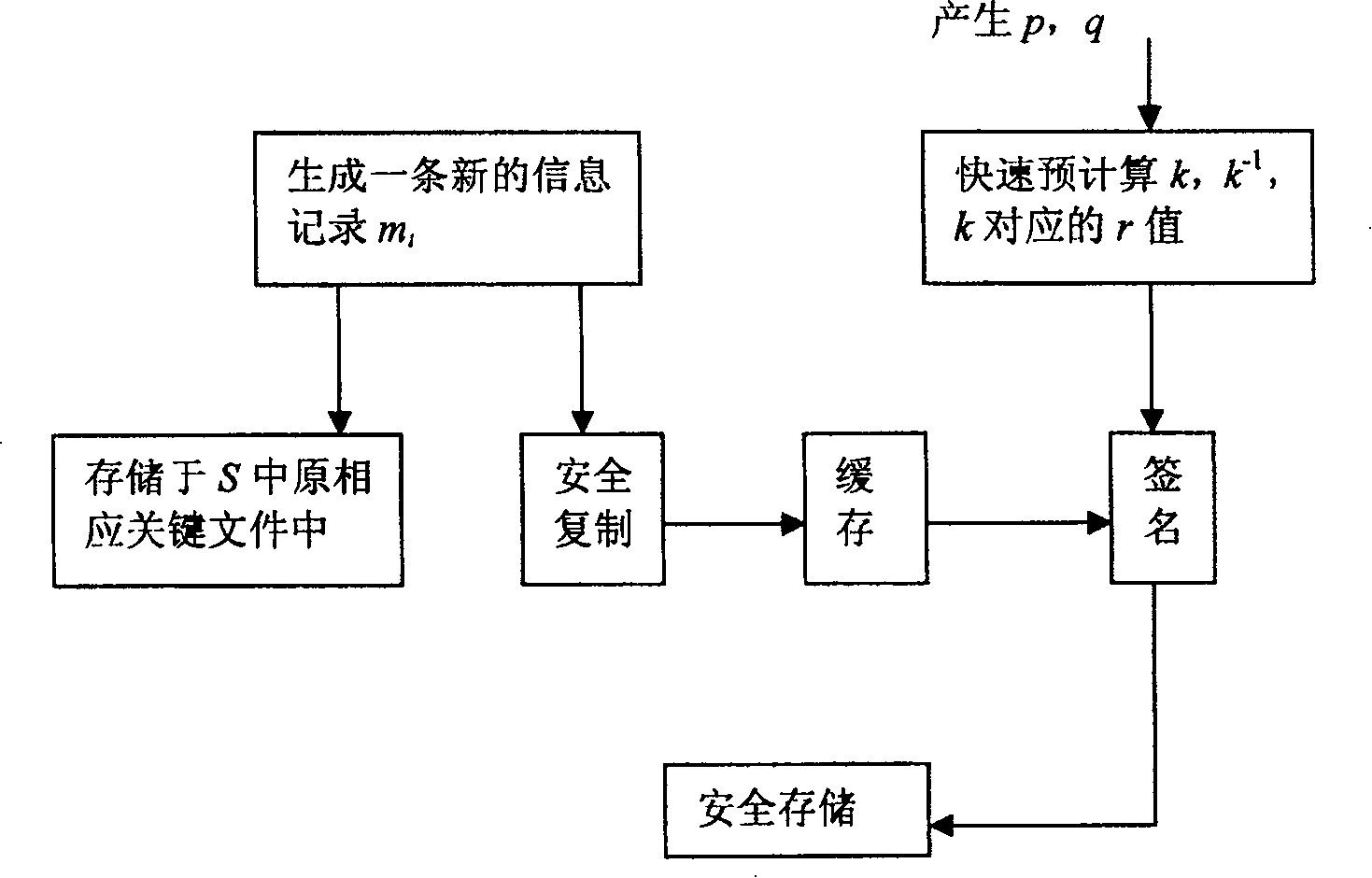
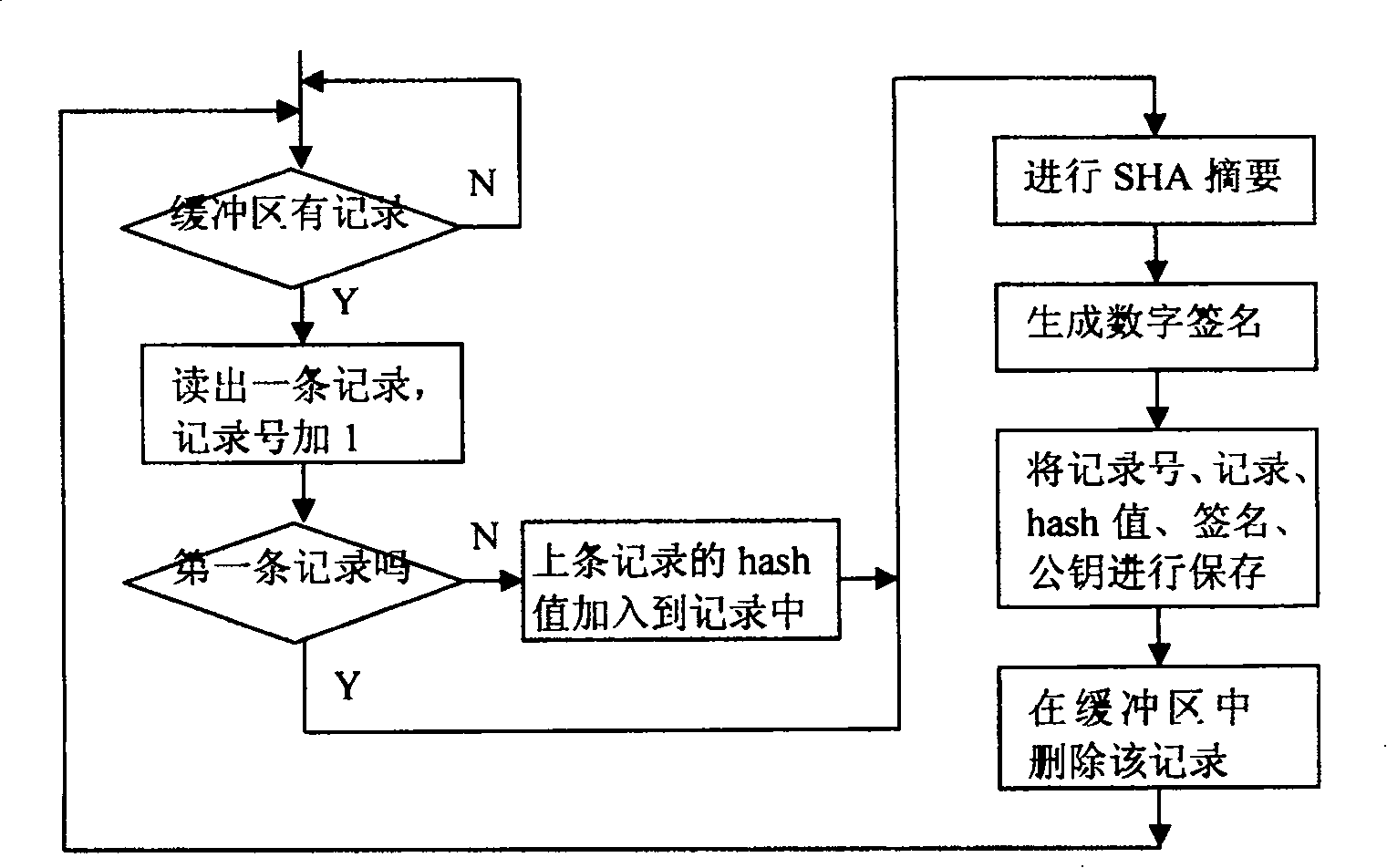
[0096] First carry out security signature and transfer (see embodiment 1) to the evidence collection information, its program testing process is as follows image 3 shown. The program loop first checks whether there is data to be signed in the buffer, and if so, reads out this record to determine whether it is the first record, if so, calculates its SHA digest, and then calculates its signature, if not, then Add the summary value obtained from the previous record to this information and then hash it, and finally save the information summary, and save this record and its summary, signature, public key and record number safely, and then retrieve the information from the buffer Delete this record.
[0097] Next, verify the information records that have been safely signed and saved. The program testing process is as follows: Figure 4 shown. The program reads the first row of data from the database, fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com