Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
50 results about "Rewrite rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In linguistics, a rewrite rule for natural language in generative grammar is a rule of the form A → X where A is a syntactic category label, such as noun phrase or sentence, and X is a sequence of such labels and/or morphemes, expressing the fact that A can be replaced by X in generating the constituent structure of a sentence. Example: S → NP VP Which means: Sentence consists of Noun Phrase followed by Verb Phrase. Rewrite rules underlie rewriting systems; there are many different varieties of rewriting systems that are commonly studied.
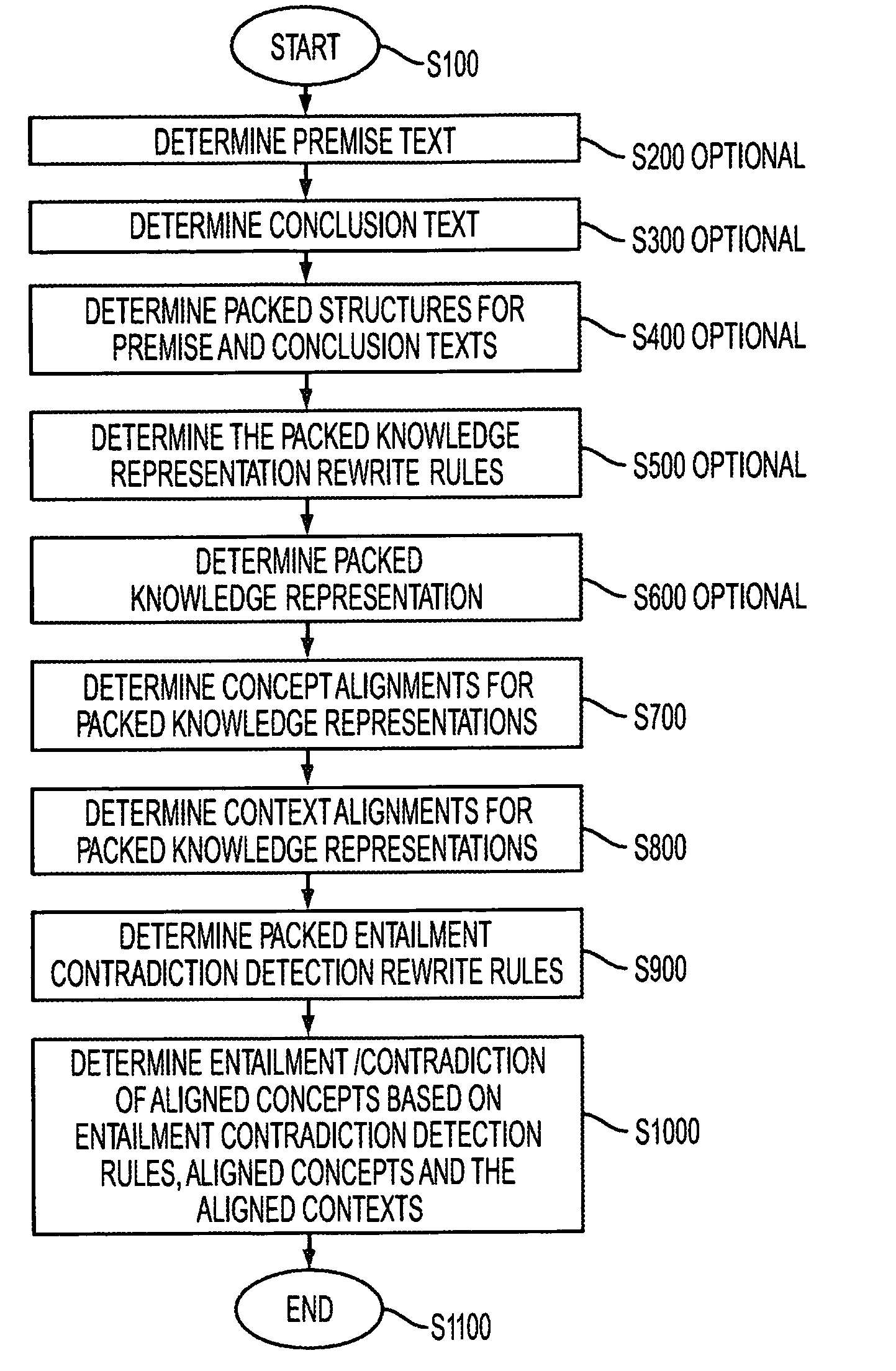
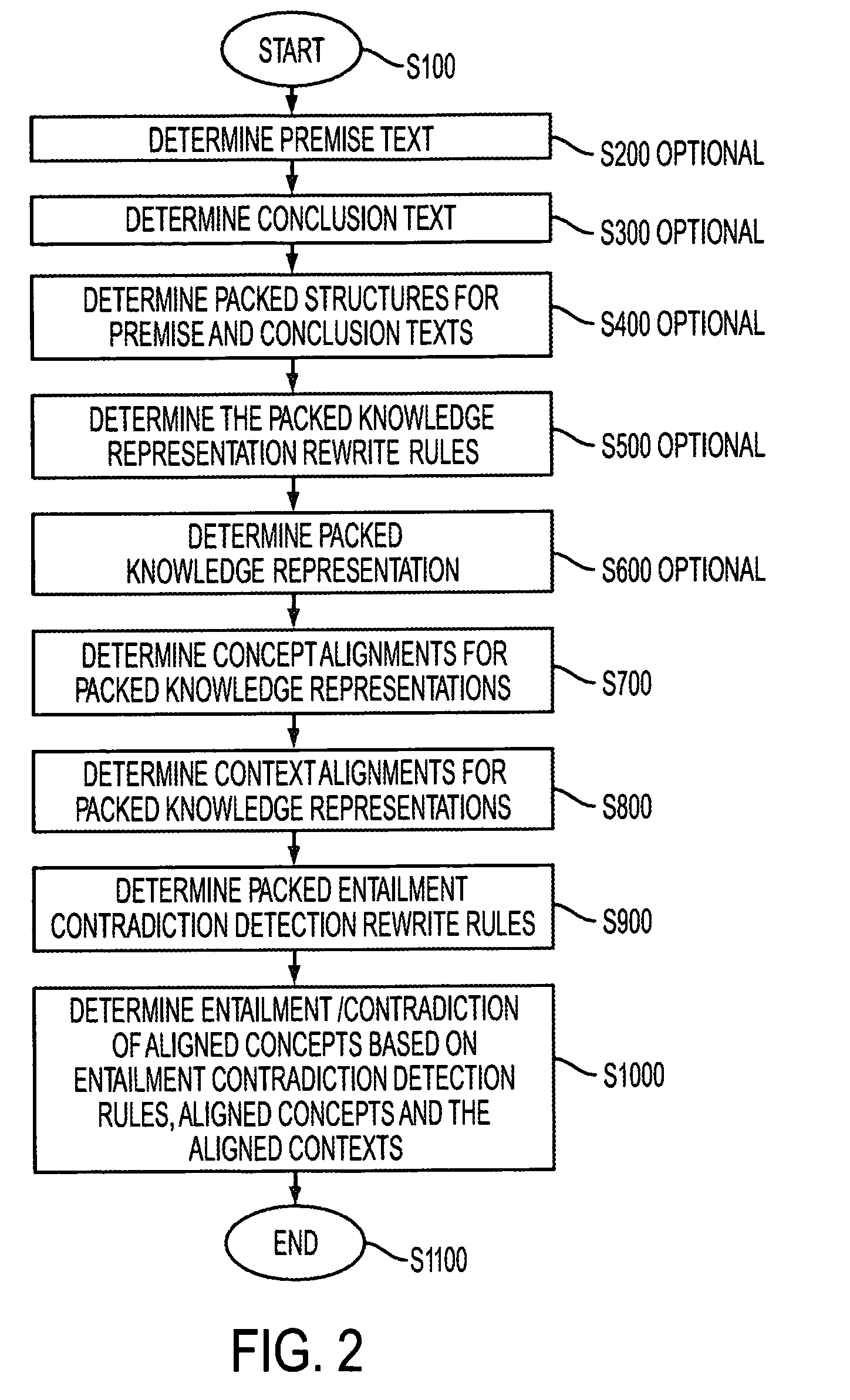
Systems and methods for detecting entailment and contradiction
InactiveUS7313515B2Knowledge representationSpecial data processing applicationsAlgorithmRewrite rule
Owner:PALO ALTO RES CENT INC
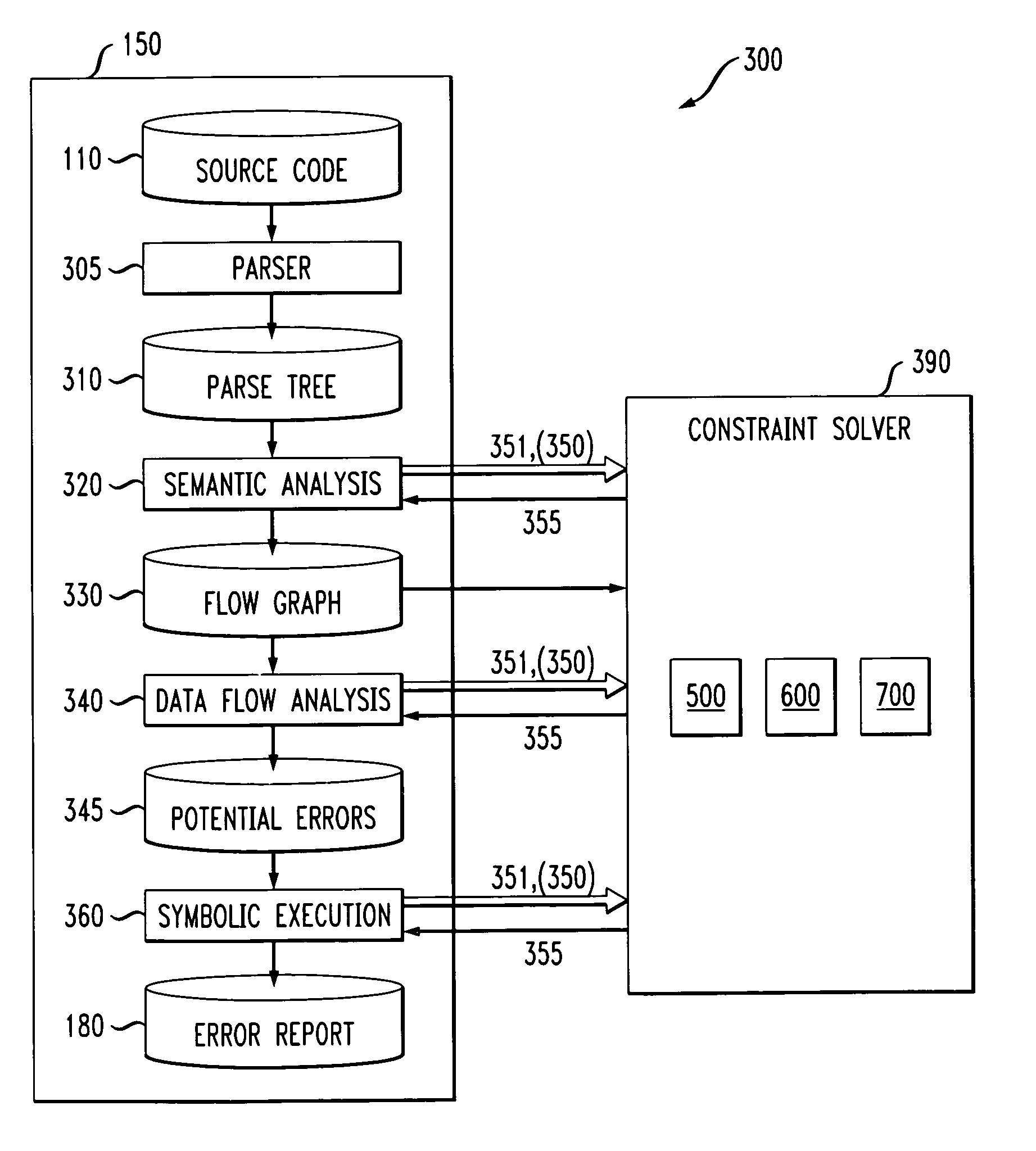
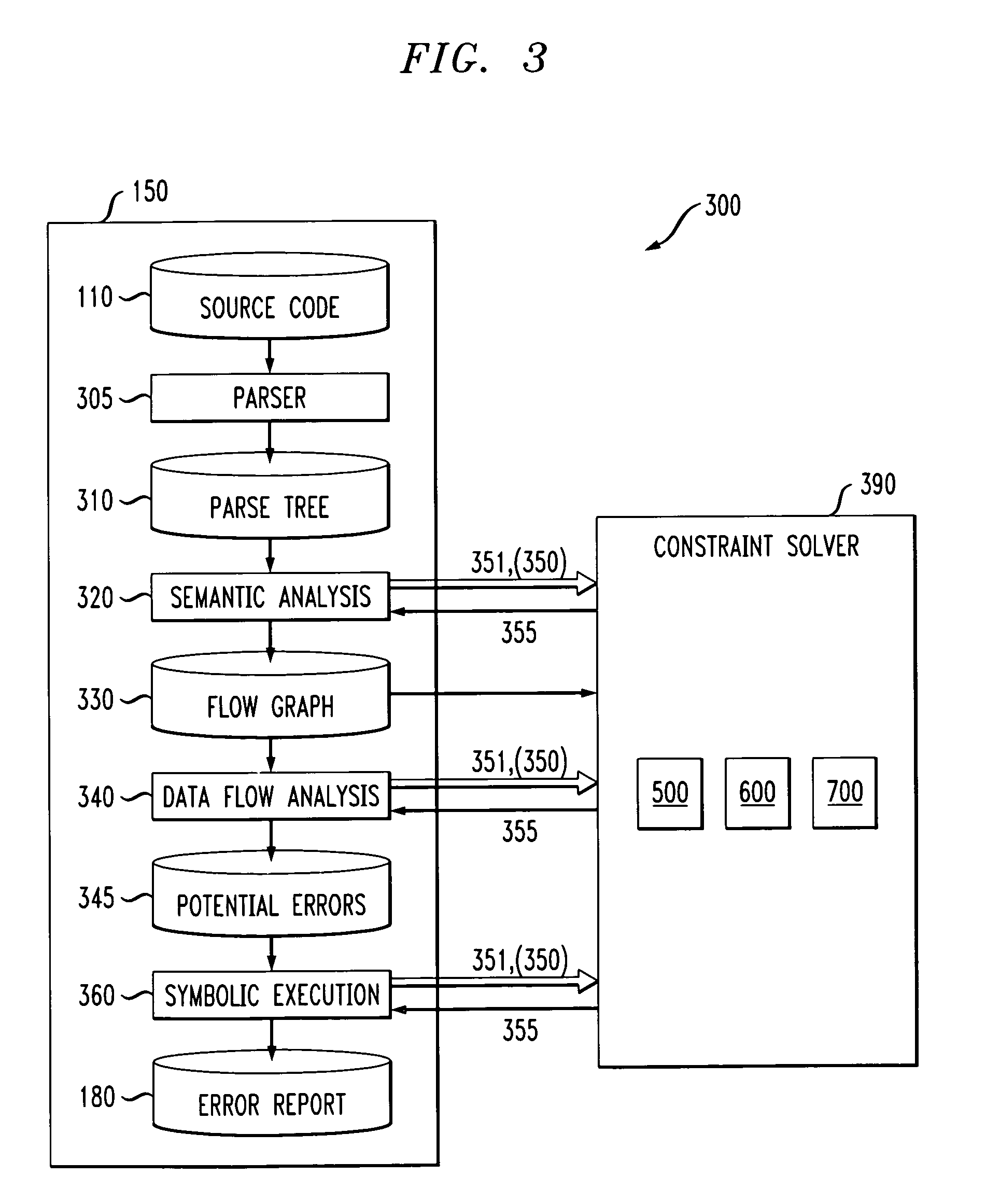
Method and apparatus for finding errors in software programs using satisfiability of constraints
InactiveUS7089542B2Efficient and accurateHandled satisfactorilyError preventionError detection/correctionRewrite ruleSemantics
A method and apparatus are provided for analyzing software programs. The invention combines data flow analysis and symbolic execution with a new constraint solver to create a more efficient and accurate static software analysis tool. The disclosed constraint solver combines rewrite rules with arithmetic constraint solving to provide a constraint solver that is efficient, flexible and capable of satisfactorily expressing semantics and handling arithmetic constraints. The disclosed constraint solver comprises a number of data structures to remember existing range, equivalence and inequality constraints and incrementally add new constraints. The constraint solver returns an inconsistent indication only if the range constraints, equivalence constraints, and inequality constraints are mutually inconsistent.
Owner:IBM CORP
Systems and methods for detecting entailment and contradiction
InactiveUS20070255555A1Knowledge representationSpecial data processing applicationsRewrite ruleSpacetime
Owner:PALO ALTO RES CENT INC
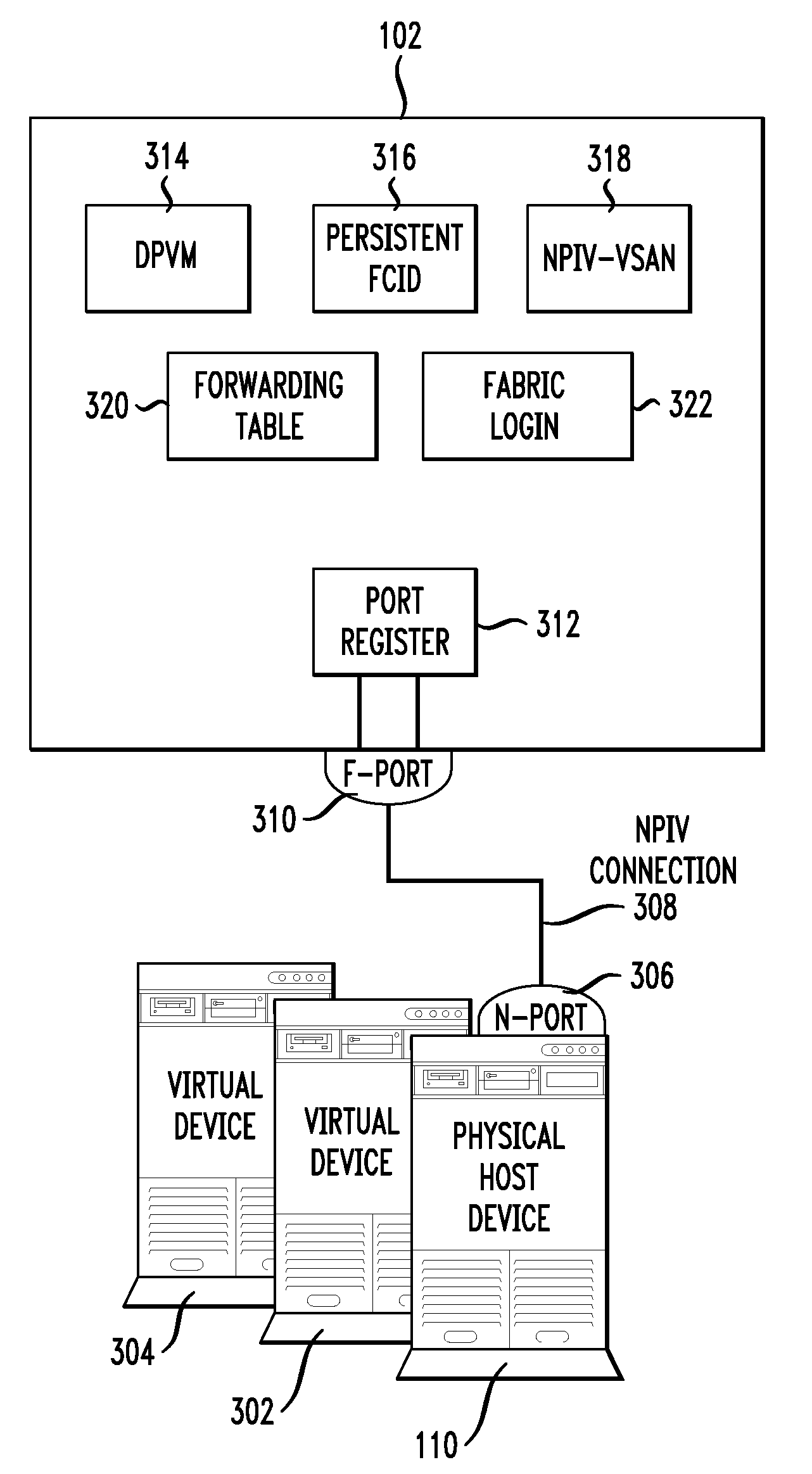
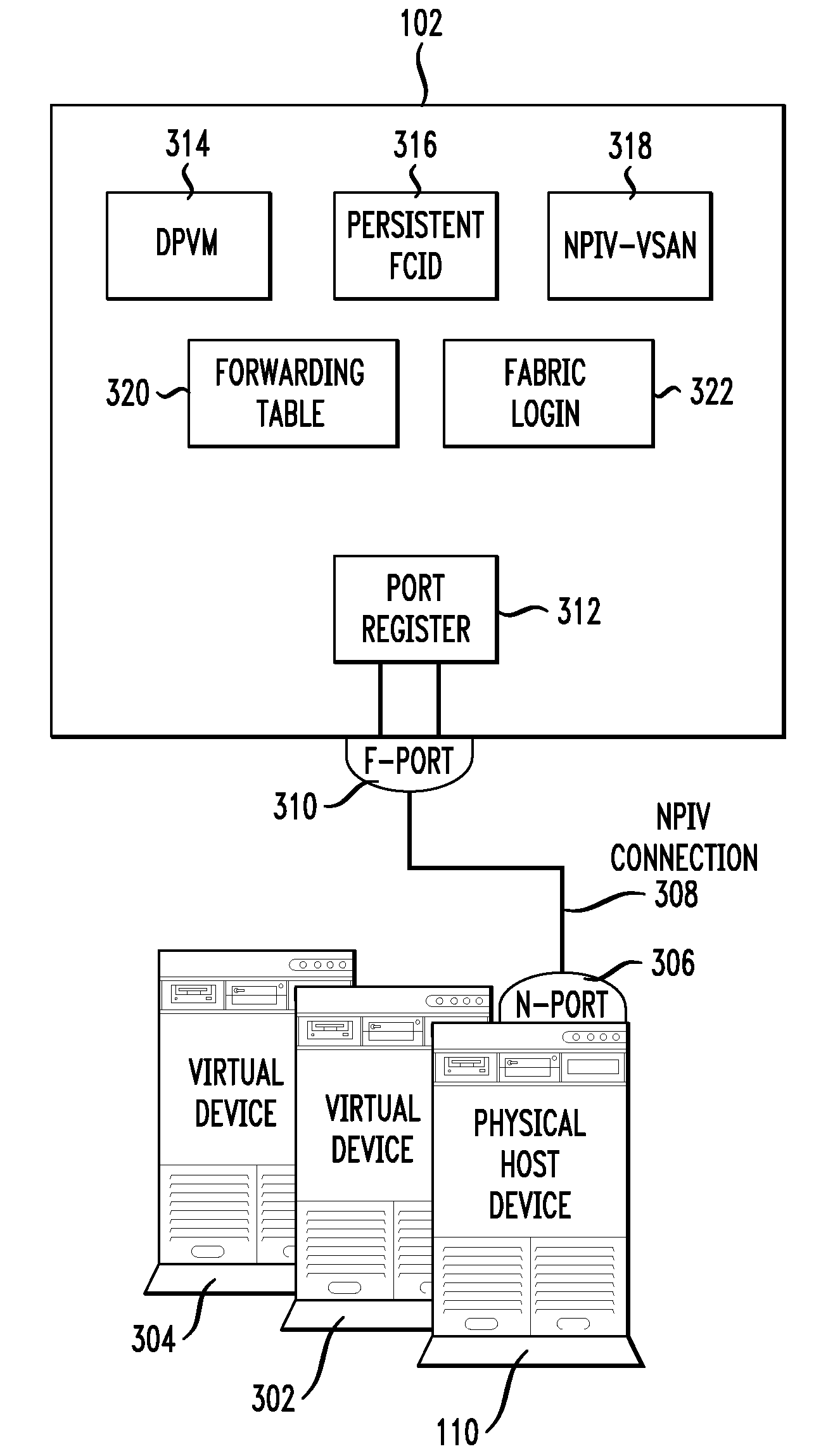
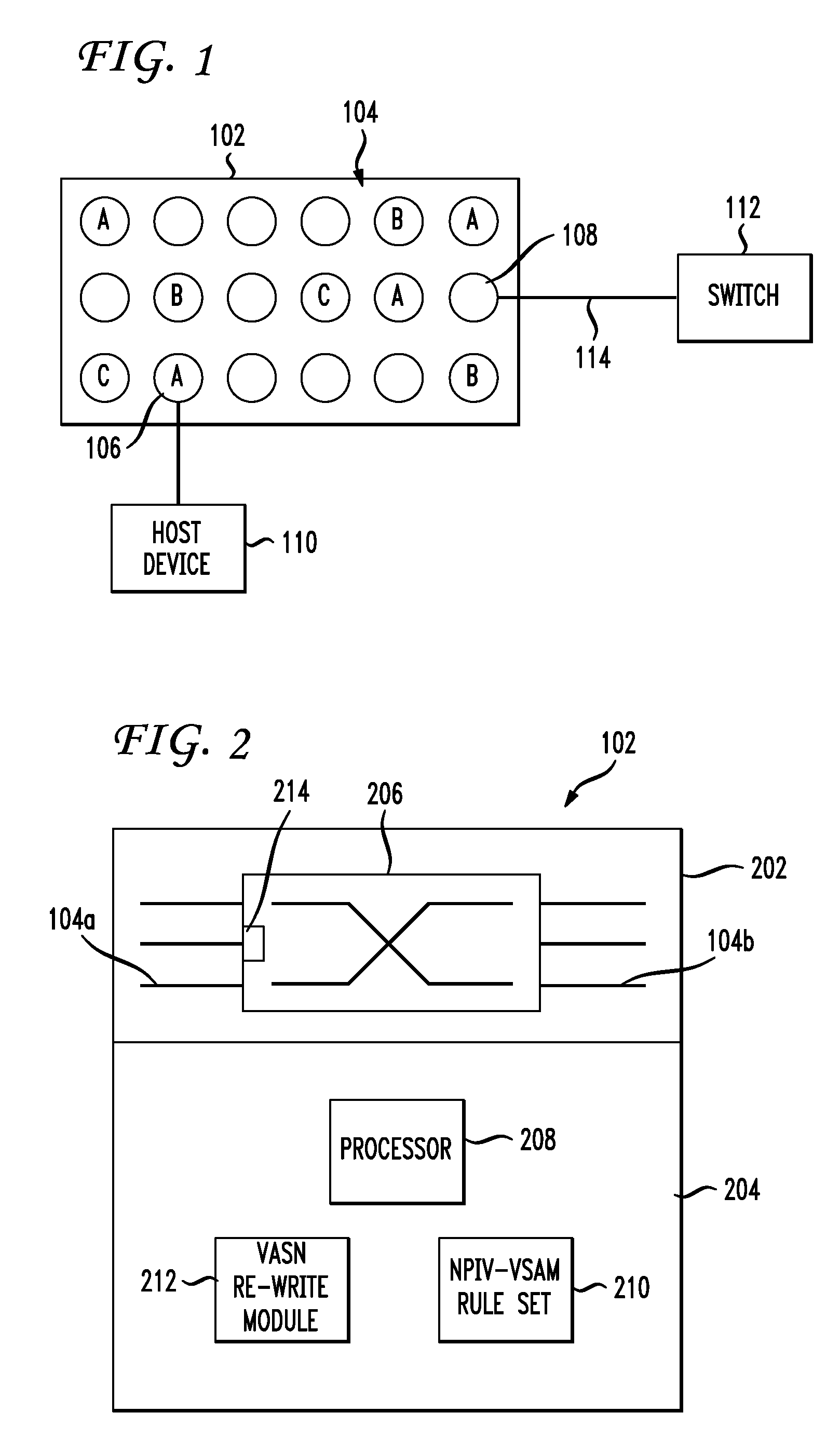
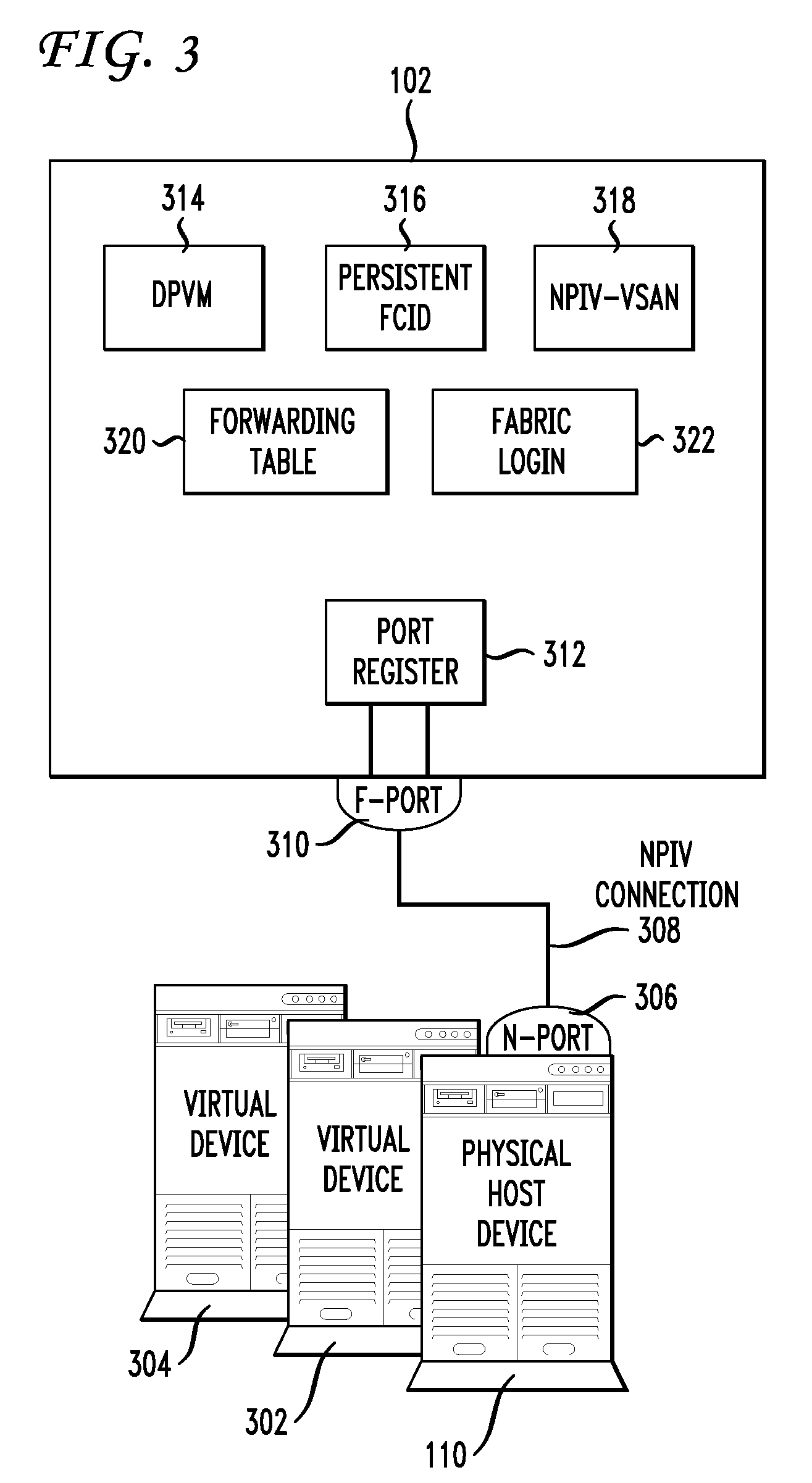
Switch with virtual network identifier re-write capability
A switch includes a processor, an ingress port having ingress port logic, and an egress port. It may also include a virtual network identifier rewrite component for rewriting a virtual network identifier in a data frame received the ingress port with a new virtual network identifier. Also included is a virtual network identifier rewrite rule set, where a rule may have one or more of the following: a received virtual network identifier, a source Fibre Channel identifier (FCID) address, an ingress port identifier, and a new virtual network identifier. The ingress port logic may insert a received virtual network identifier into the data frame received at the ingress port, where the virtual network identifier may correspond to the ingress port. The virtual network identifier rewrite component may assign the new virtual network identifier to the data frame according to a specific virtual network identifier rewrite rule.
Owner:CISCO TECH INC
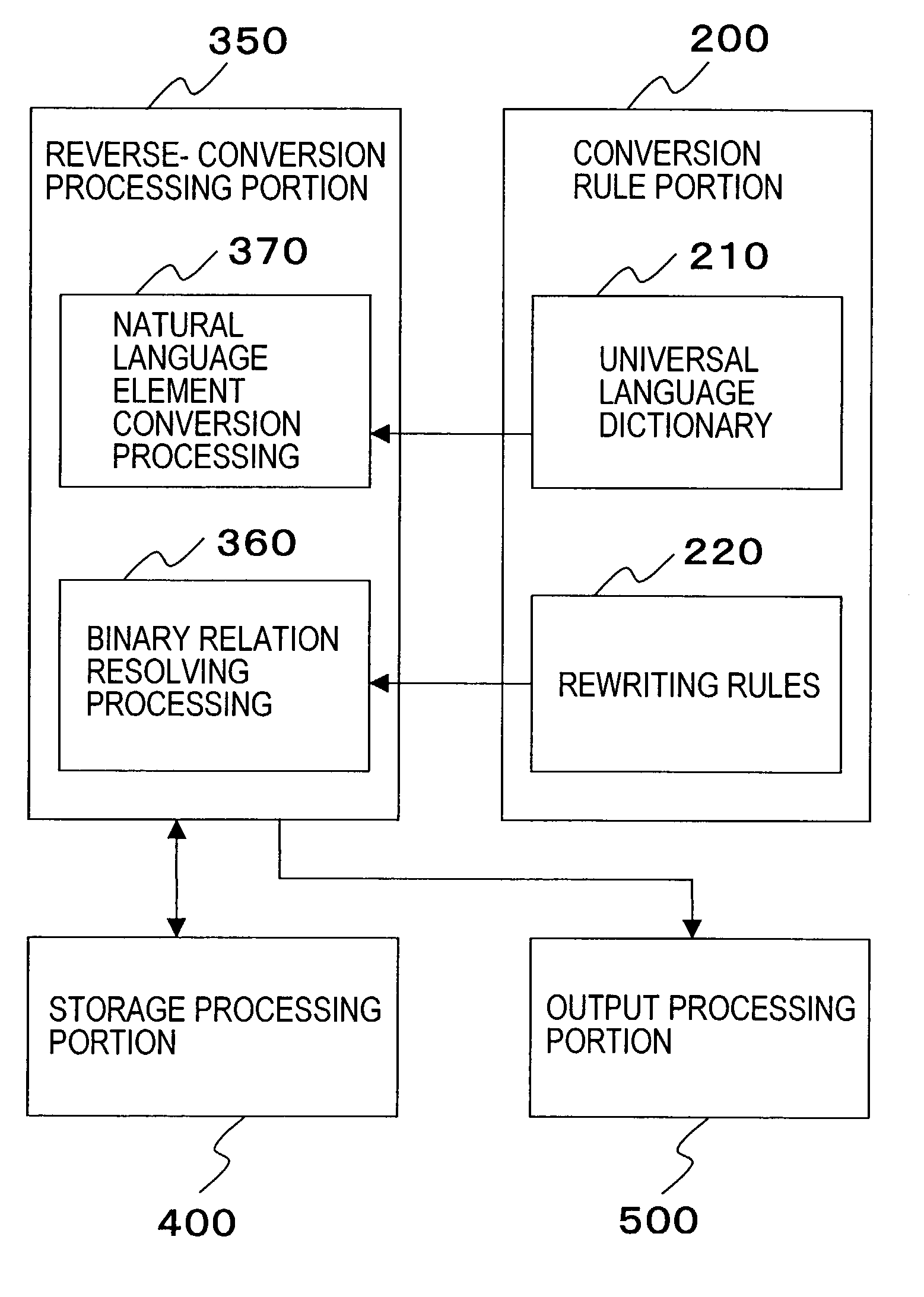
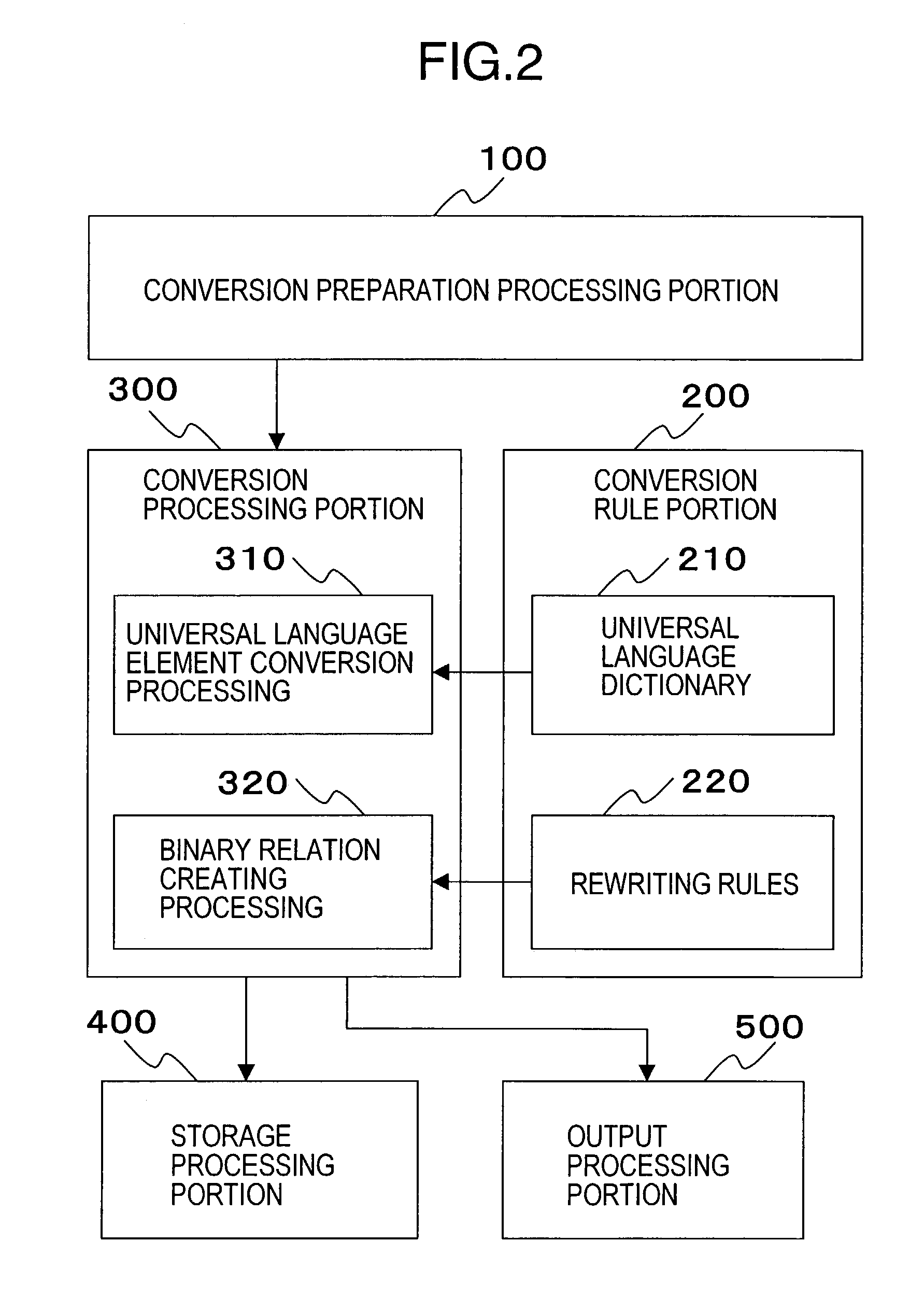
Language conversion system
InactiveUS7107206B1Low costNatural language translationSpecial data processing applicationsRewrite ruleGeneral-purpose language
A system is disclosed which allows communication between various kinds of languages. The conversion processing portion (300) rewrites components of the representation in the natural language constructing given natural language representation to universal language elements corresponding thereto in the universal language dictionary (210). The conversion processing portion (300) joins multiple rewritten universal language elements by applying the rewriting rules (220) in accordance with an order in universal language element and creates representation in universal language, which is represented in the binary relation. A reverse-conversion processing portion (350) resolves representation in universal language represented in the binary relation to universal language elements constructing joins therein with reference to the rewriting rules (220) in accordance with rules for representation in the binary relation, which are included in the rules. The reverse-conversion processing portion (350) rewrites the resolved universal language elements to components constructing the natural language representation with reference to the universal language dictionary (120) in order to create representation in natural language.
Owner:UNITED NATIONS
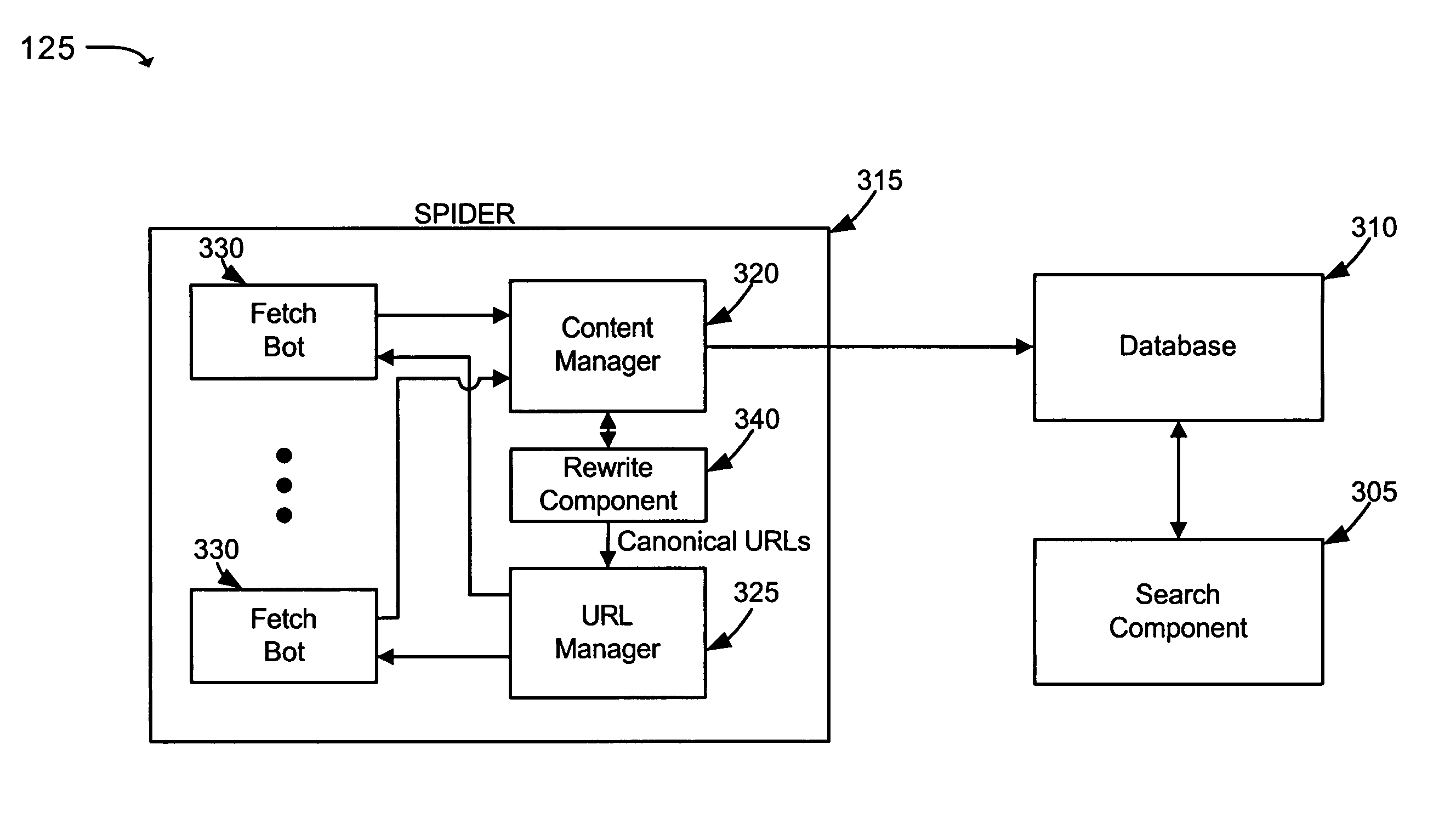
Automatic generation of rewrite rules for URLs
ActiveUS7827254B1Reduce in quantityWeb data indexingMultiple digital computer combinationsRewrite ruleUniform resource locator
A rewrite component automatically generates rewrite rules that describe how uniform resource locators (URLs) can be rewritten to reduce or eliminate different URLs that redundantly refer to the same or substantially the same content. The rewrite rules can be applied to URLs received when crawling a network to increase the efficiency of the crawl and the corresponding document index generated from the crawl.
Owner:GOOGLE LLC
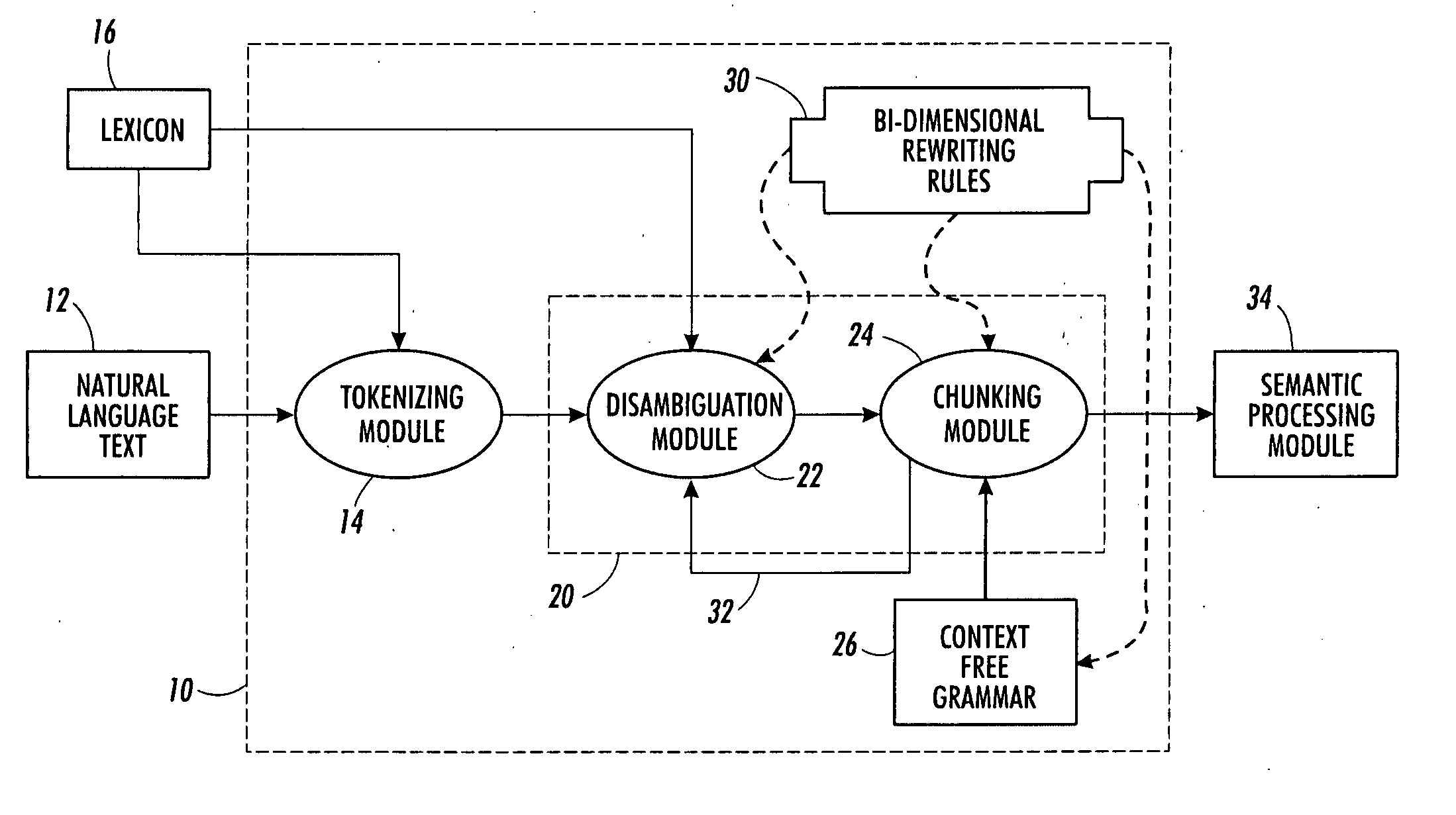
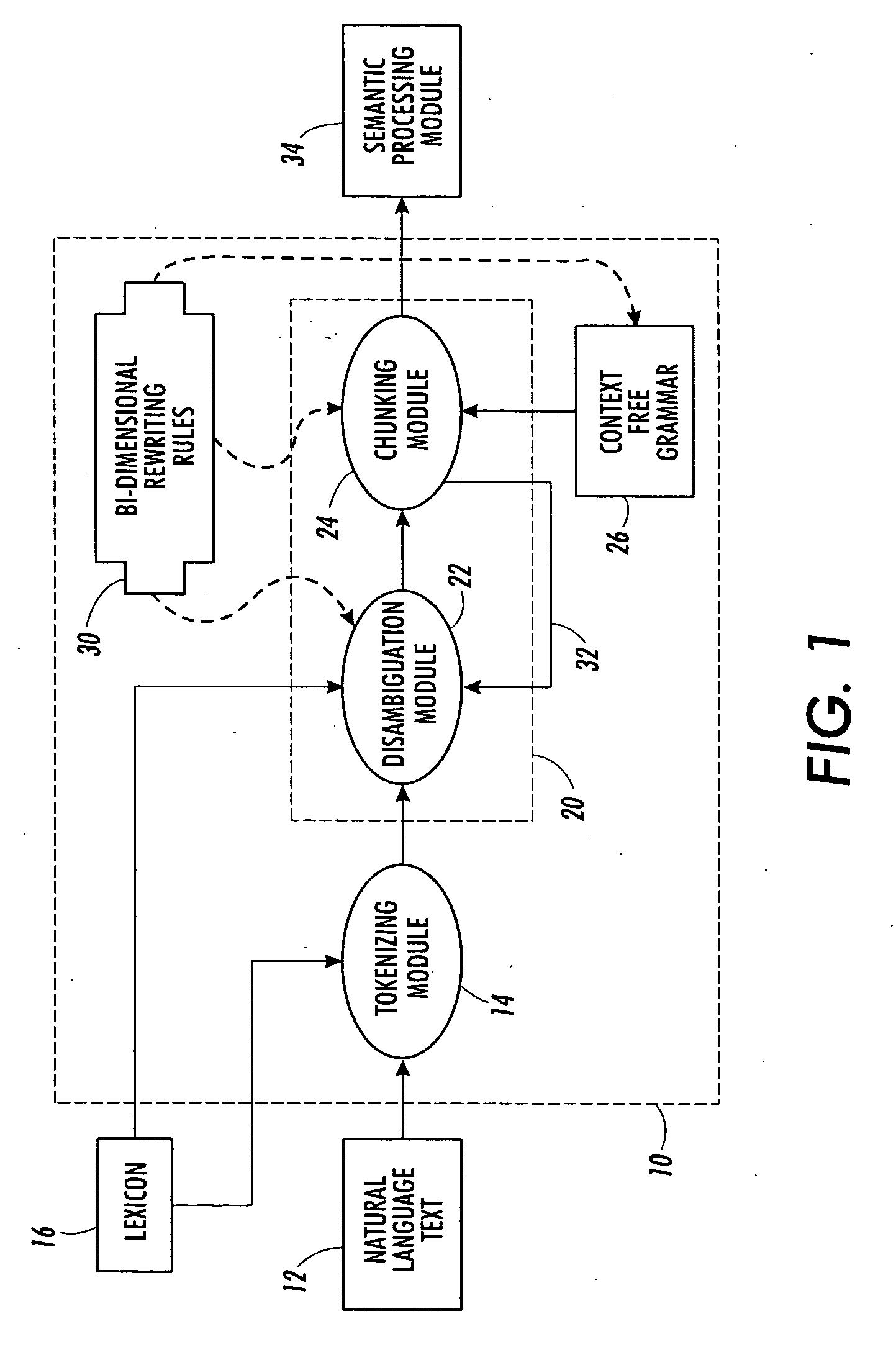
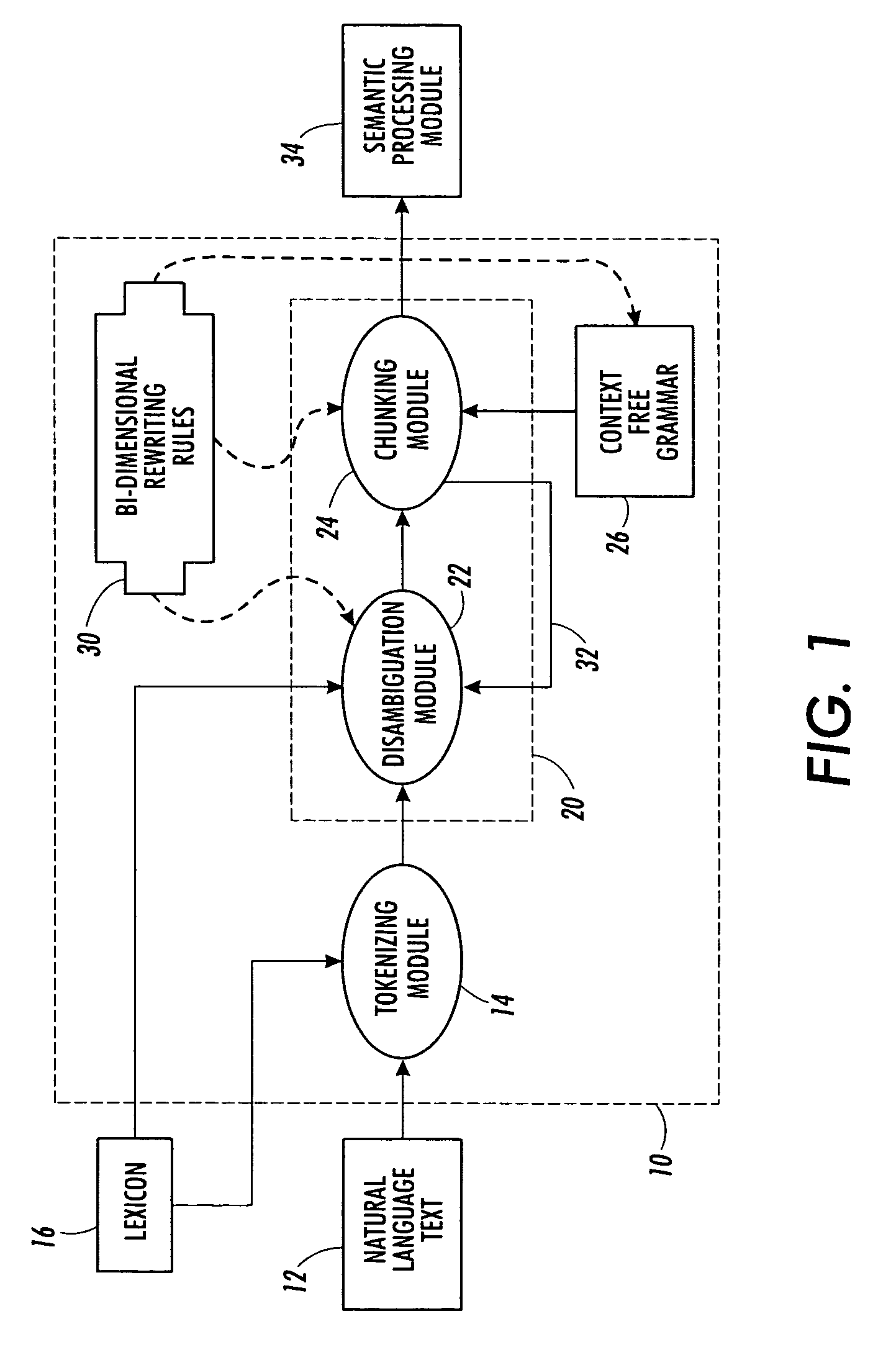
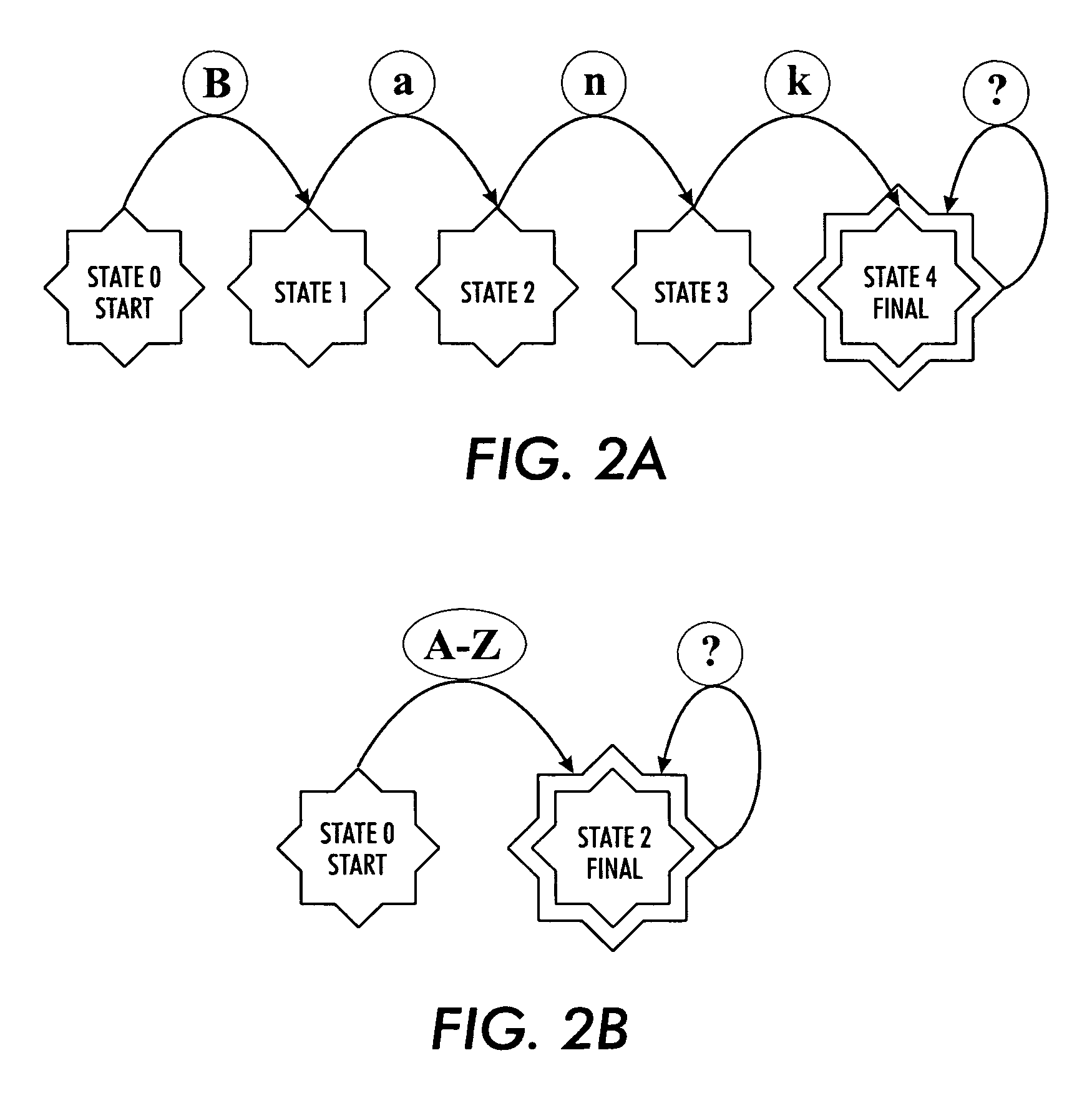
Bi-dimensional rewriting rules for natural language processing
InactiveUS20060136196A1Digital data processing detailsNatural language data processingPattern matchingRewrite rule
A linguistic rewriting rule for use in linguistic processing of an ordered sequence of linguistic tokens includes a token pattern recognition rule that matches the ordered sequence of linguistic tokens with a syntactical pattern. The token pattern recognition rule incorporates a character pattern recognition rule to match characters contained in an ambiguous portion of the ordered sequence of linguistic tokens with a character pattern defining a corresponding portion of the syntactical pattern.
Owner:XEROX CORP
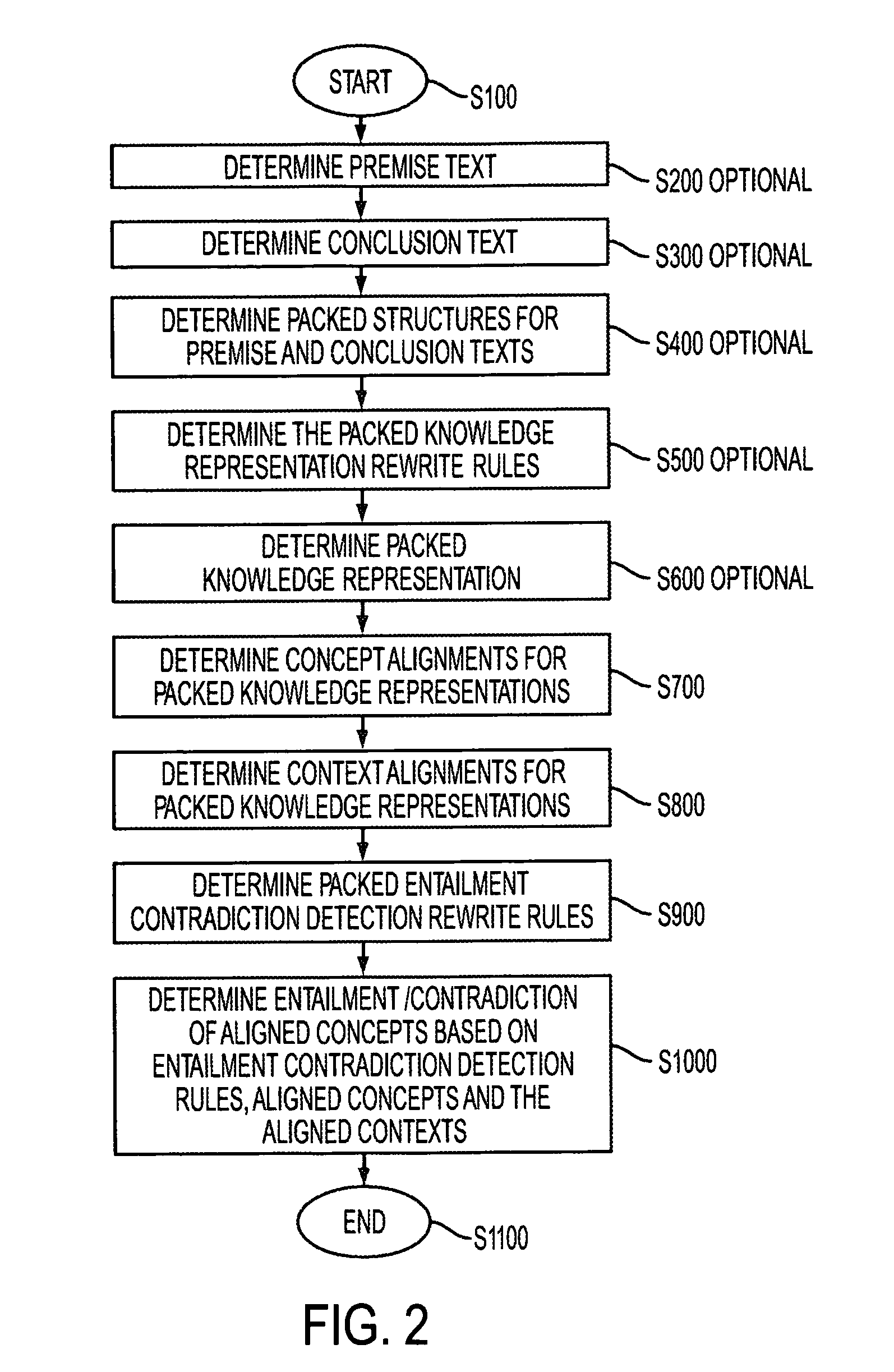
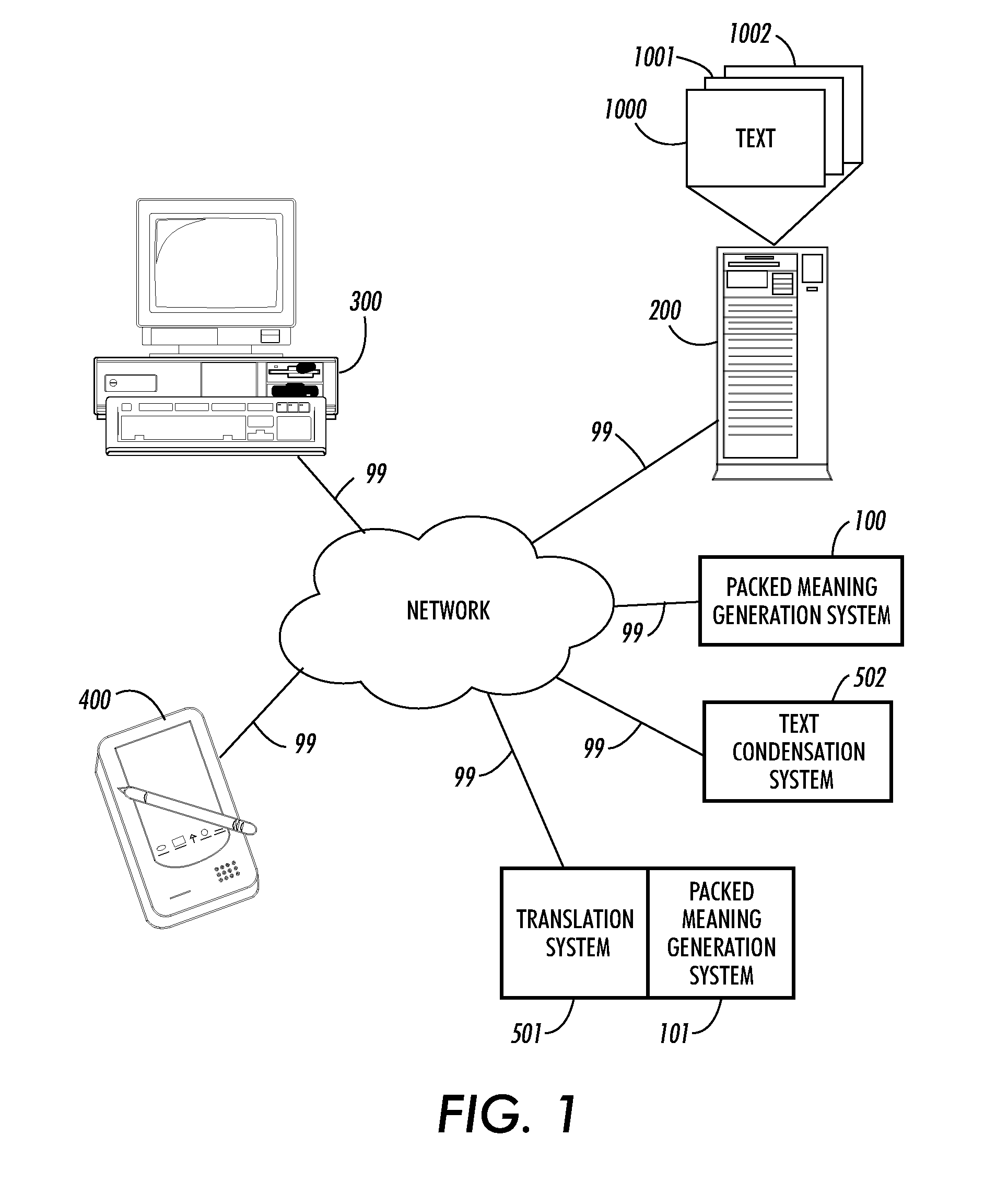
Systems and methods for the generation of alternate phrases from packed meaning
ActiveUS20050137855A1Natural language translationSpecial data processing applicationsSemanticsRewrite rule
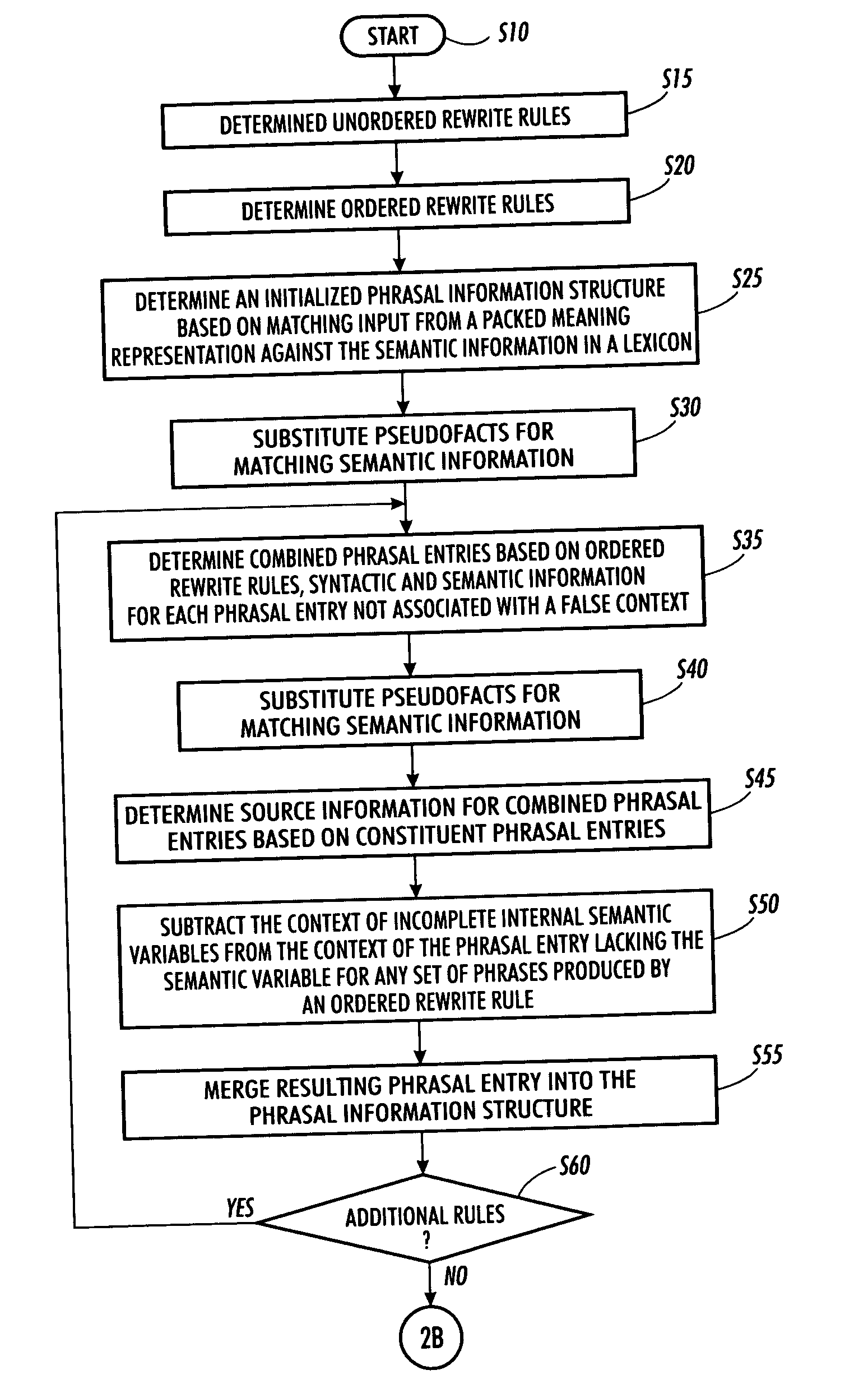
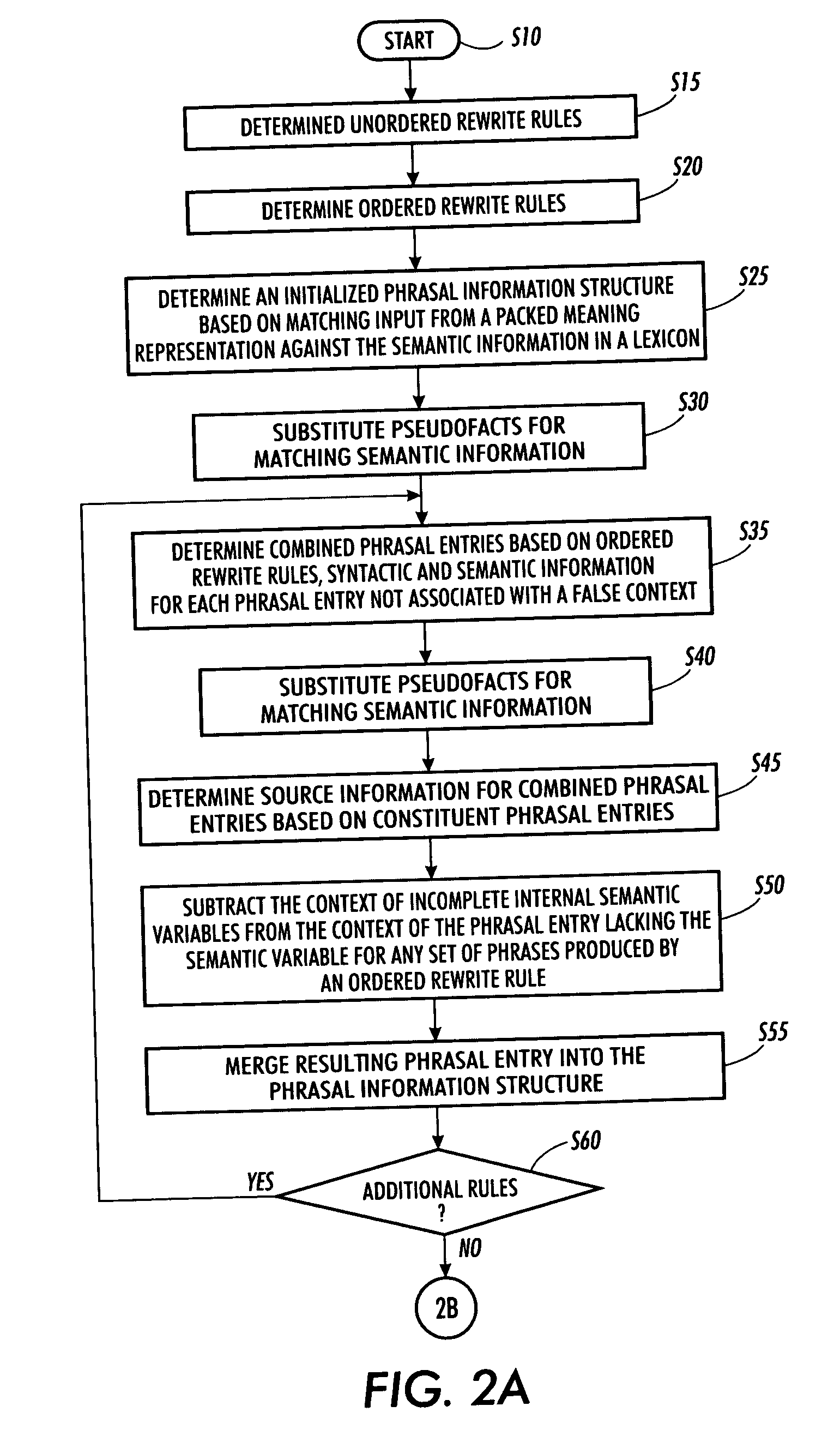
Techniques are provided to generate alternate phrases from a packed meaning representation. The semantics of input items in a packed meaning representation are matched against a lexicon to determine initial entries in a phrasal information structure. Context, syntax and semantic information describing each phrasal entry are added to the phrasal information structure. Linear or other implications are used to determine a set of unordered rewrite rules. The unordered rewrite rules associate semantic information with pseudofacts such that a complete set of choices from the set of disjunctions in the packed meaning representation is selected. Semantic information associated with the unordered rewrite rules identifies entries in the phrasal information structure to be updated with the pseudofact of the unordered rewrite rule; Entries in the phrasal information structure not associated with false contexts are combined based on ordered rewrite rules. The ordered rewrite rules are based on the language of the packed meaning representation. Source information associated with each new entry in the phrasal information structure reflects the phrasal entry identifiers of the entries used to determine the new entry. For any set of entries in the phrasal information structure produced by an ordered rewrite rule, the context of a missing semantic fact is subtracted from the context of the entry lacking the semantic fact. Entries associated with a false context are discarded and entries sharing the same syntax and semantic information are merged. Any entries in the phrasal information structure associated with the “ALL” pseudofact are then determined. Alternate phrases are generated based on the source information for the entry in the phrasal information structure associated with the “ALL” pseudofact.
Owner:XEROX CORP
Automatic designing system, automatic designing method and automatic designing program for automatically designing architecture for system components
InactiveUS20100332444A1Efficient reuseSimple methodGeometric CADDigital data processing detailsGraphicsAlgorithm
Owner:IBM CORP
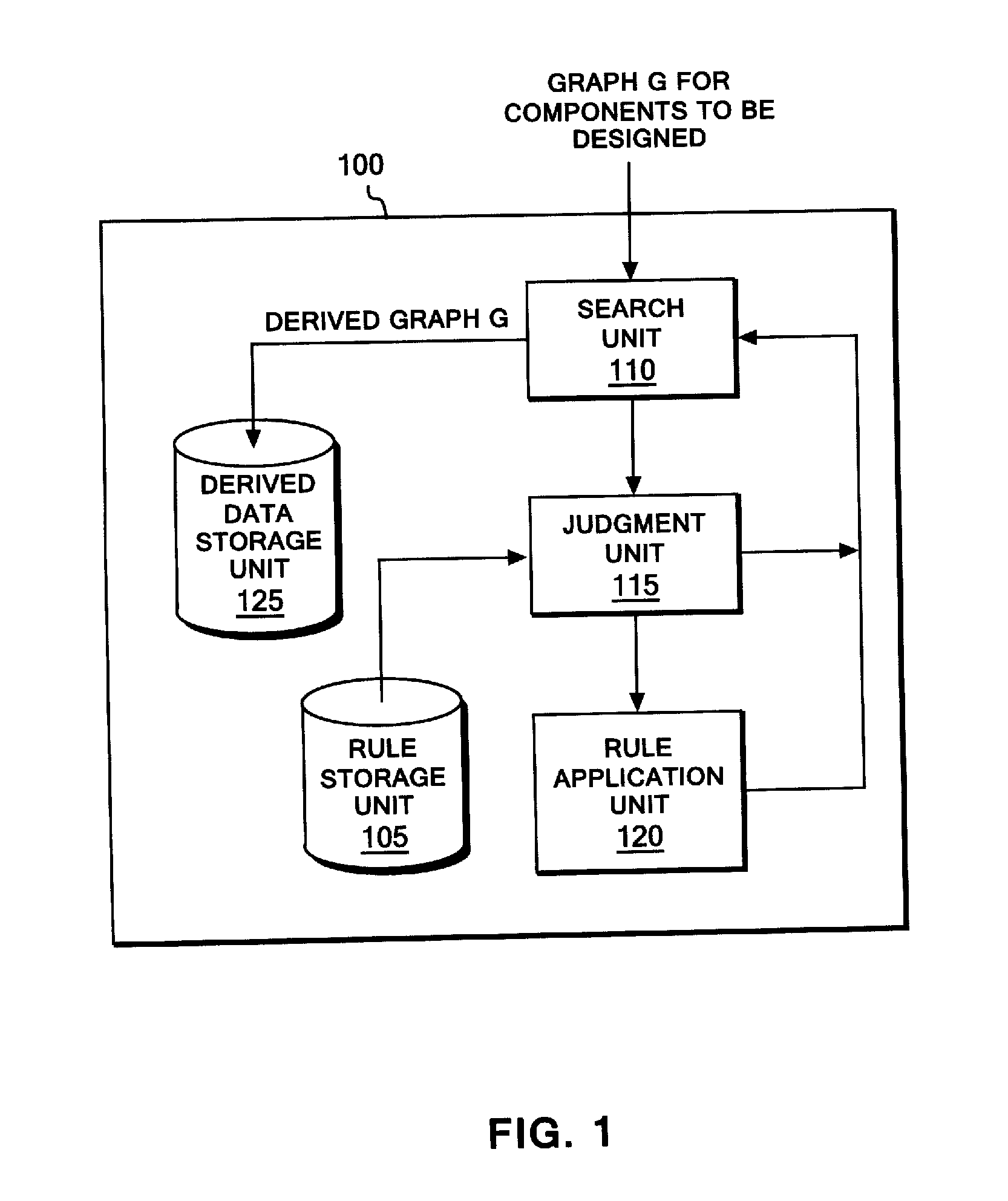
Use of a directed acyclic organization structure for selection and execution of consistent subsets of rewrite rules
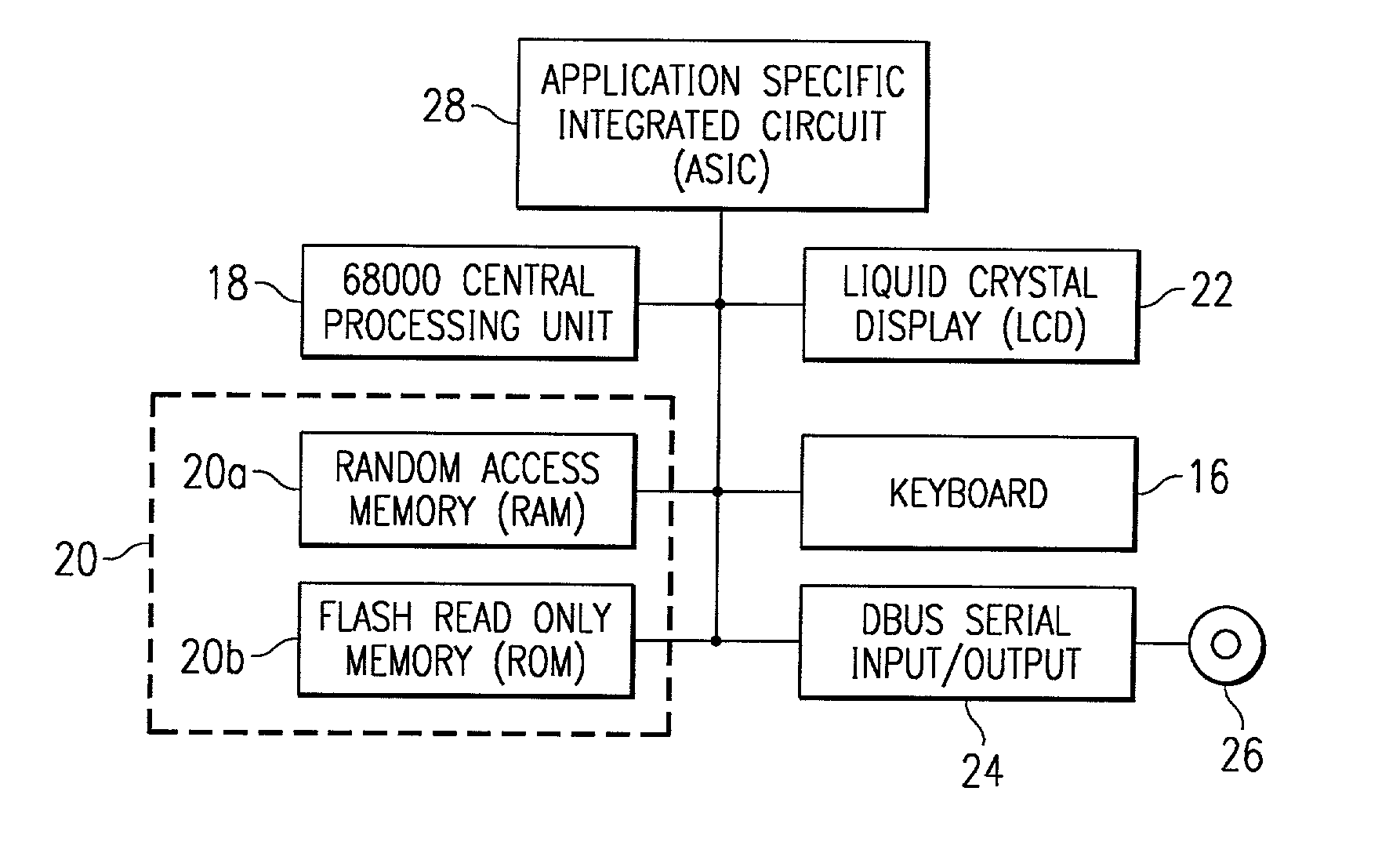
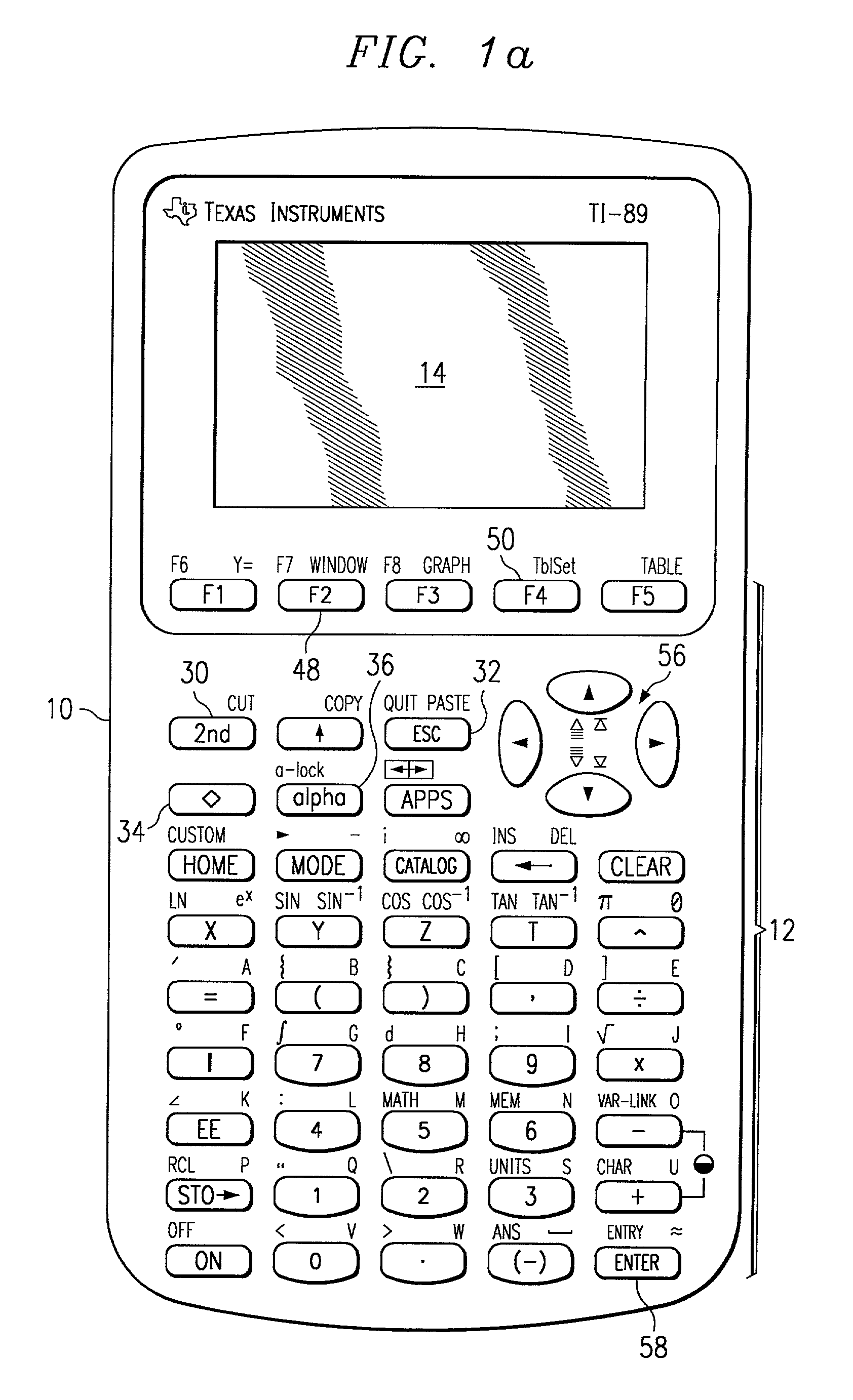
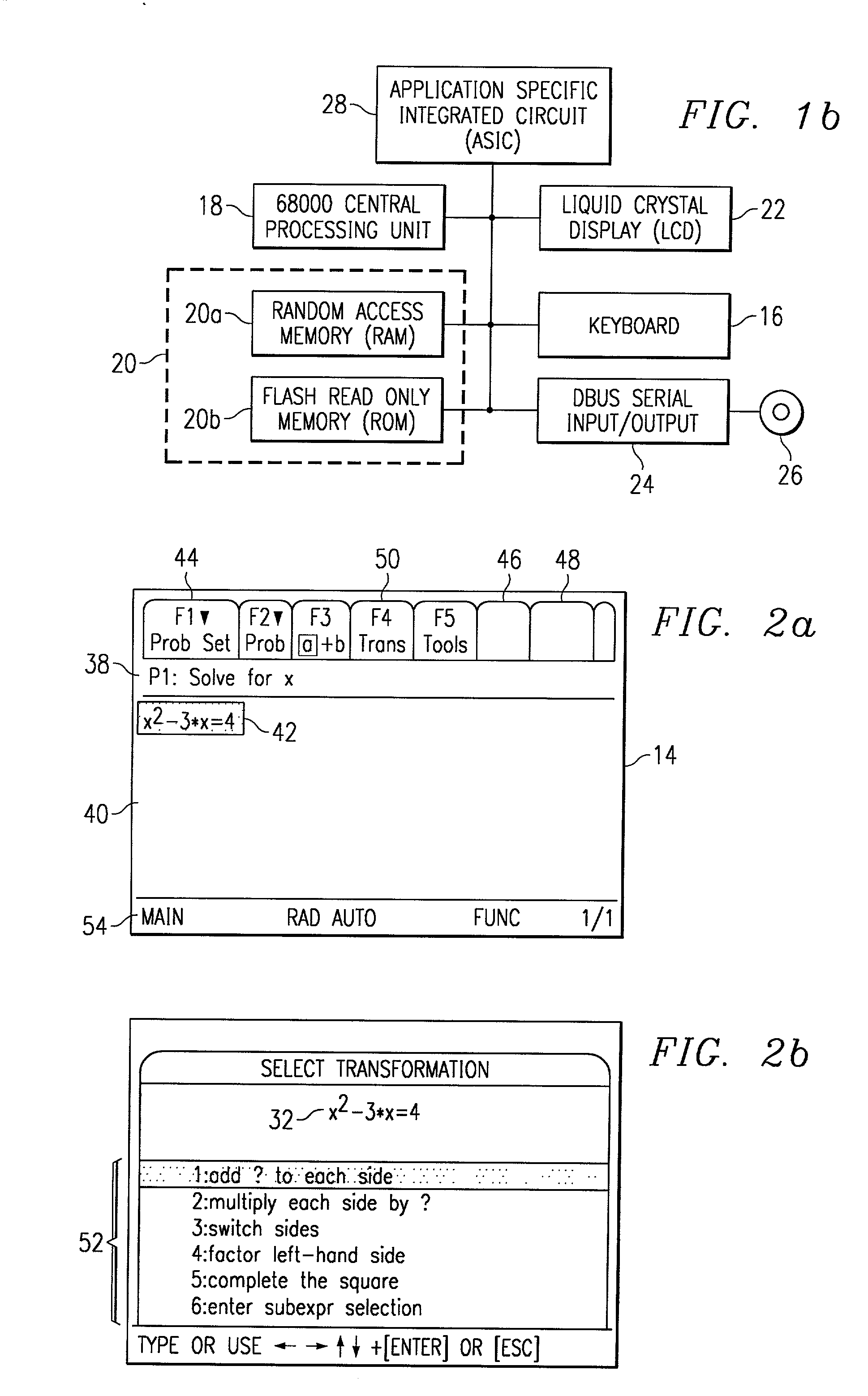
The present invention discloses the use of a hand-held calculator programmed to teach subject matter such as mathematics in a manner that emulates traditional step-by-step teacher-student teaching methods and shows the important intermediate steps. The method evaluates a selected problem against a master set of possible operations, organized according to a hierarchy that can be applied to the problem and then provides choices of several operations that are applicable or can operate on a selected problem. Importantly, the choices available to the student will not always lead to a solution or simplification of the problem. This allows the student to see the effect of a good choice, as well as a poor choice. If the problem can be operated on further, the results of the previous operations have a new problem or expression to be solved. This repetitive process continues until there are no further operations possible that will move the problem closer to a final solution.
Owner:TEXAS INSTR INC
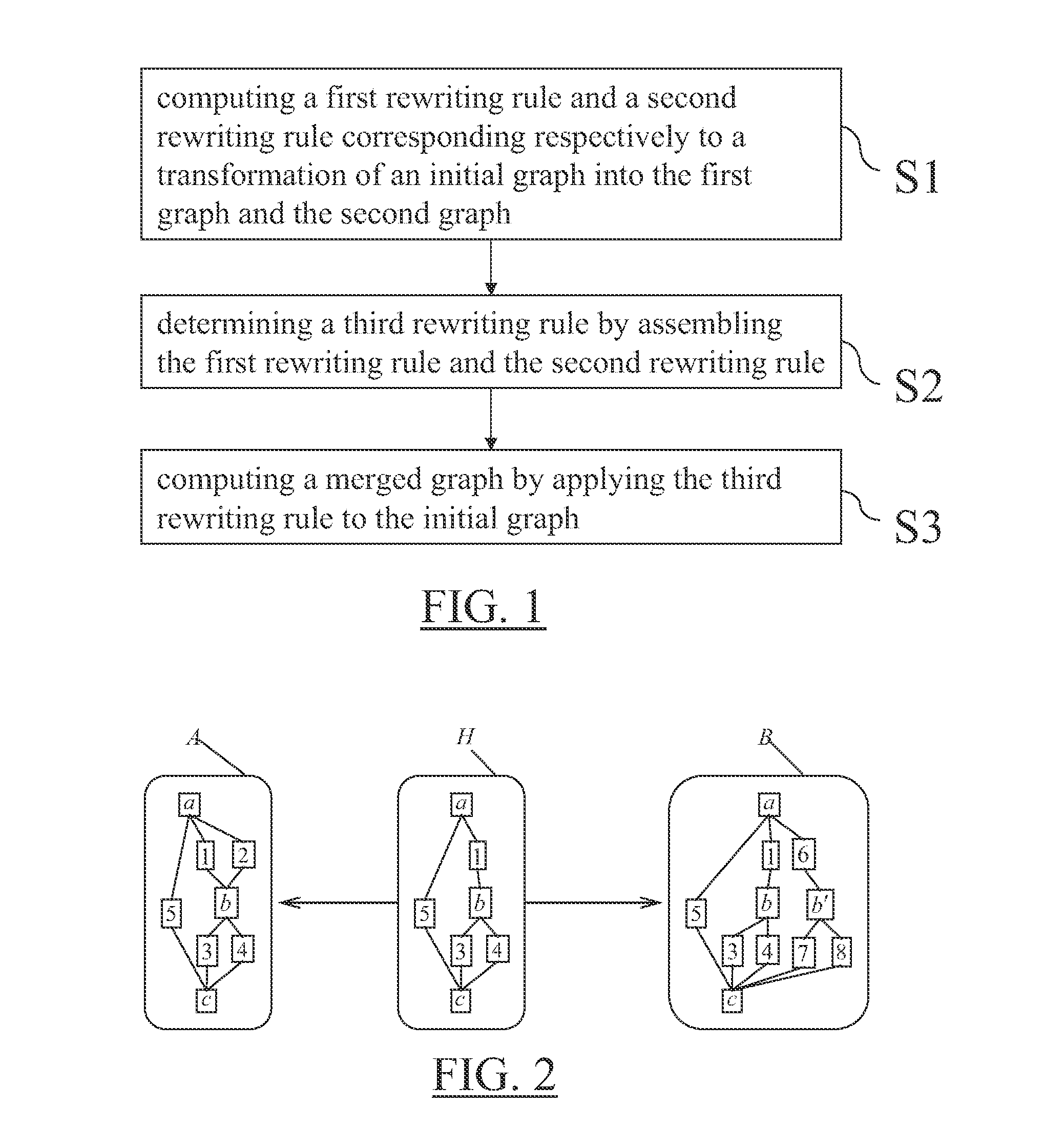
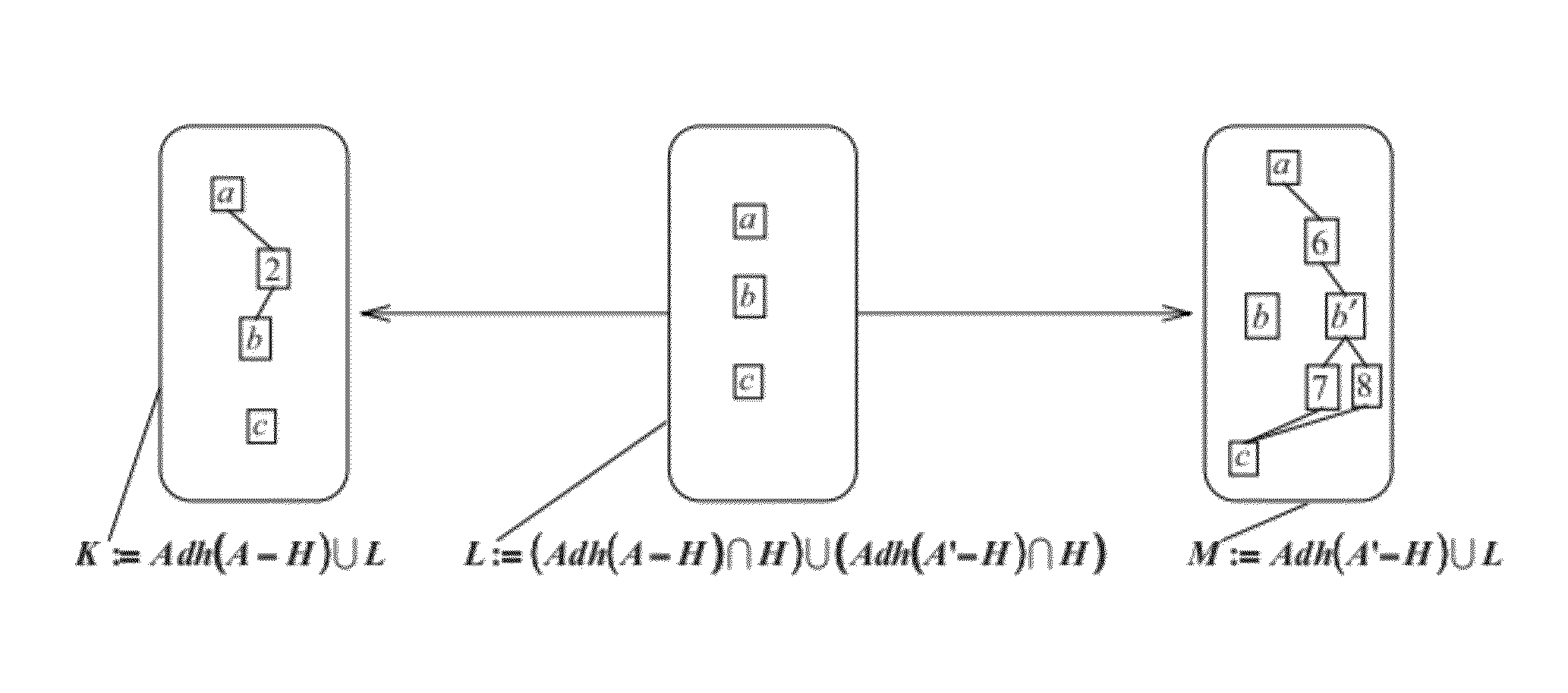
Merging of Modeled Objects
A computer-implemented method for merging a first and second modeled object which are modified versions of an initial modeled object and are defined by a first and second graphs. The method comprises merging the first graph and the second graph. For this, the method comprises computing a first rewriting rule and a second rewriting rule corresponding respectively to a transformation of an initial graph into the first graph and the second graph, determining a third rewriting rule by assembling the first rewriting rule and the second rewriting rule, and computing a merged graph by applying the third rewriting rule to the initial graph. Such a method is an improvement for the merging of modeled objects.
Owner:DASSAULT SYSTEMES
Bi-dimensional rewriting rules for natural language processing
InactiveUS7822597B2Digital data processing detailsNatural language data processingRewrite ruleSyntax
A linguistic rewriting rule for use in linguistic processing of an ordered sequence of linguistic tokens includes a token pattern recognition rule that matches the ordered sequence of linguistic tokens with a syntactical pattern. The token pattern recognition rule incorporates a character pattern recognition rule to match characters contained in an ambiguous portion of the ordered sequence of linguistic tokens with a character pattern defining a corresponding portion of the syntactical pattern.
Owner:XEROX CORP
Modeled object updating
ActiveUS20120173212A1CAD network environmentComputation using non-denominational number representationGraphicsRewrite rule
Owner:DASSAULT SYSTEMES
Switch with virtual network identifier re-write capability
A switch includes a processor, an ingress port having ingress port logic, and an egress port. It may also include a virtual network identifier rewrite component for rewriting a virtual network identifier in a data frame received the ingress port with a new virtual network identifier. Also included is a virtual network identifier rewrite rule set, where a rule may have one or more of the following: a received virtual network identifier, a source Fibre Channel identifier (FCID) address, an ingress port identifier, and a new virtual network identifier. The ingress port logic may insert a received virtual network identifier into the data frame received at the ingress port, where the virtual network identifier may correspond to the ingress port. The virtual network identifier rewrite component may assign the new virtual network identifier to the data frame according to a specific virtual network identifier rewrite rule.
Owner:CISCO TECH INC
Systems and methods for the generation of alternate phrases from packed meaning
InactiveUS20070250305A1Natural language translationSpecial data processing applicationsSemanticsRewrite rule
Techniques are provided to generate alternate phrases from a packed meaning representation. The semantics of input items in a packed meaning representation are matched against a lexicon to determine initial entries in a phrasal information structure. Context, syntax and semantic information describing each phrasal entry are added to the phrasal information structure. Linear or other implications are used to determine a set of unordered rewrite rules. The unordered rewrite rules associate semantic information with pseudofacts such that a complete set of choices from the set of disjunctions in the packed meaning representation is selected. Semantic information associated with the unordered rewrite rules identifies entries in the phrasal information structure to be updated with the pseudofact of the unordered rewrite rule; Entries in the phrasal information structure not associated with false contexts are combined based on ordered rewrite rules. The ordered rewrite rules are based on the language of the packed meaning representation. Source information associated with each new entry in the phrasal information structure reflects the phrasal entry identifiers of the entries used to determine the new entry. For any set of entries in the phrasal information structure produced by an ordered rewrite rule, the context of a missing semantic fact is subtracted from the context of the entry lacking the semantic fact. Entries associated with a false context are discarded and entries sharing the same syntax and semantic information are merged. Any entries in the phrasal information structure associated with the “ALL” pseudofact are then determined. Alternate phrases are generated based on the source information for the entry in the phrasal information structure associated with the “ALL” pseudofact.
Owner:PALO ALTO RES CENT INC
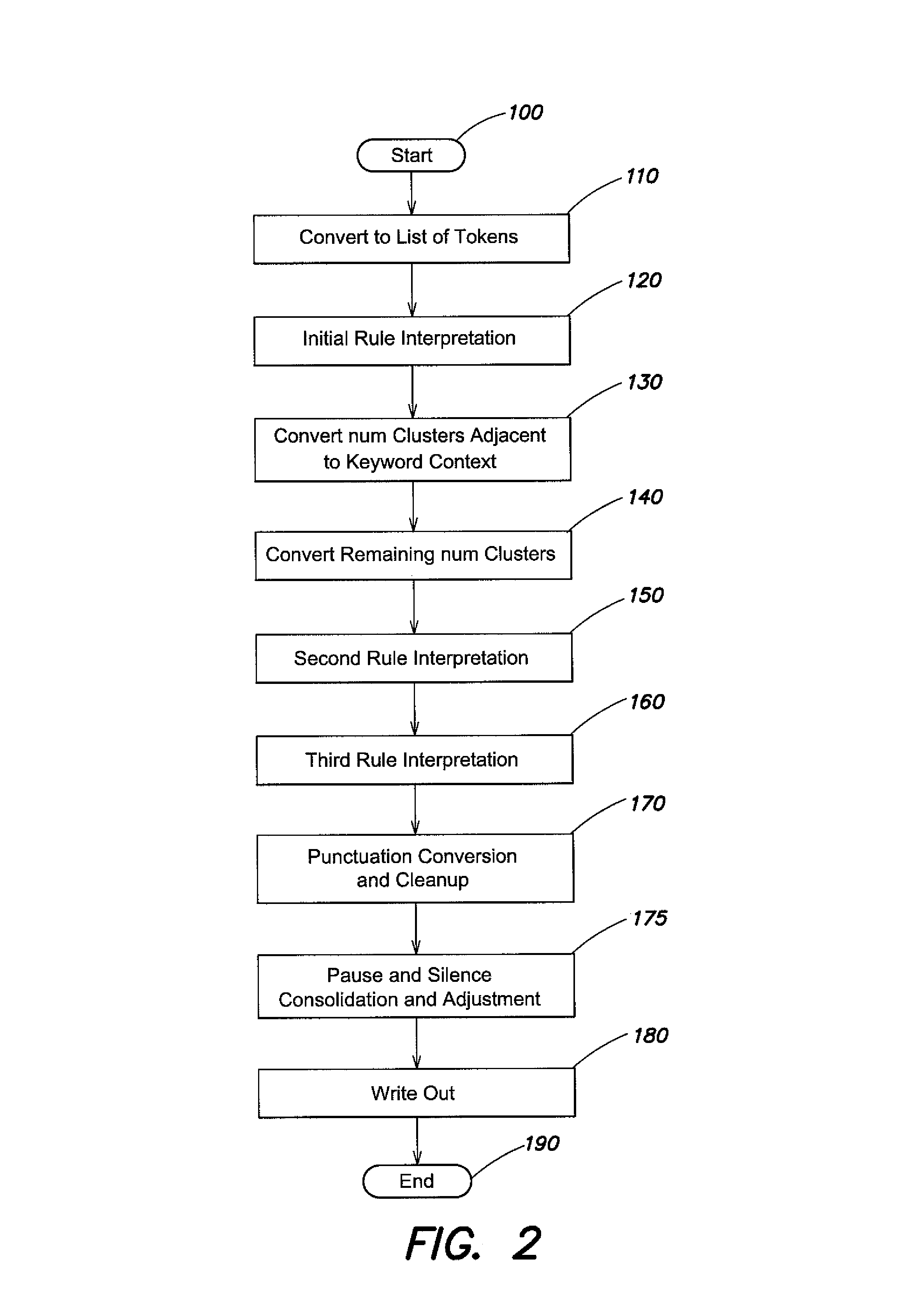
System and method for post processing speech recognition output
InactiveUS7996223B2Natural language data processingSpeech recognitionRewrite ruleSpeech identification
A system and method may be disclosed for facilitating the conversion of dictation into usable and formatted documents by providing a method of post processing speech recognition output. In particular, the post processing system may be configured to implement rewrite rules and process raw speech recognition output or other raw data according to those rewrite rules. The application of the rewrite rules may format and / or normalize the raw speech recognition output into formatted or finalized documents and reports. The system may thereby reduce or eliminate the need for post processing by transcriptionists or dictation authors.
Owner:NUANCE COMM INC
Automatic suggestion for query-rewrite rules
Embodiments of the invention relate to automatically suggesting query-rewrite rules. One embodiment includes providing a missing search result for a query. A collection of semantically coherent rewrite rules are generated based on the missing search result. Generating the missing search result includes: selecting candidates including subsequences of the query and subsequences of particular fields of a document, invoking a search engine using the candidates for providing search results, filtering out particular candidates that fail to achieve a desired search result, and classifying remaining candidates based on a learned classifier. Query rewrite rules for document searching are suggested based on the classified remaining candidates.
Owner:IBM CORP
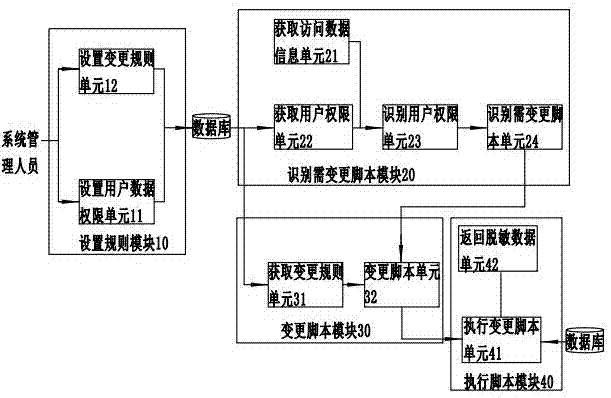
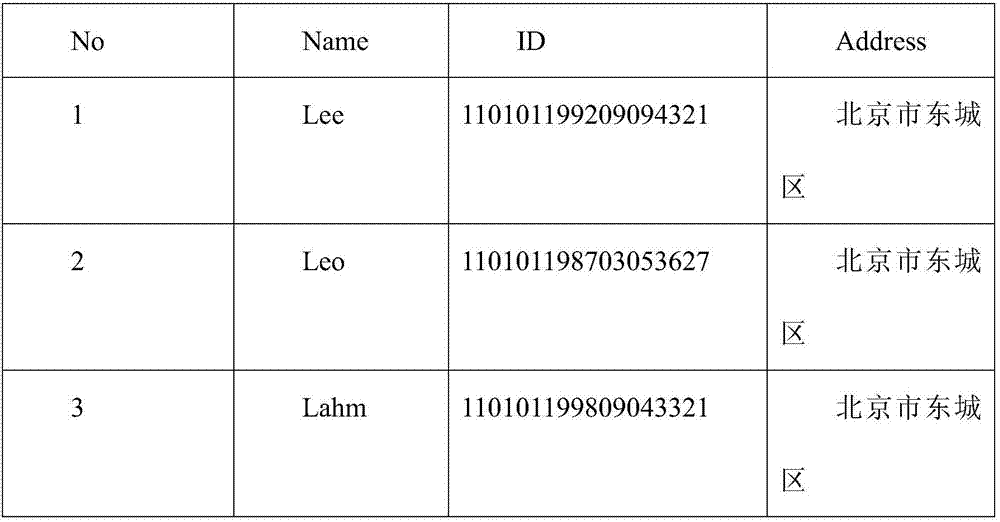
System and method for realizing data desensitization
The invention discloses a system for realizing data desensitization. The system comprises a database, a rule setting module, a to-be-changed script recognition module, a script changing module and a script execution module, wherein the rule setting module, the to-be-changed script recognition module, the script changing module and the script execution module are connected in sequence; according to the rule setting module, an access permission of a user on data is set according to a business demand in advance, and sql rewriting rules are set for sensitive fields and stored into the database; according to the to-be-changed script recognition module, the access permission of the user on the data is judged, an sql script of an unauthorized user is recognized, and a to-be-changed script is determined; the script changing module rewrites and changes the sql script of the unauthorized user; and the script execution module executes the changed sql script, generates desensitized data and transmits the desensitized data to an access terminal accessed by the user. The invention furthermore discloses a desensitization method of the system for realizing data desensitization. Through the system and the method, targeted desensitization can be performed, and desensitization workload is reduced.
Owner:GUANGDONG KINGPOINT DATA SCI & TECH CO LTD
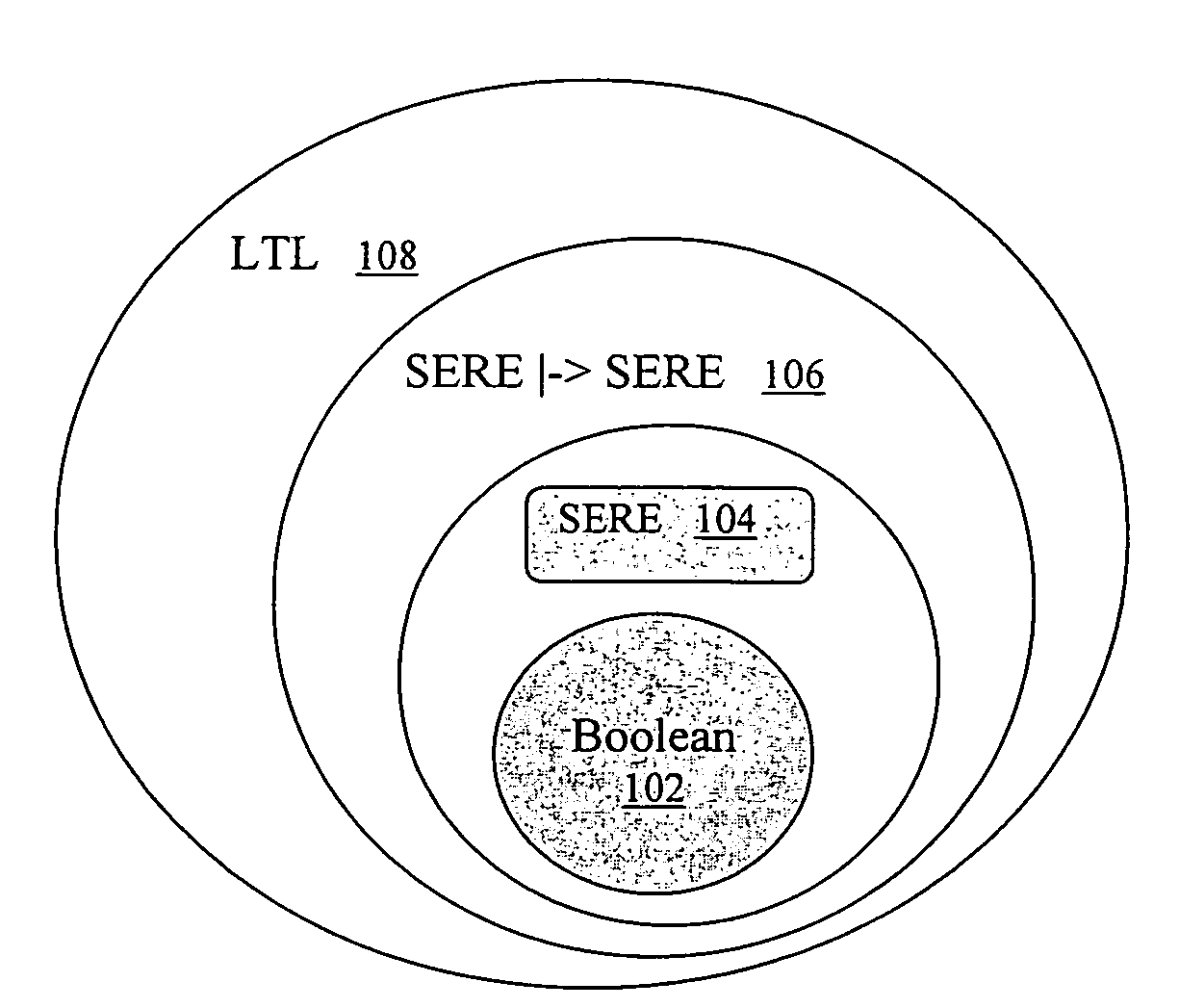
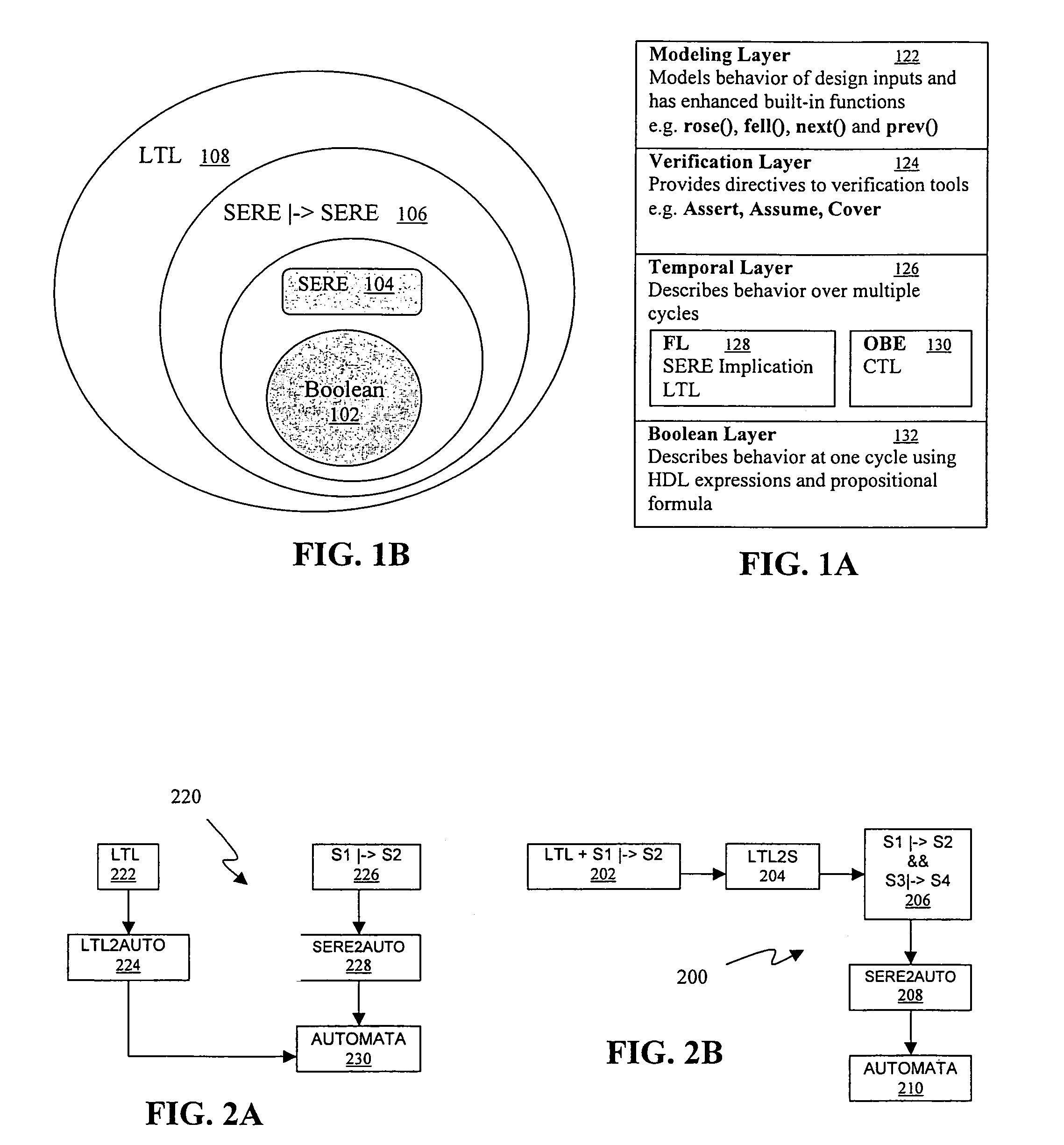
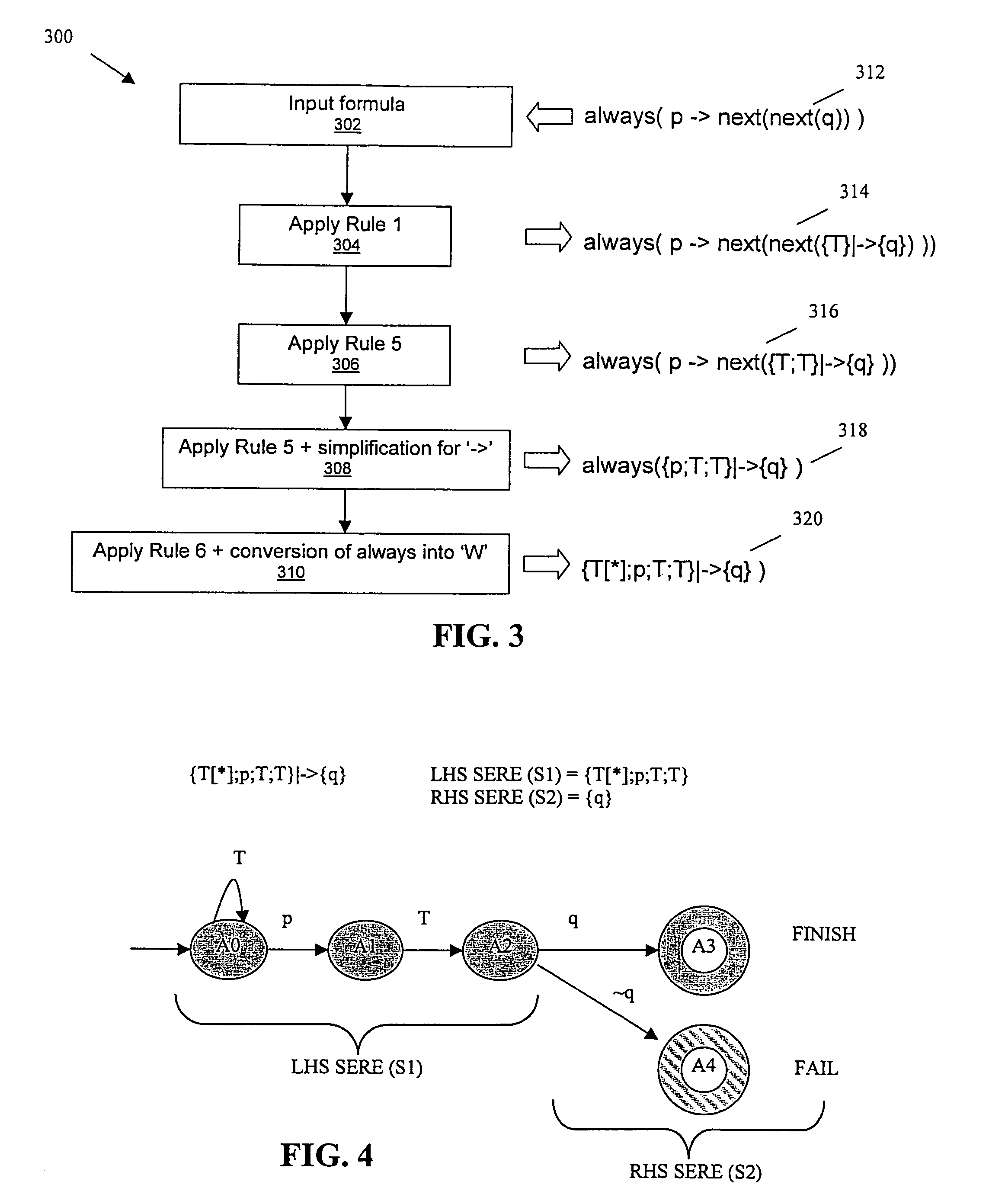
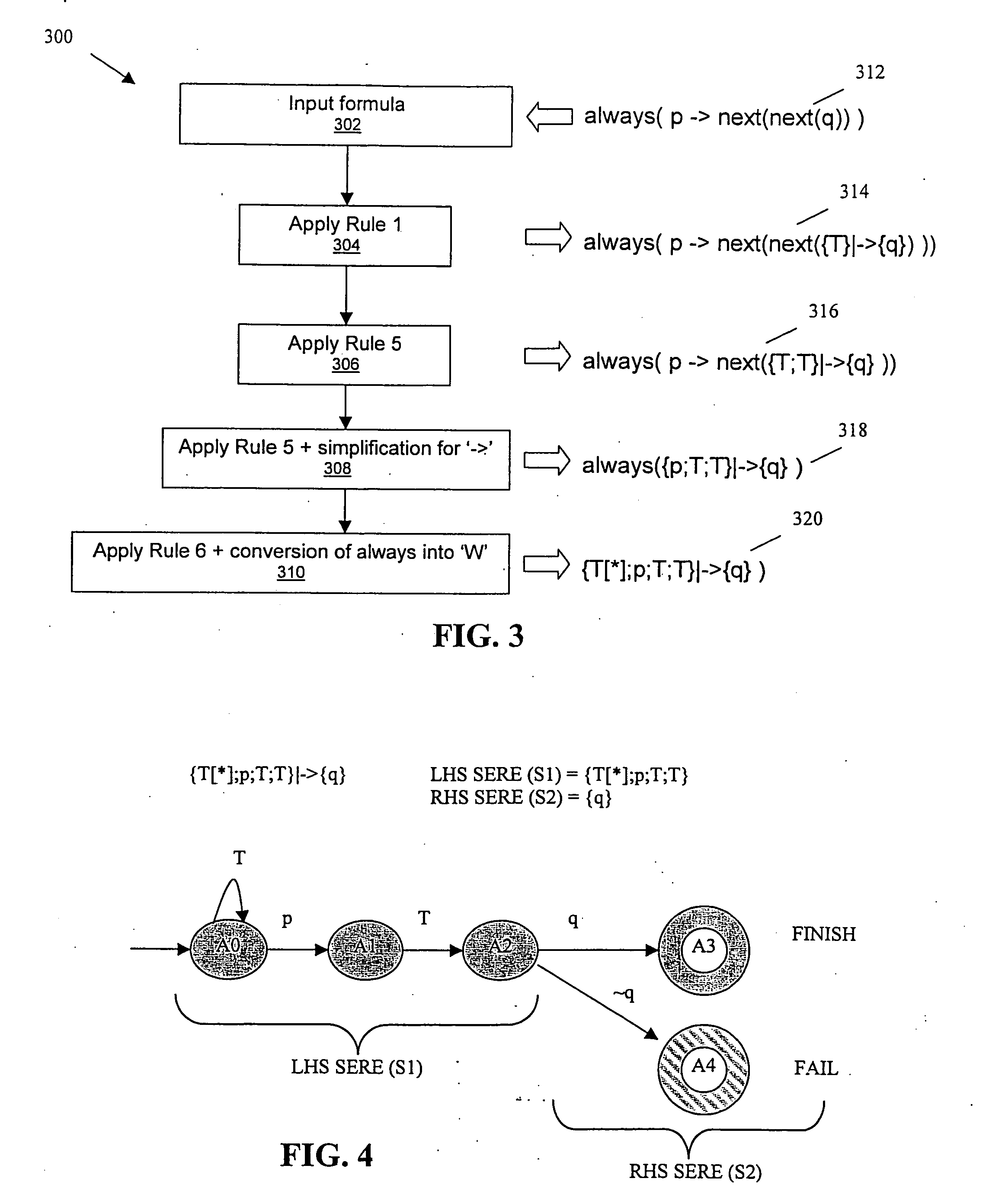
Transformation of simple subset of PSL into SERE implication formulas for verification with model checking and simulation engines using semantic preserving rewrite rules
InactiveUS7386813B2Design optimisation/simulationSoftware simulation/interpretation/emulationProperty Specification LanguageRewrite rule
Owner:CADENCE DESIGN SYST INC
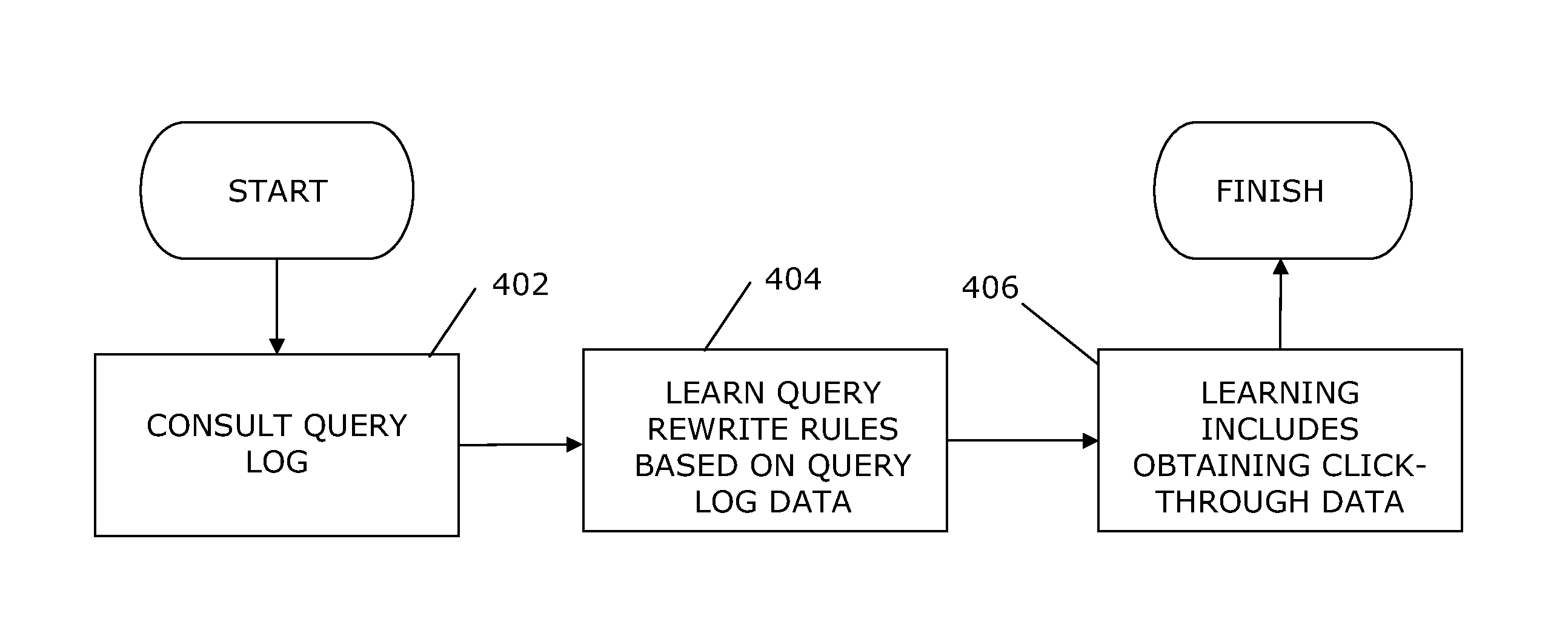
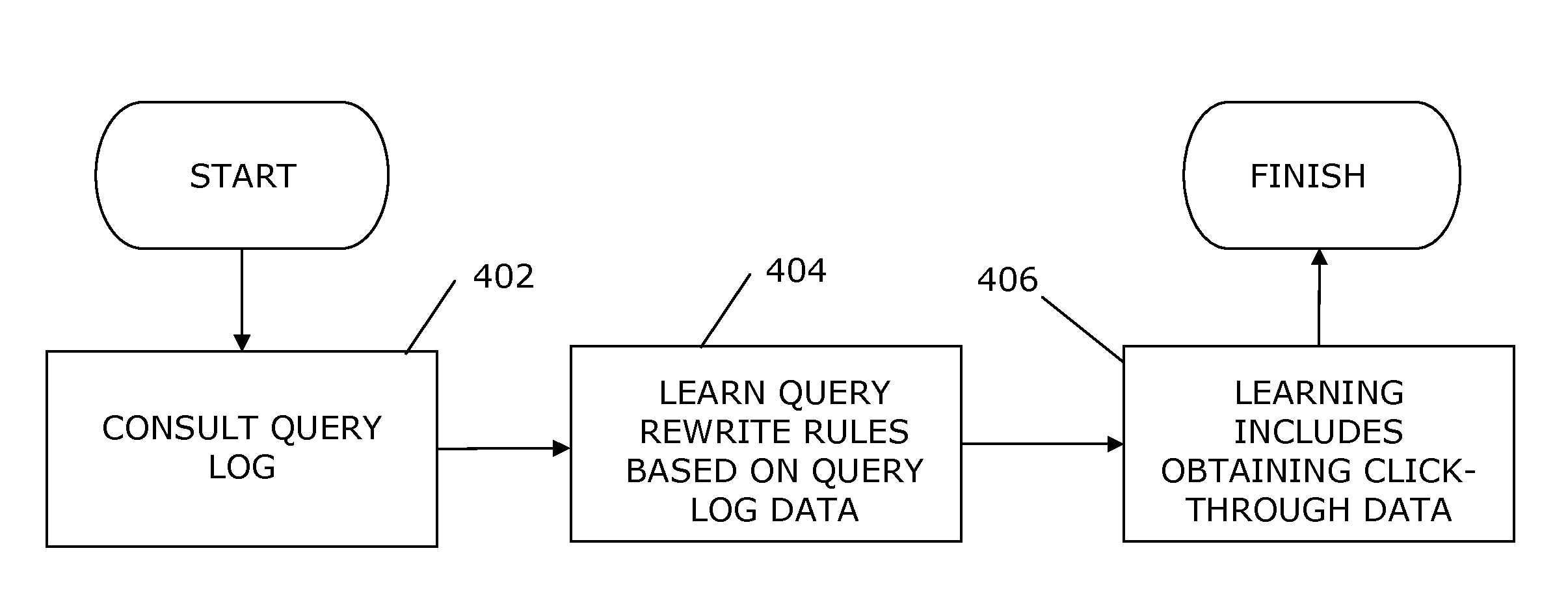
Learning rewrite rules for search database systems using query logs
ActiveUS20130262351A1Digital data information retrievalDigital computer detailsRewrite ruleData mining
Owner:IBM CORP
Modeled object updating
ActiveUS8983805B2Cathode-ray tube indicatorsComputation using non-denominational number representationGraphicsRewrite rule
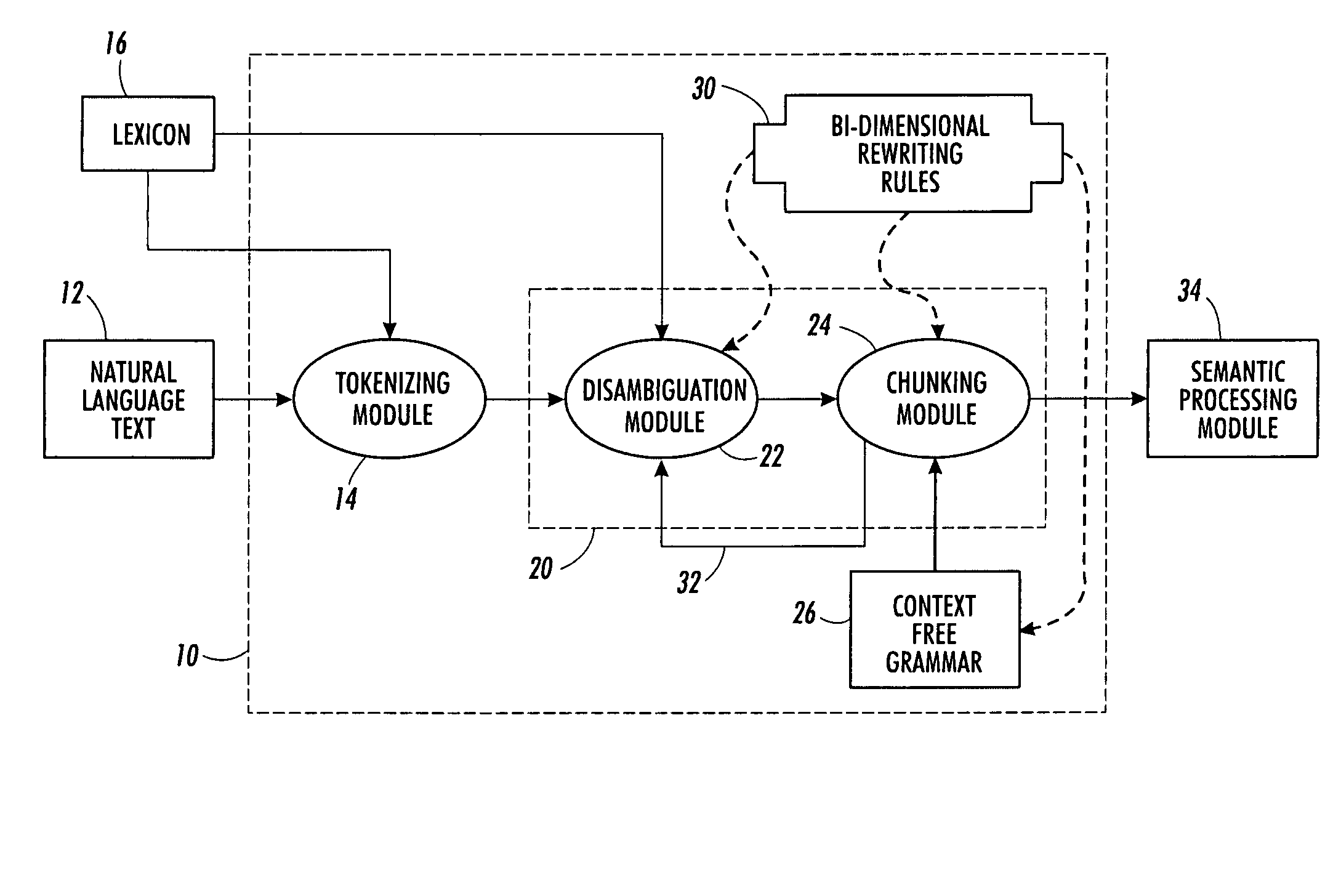
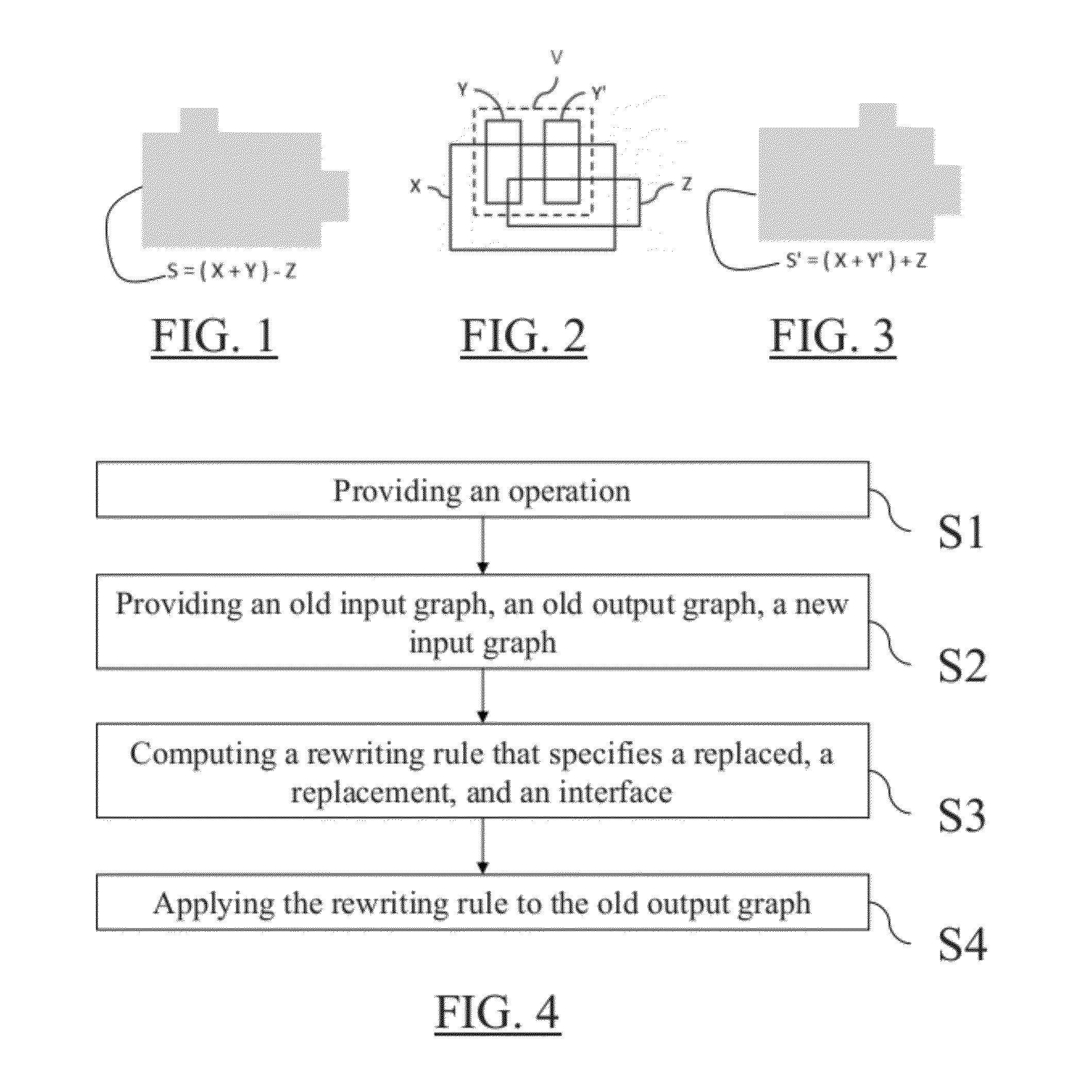
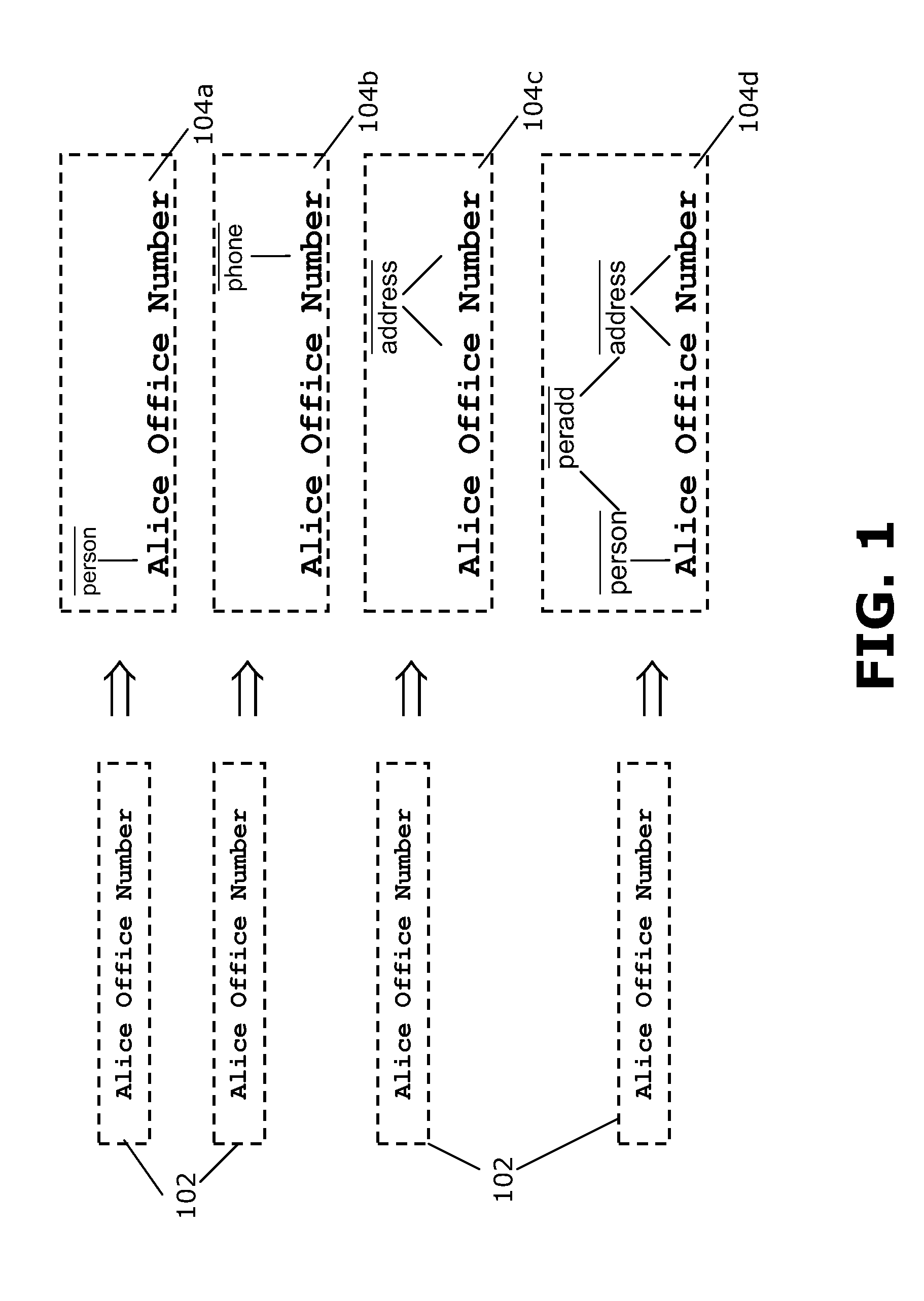
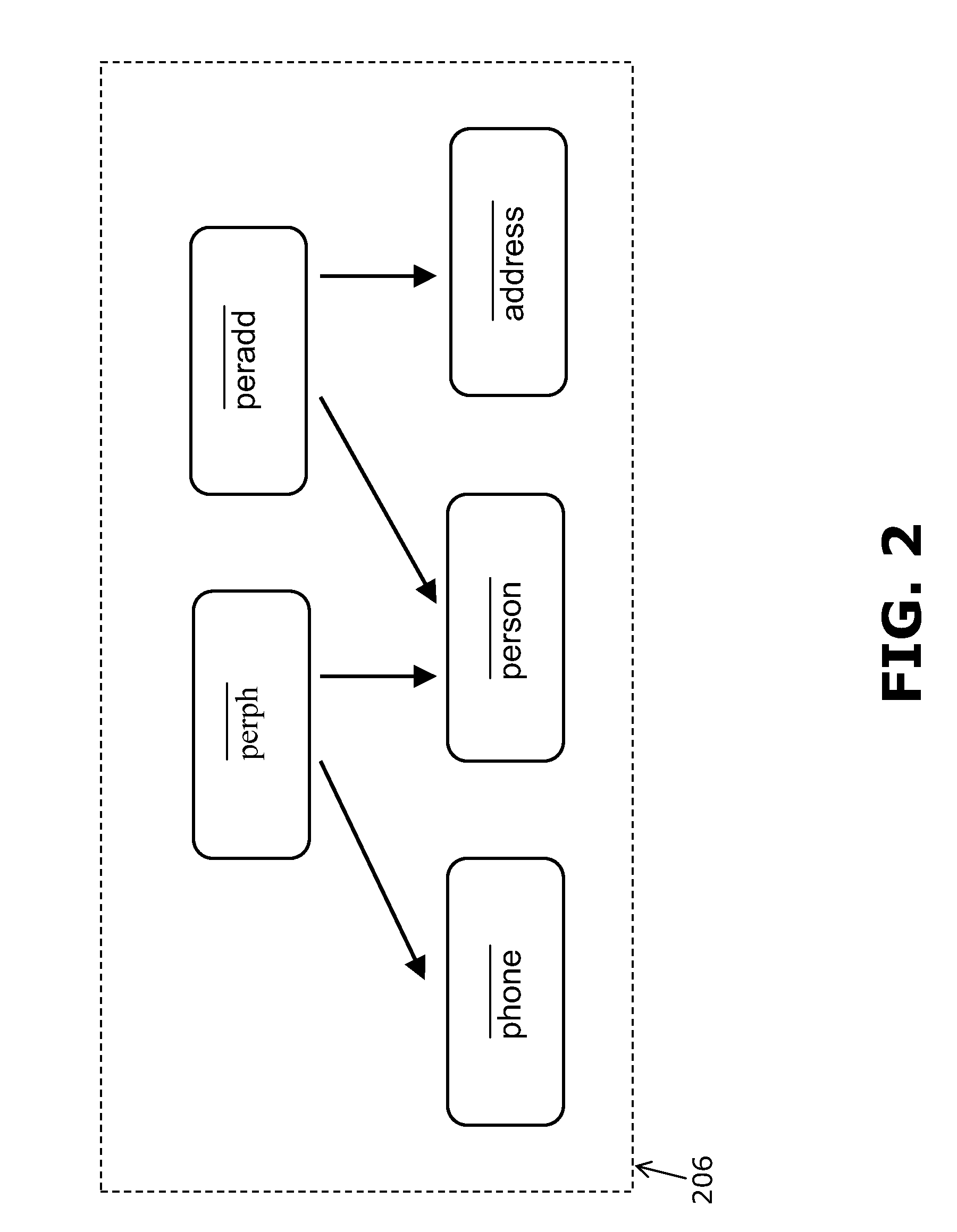
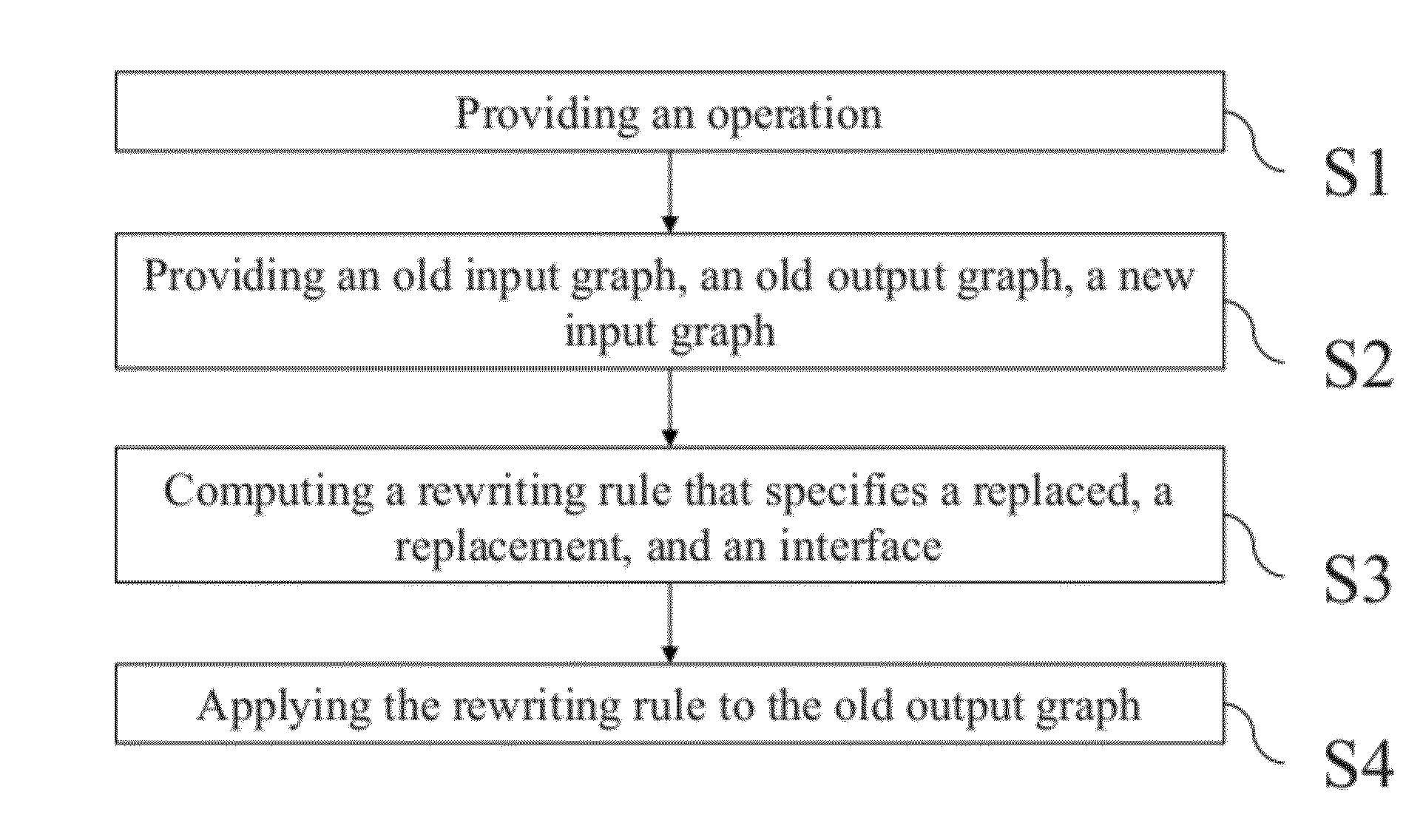
Provided is a computer-implemented method for updating a 3D model. The method comprises providing an operation undergone by the 3D model, an old input graph of the 3D model before undergoing the operation, an old output graph of the 3D model corresponding to an application of the operation to the old input graph, and a new input graph of the operation. The new input graph is generated as a result of a modification of the 3D model. The method also comprises computing a double push-out rewriting rule that specifies a part of the old input graph to be replaced, a part of the new input graph to replace the part of the old input graph. The rewriting rule also specifies an interface which is a part common to the part of the old input graph, the part of the new input graph, and the old output graph. The method further comprises applying the rewriting rule directly on the old output graph. This transforms the old output graph to a new output graph representing an updated 3D model of the real world object. The method is an improvement to updating a 3D model in a CAD system.
Owner:DASSAULT SYSTEMES
Learning rewrite rules for search database systems using query logs
ActiveUS20130262350A1Digital data information retrievalDigital computer detailsRewrite ruleData mining
Owner:IBM CORP
Transformation of simple subset of PSL into SERE implication formulas for verification with model checking and simulation engines using semantic preserving rewrite rules
InactiveUS20060136879A1Design optimisation/simulationSoftware simulation/interpretation/emulationProperty Specification LanguageRewrite rule
The disclosure presents a formulation to support simulatable subset (also known as ‘simple-subset’) of a property specification language. This method is applicable for model checking and simulation. In this formulation, the ‘simple-subset’ is transformed to a set of basic formulas. Verification engines are required to support the basic formula only. The basic formula is a form of automata in the property specification language. This is called SERE implication. The efficiency of verification is dependent on size of automata. Miscellaneous opportunistic rules are applied to optimize SERE implication formulas.
Owner:CADENCE DESIGN SYST INC
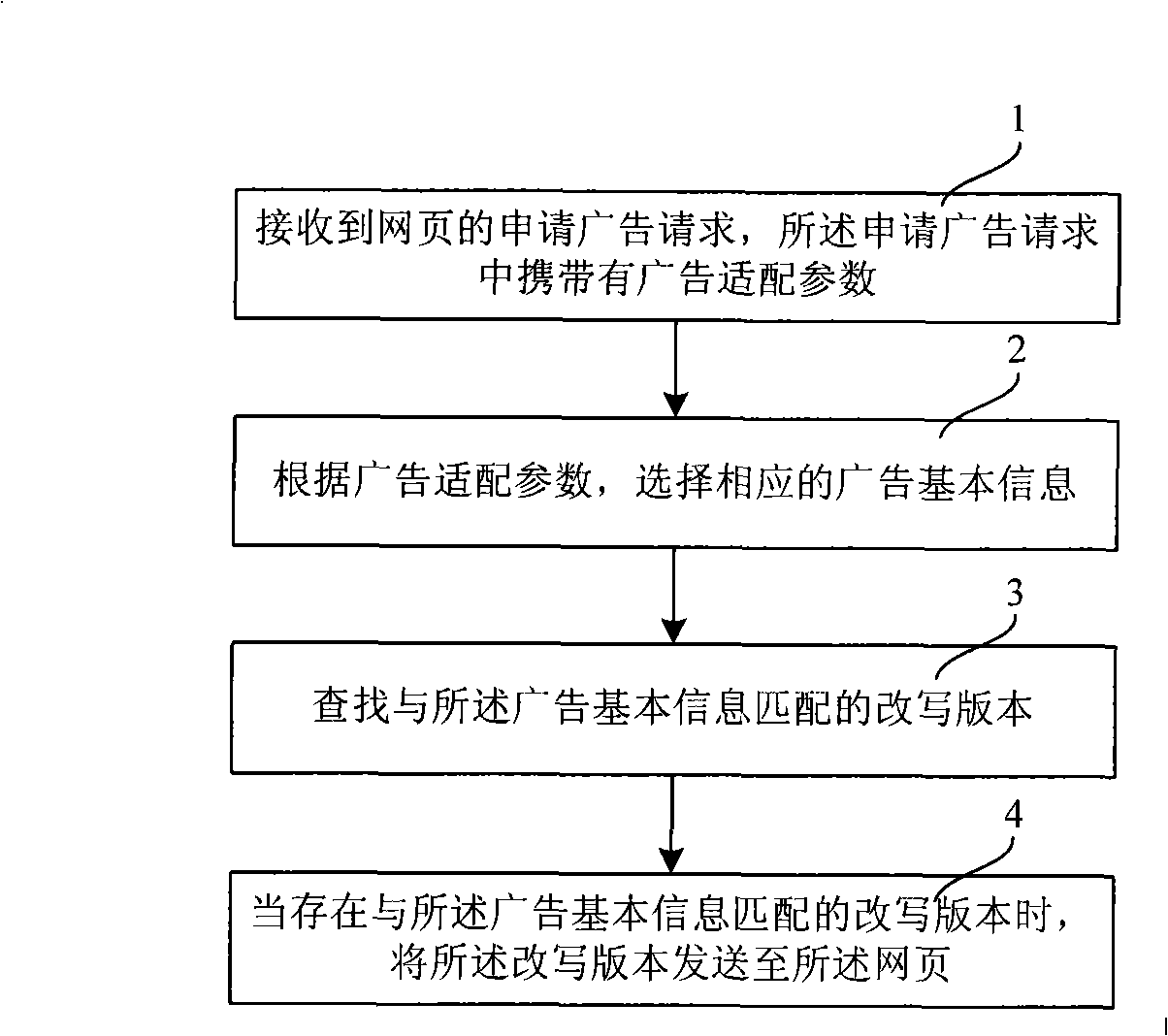
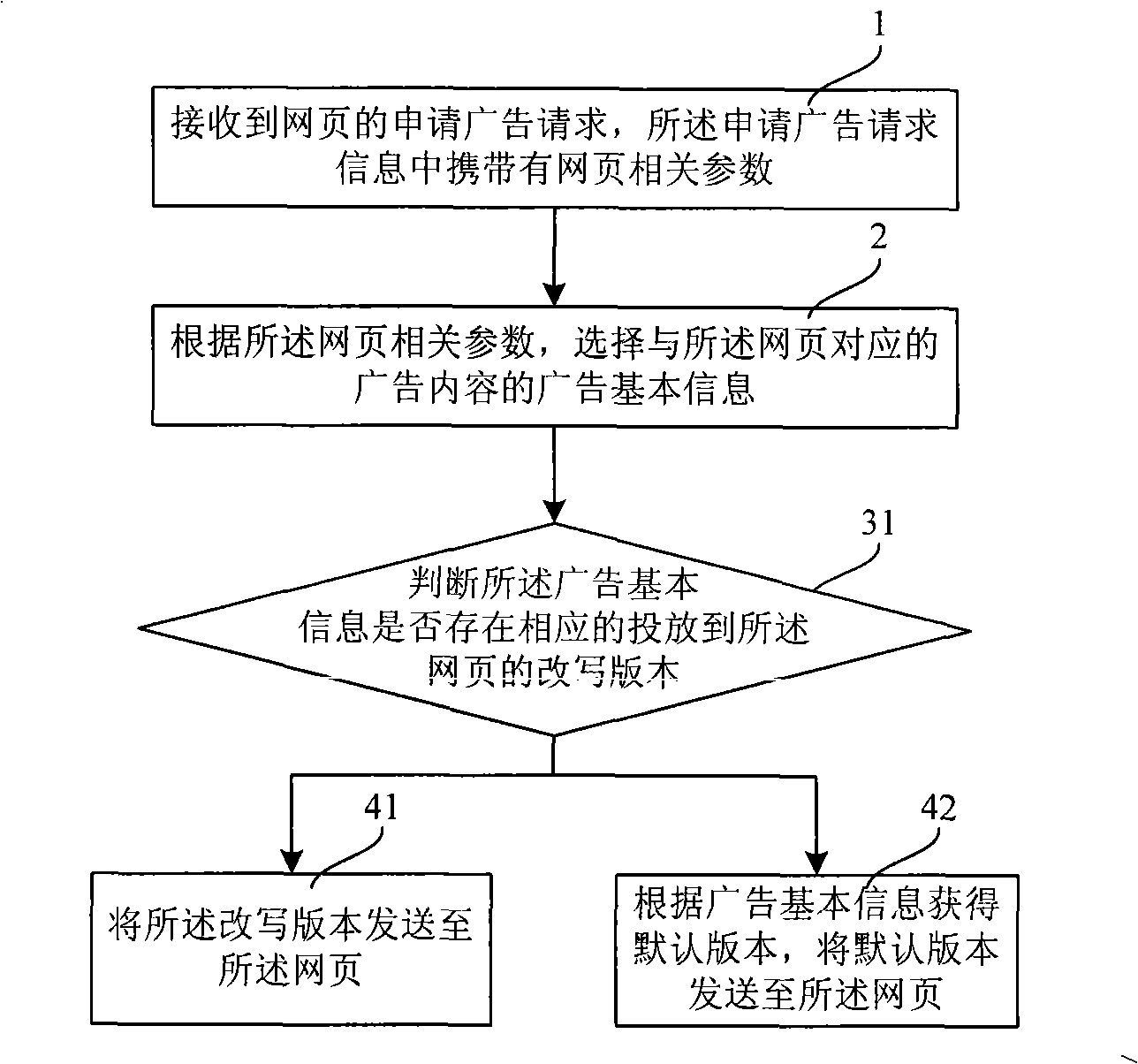
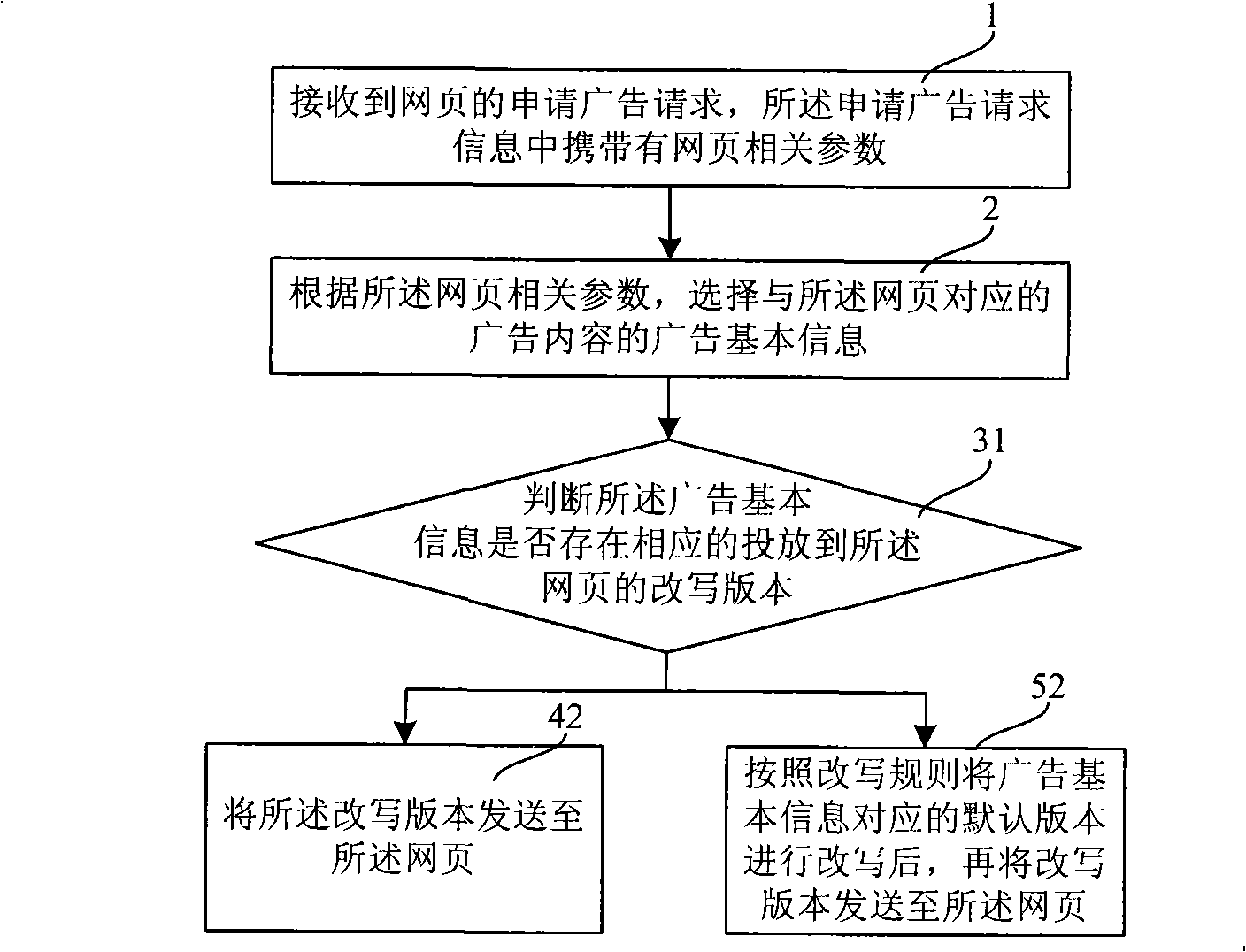
Advertisement releasing method and advertisement releasing server
InactiveCN101295301AIncrease attractivenessImprove click-through rateMarketingSpecial data processing applicationsRewrite ruleWeb page
The invention relates to an advertising method, comprising the steps that: an advertisement application request of a web page is received, the advertisement application request carries the advertisement adaptation parameters; the corresponding advertisement basic information is selected according to the advertisement adaptation parameters; a rewritten version matched with the advertisement basic information is searched; when the rewritten version matched with the advertisement basic information exists, the rewritten version is sent to the web page. The invention further relates to an advertising server, comprising an information interface module, wherein, the advertising server further comprises: an advertisement content library, a rewriting module and an inquiry module; the rewriting module is connected with the advertisement content library, thus rewriting a default version of the advertisement according to the rewriting rules and saving the rewritten version into the advertisement content library; and the inquiry module is connected with the information interface module and the advertisement content library. The advertising method provides the rewritten version to the content advertisement, when the text of the rewritten version is simple and the meaning is clear, the attraction of the advertisement can be correspondingly increased, thus achieving better advertising effect.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method and system for realizing receipt rewriting
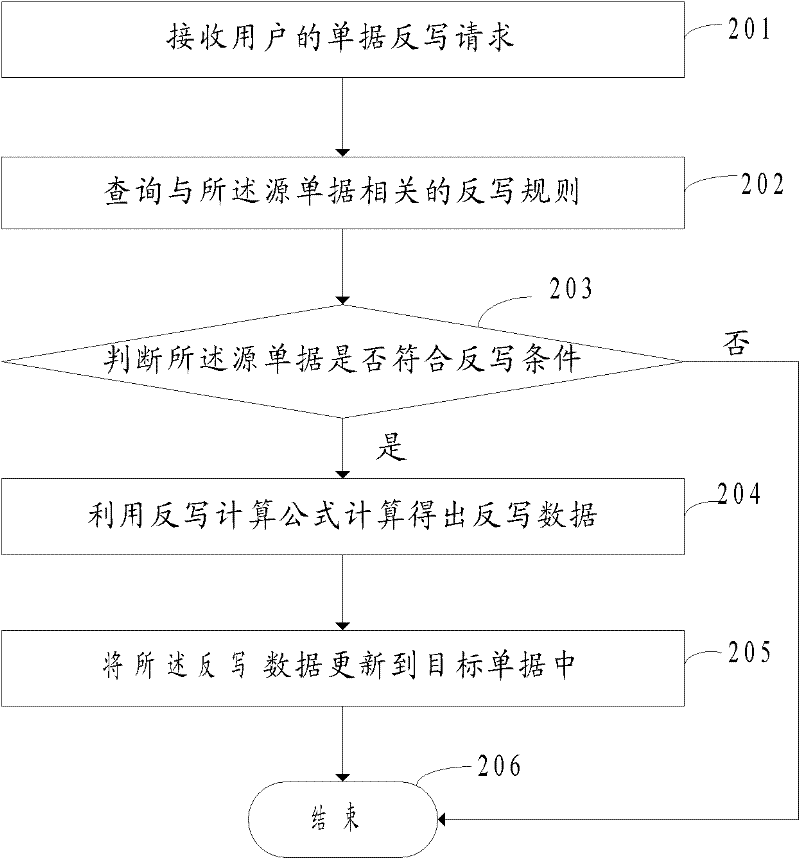
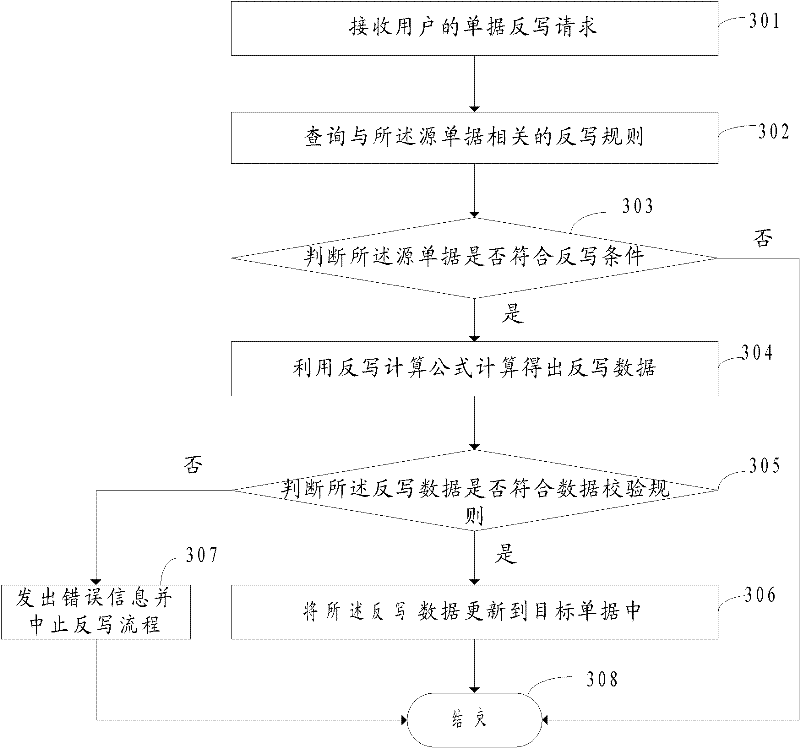
ActiveCN102479199AImprove the efficiency of reverse writingReduce workloadResourcesSpecial data processing applicationsRewrite ruleComputer science
The invention provides a method and a system for realizing receipt rewriting. The method comprises the following steps: receiving a receipt retrography request from a user, wherein the receipt rewriting request is the request for rewriting the data in a source receipt to a target receipt; querying a rewriting rule related to the source receipt, wherein the rewriting rule comprises a rewriting calculation formula; calculating the rewriting data by using the rewriting calculation formula; updating the rewriting data into the target receipt so as to realize the receipt rewriting. According to the embodiment of the invention, the professionals do not need to compile codes actively, thus work load can be lessened and then the efficiency of the receipt rewriting can be improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
ASP.NET-based pseudo static page implementation method
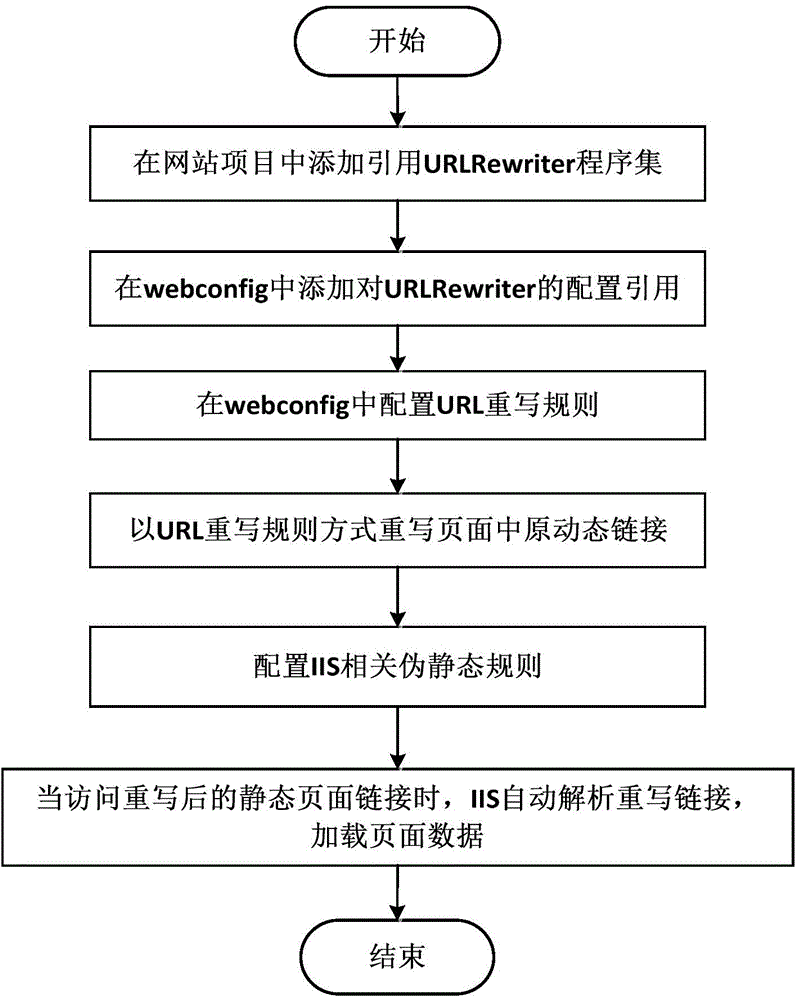
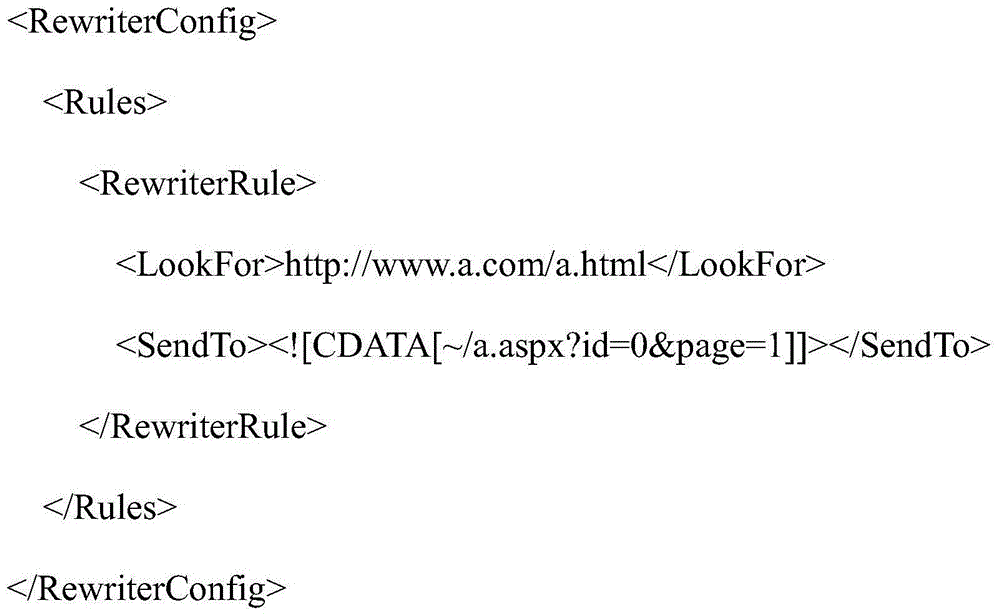
InactiveCN104866312AFix search issuesSpecific program execution arrangementsTime dynamicsRewrite rule
The present invention relates to the technical field of ASP.NET, and in particular relates to an ASP.NET-based pseudo static page implementation method. According to the method provided by the present invention, a rewrite rule is configured for webconfig by introducing a URLRewriter program set; a dynamic link is rewritten; when the rewritten link is accessed, an IIS performs rewrite parsing on the link, automatically turns to the dynamic link, and loads page data. The method according to the present invention solves the problem that, during the Web development process based on ASP.NET, search efficiency of a search engine is reduced because the link of real-time dynamic content is displayed, and is thus widely applied in ASP.NET development.
Owner:G CLOUD TECH
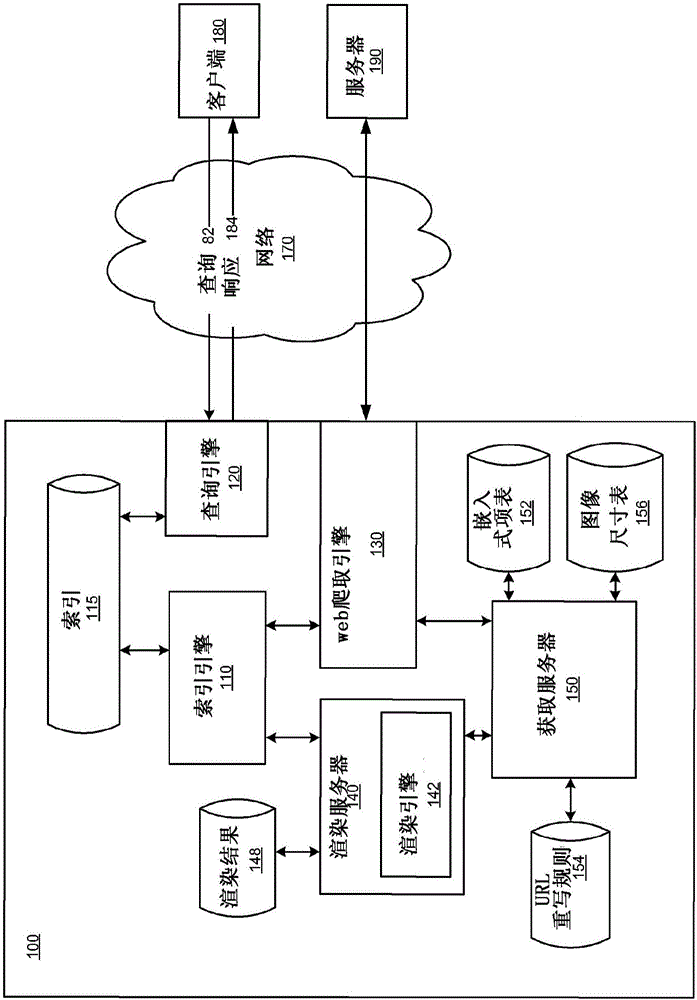
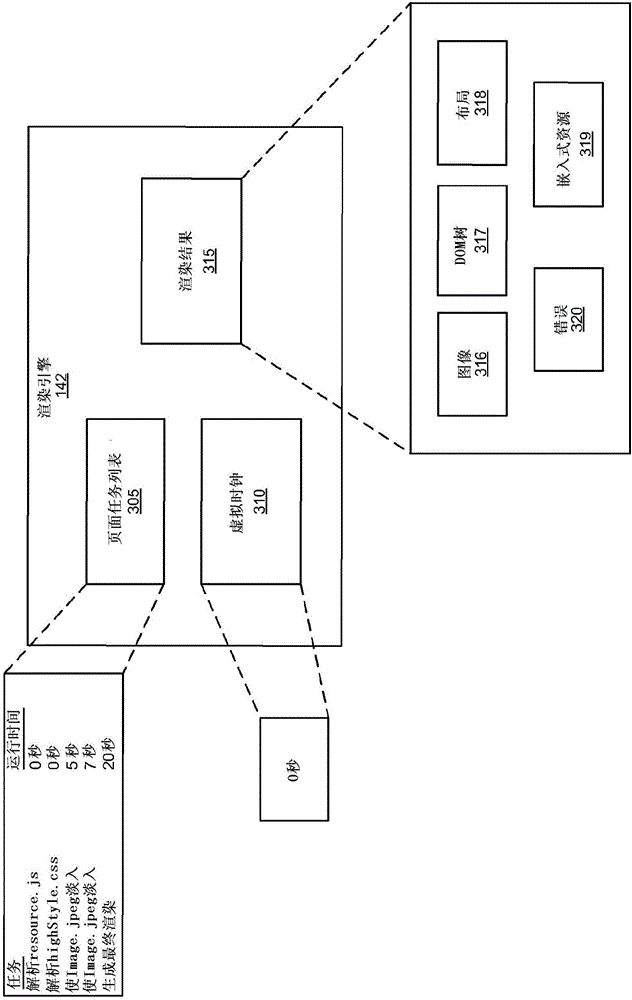
Batch-optimized render and fetch architecture
ActiveCN106462582AAvoid common mistakesAvoid timeout errorsText processingSpecial data processing applicationsRewrite ruleWeb page
Implementations include a batch-optimized render and fetch architecture. An example method performed by the architecture includes receiving a request from a batch process to render a web page and initializing a virtual clock and a task list for rendering the web page. The virtual clock stands still when a request for an embedded item is outstanding and when a task is ready to run. The method may also include generating a rendering result for the web page when the virtual clock matches a run time for a stop task in the task list, and providing the rendering result to the batch process. Another example method includes receiving a request from a batch process to render a web page, identifying an embedded item in the web page, and determining, based on a rewrite rule, that the embedded item has content that is duplicative of content for a previously fetched embedded item.
Owner:GOOGLE LLC
Automatic suggestion for query-rewrite rules
ActiveUS9348895B2Digital data information retrievalSpecial data processing applicationsRewrite ruleDocumentation
Owner:INT BUSINESS MASCH CORP
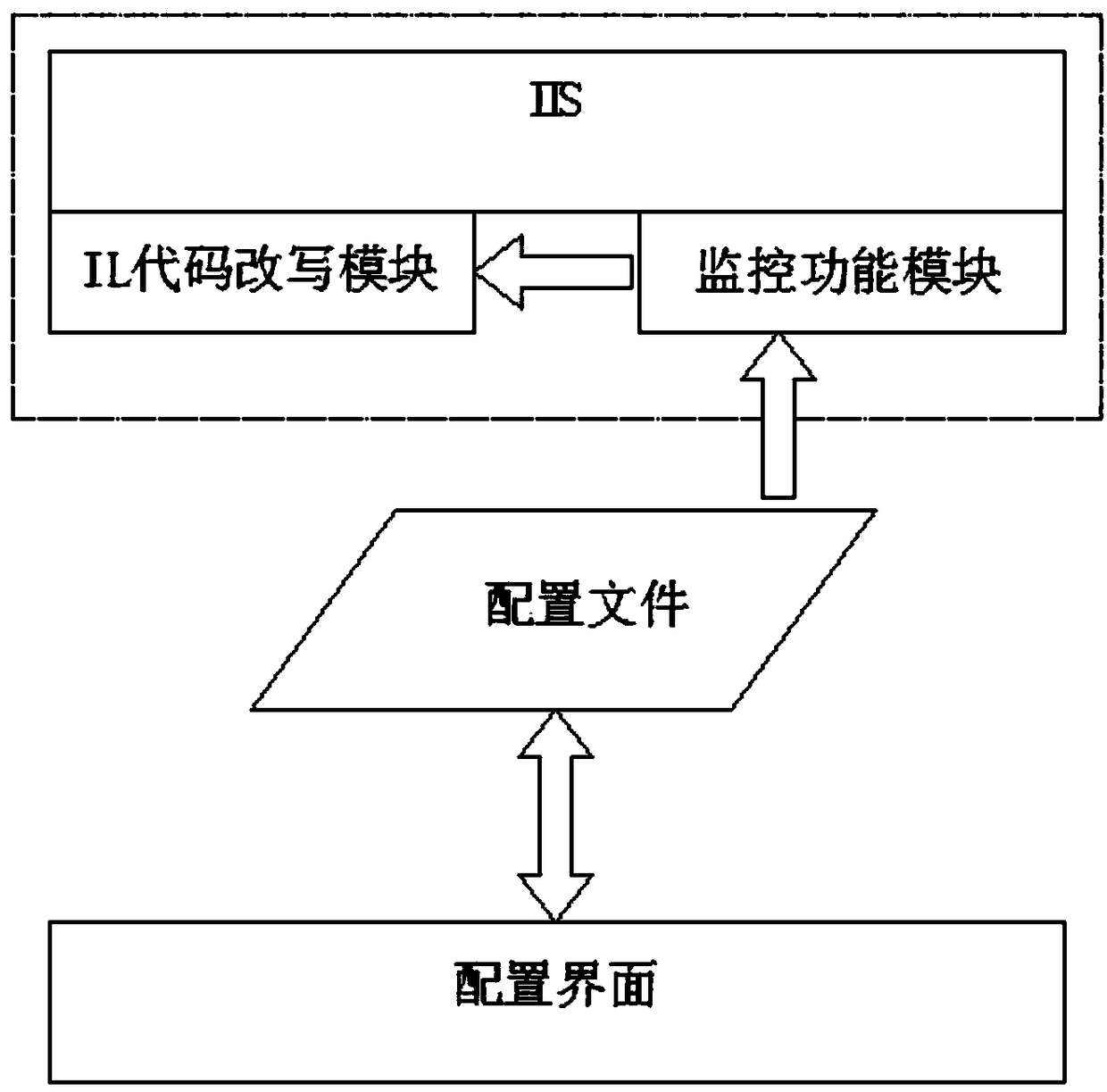
Diagnosis method for analyzing performance and fault of ASP. NET application software
ActiveCN108089978AReduce the difficulty of implementationRewrite rules are simple and easy to useHardware monitoringSoftware testing/debuggingVisibilityError processing
The present invention discloses a diagnosis method for analyzing the performance and the fault of ASP. NET application software. The method comprises the following steps: (1) when starting an ASP. NETapplication program, loading an IL code rewriting module through environment variables; (2) when the ASP. NET application program dynamically compiles the IL code, triggering the IL code rewriting function, and loading a monitoring function module for asynchronous processing; (3) in the process of processing an HTTP request, collecting an execution process and error information of a code segment;and (4) creating separate threads to asynchronously process the collected performance information and error information. According to the diagnosis method for analyzing the performance and the faultof ASP. NET application software disclosed by the present invention, without the involvement of developers, the difficulty of implementation is reduced, the rewriting rule is simple and easy to use, and the abnormalities are intercepted; and even if there is a bug, the original system cannot be affected, and by processing the classified application components and application errors, the data visibility is improved.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Method and device for generating uniform resource locator (URL) rewriting rules
ActiveCN109561163ASave manpower and material costsReduce errorsTransmissionRewrite engineRewrite rule
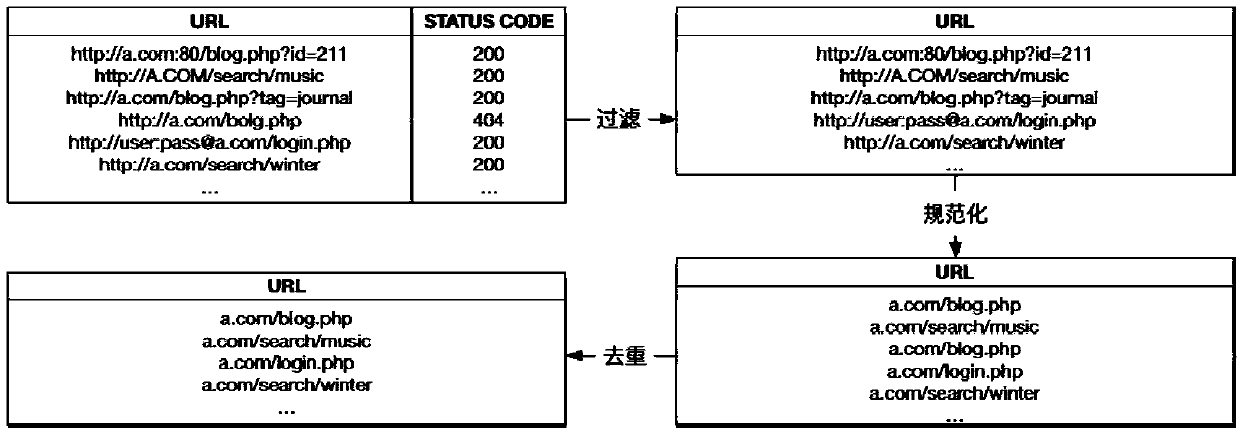
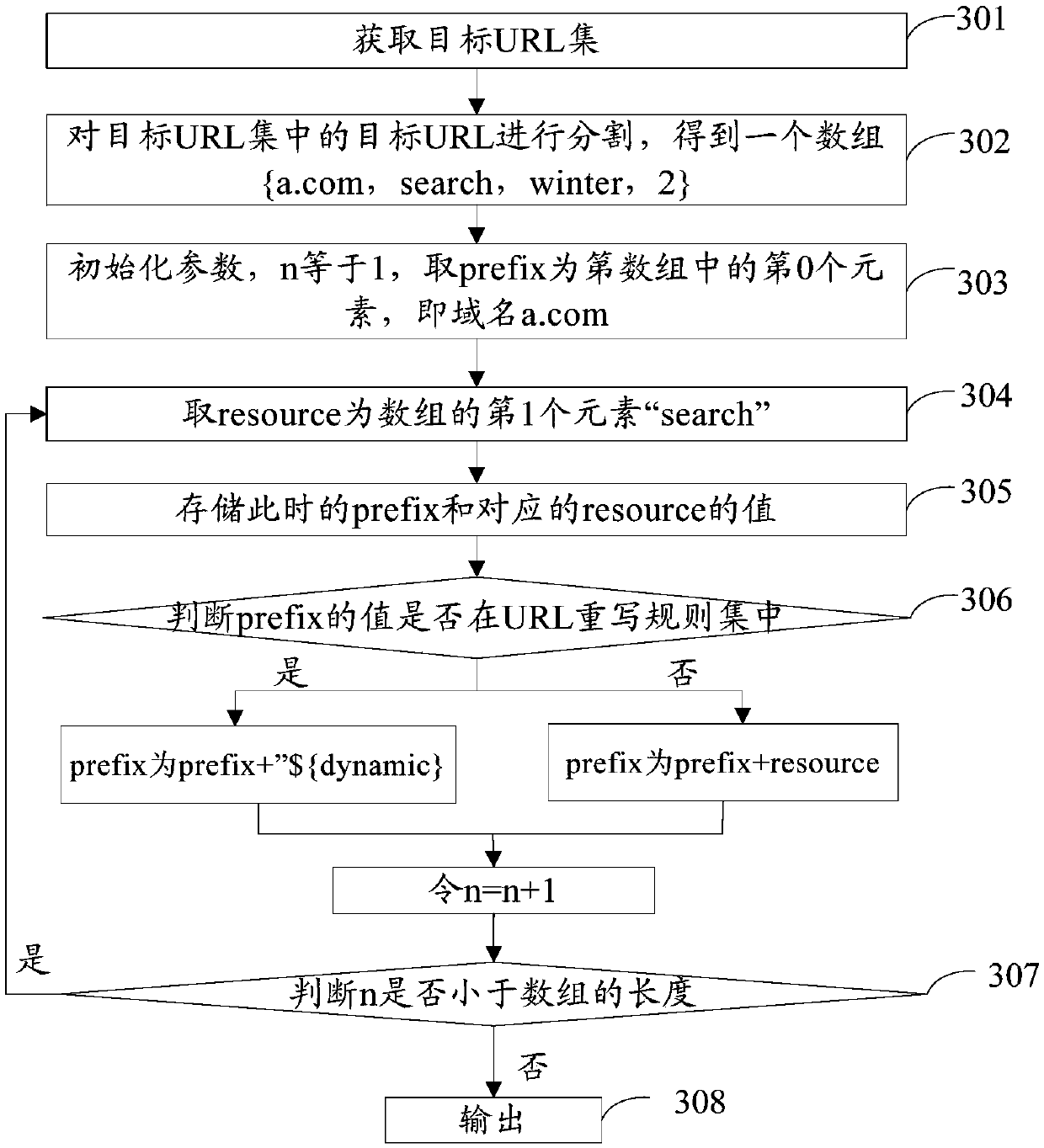
The invention provides a method and device for generating uniform resource locator (URL) rewriting rules. The method comprises the steps of obtaining a target URL set of a target website, wherein thetarget website is a website to generate the URL rewriting rules; obtaining a parameter set of mutually corresponding prefix parameters and resource parameters in the target URL set, wherein the resource parameters are sub-paths of the prefix parameters; and generating a URL rewriting rule set of the target website according to the parameter set. The URL rewriting rules of the website can be automatically analyzed according to an access log without manual participation by adopting the embodiment of the invention.
Owner:ALIBABA GRP HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com