System and method for realizing data desensitization
A data desensitization and desensitization technology, which is applied in the field of data security, can solve the problems of regular update, heavy preparatory workload, and inability to meet flexibility and changes, so as to reduce space occupation, fast desensitization speed, and reduce data desensitization workload effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be described in further detail below by means of specific embodiments:
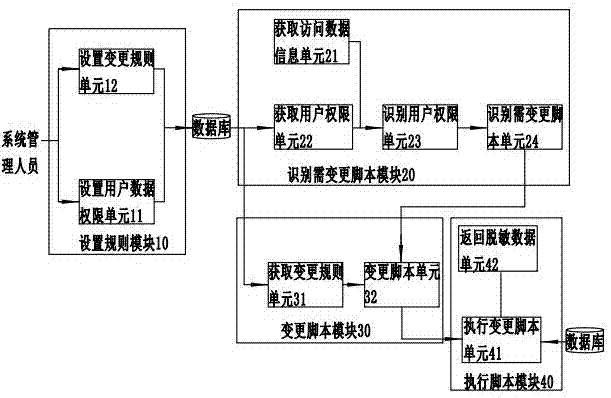
[0048] The reference numerals in the drawings of the description include: setting rule module 10, setting user data authority unit 11, setting change rule unit 12, identifying script module 20 to be changed, obtaining access data information unit 21, obtaining user authority unit 22, identifying user Authorization unit 23 , identification needs to change script unit 24 , change script module 30 , acquisition change rule unit 31 , change script unit 32 , execute script module 40 , execute change script unit 41 , return desensitized data unit 42 .
[0049] Such as figure 1 As shown, a system for realizing data desensitization is composed of a rule setting module 10 , a script identification module 20 to be changed, a script modification module 30 and an execution script module 40 .
[0050] The setting rule module 10 is responsible for setting the user's access authority t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com