Auditing a device
a technology of a device and a test tube, applied in the field of auditing a device, can solve the problems of exacerbated situation, device with limited resources, and inability to store definitions of detecting all known programs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
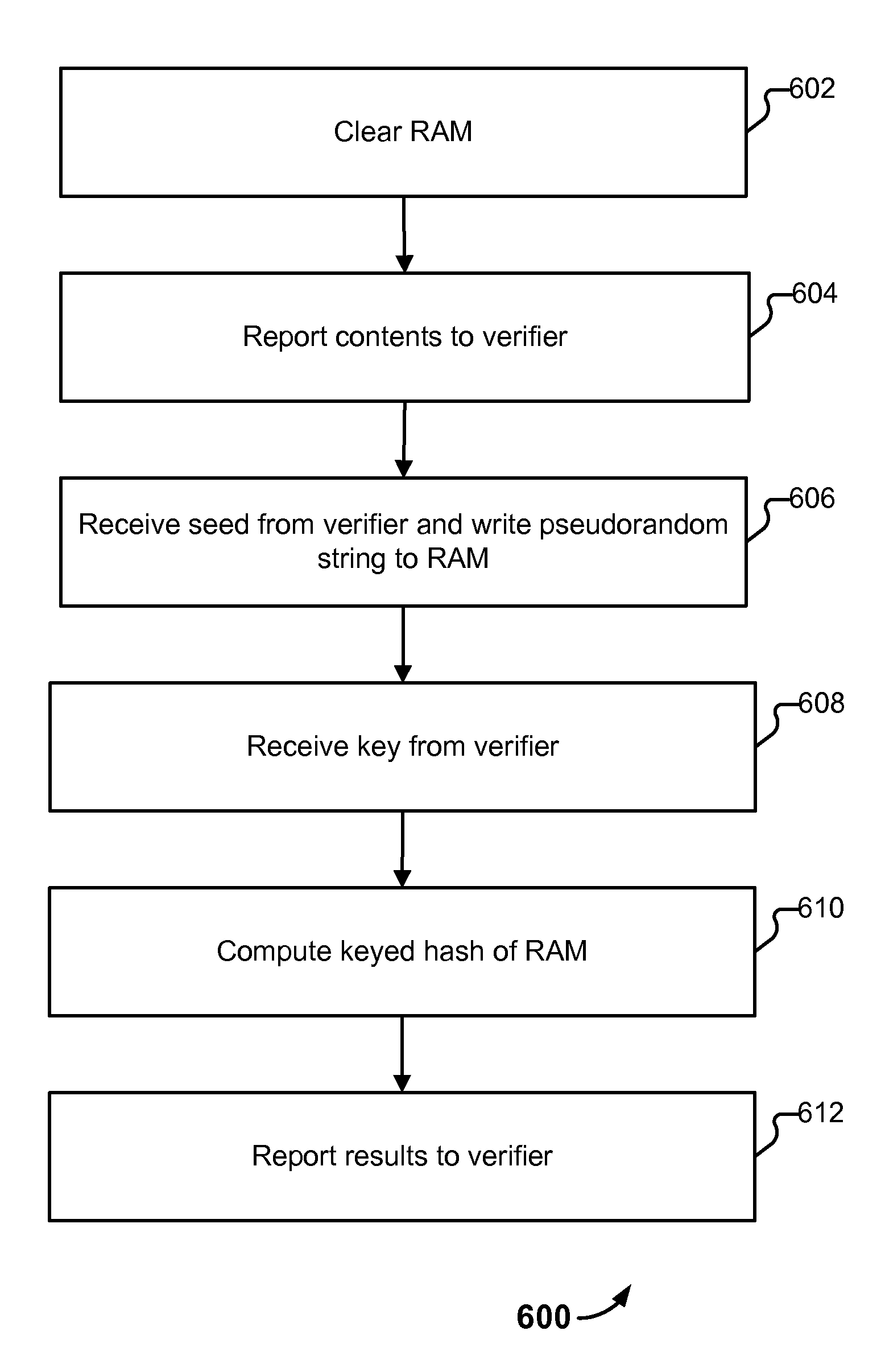
[0256]In some embodiments, only half as much pseudo-random material is generated (as before). Only in even-numbered cells of free RAM is it written and only in these cells will memory-printing be performed later on. This speeds up both the generation phase and the memory-printing by a factor 2. It also avoids having to page out material in RAM, and allows the odd-numbered cells to be used to store temporary values, such as variables needed for the execution of the memory-printing. Malware can exist, but can only jump (to odd cells), nothing else. If it attempts to do anything else, it will have to execute random content stored in the even-numbered cells, which will disrupt the malware execution.
example 2
[0257](a) Obtain the seed to generate the pseudo-random string very early on, and generate this in the background . . . at any time. Call this first pseudo-random generator PRG1. Store this string in secondary storage until it is needed.
[0258](b) To perform the setup before memory-printing, receive a new seed value (call this seed2) and use this as input to a fast pseudo-random generator. Call this second pseudo-random generator PRG2. Combine the output of PRG1 and PRG2 by XORing them together, writing the contents to free RAM. (Note that this can be combined with Example #1.)
[0259]Note: It is possible to use a weak PRG2, since the final randomness will be the combination of the two randomness sources. It can be also be one in accordance with NIST special publication 800-90. A secure block cipher can be converted into a CSPRNG by running it in counter mode. This is done by choosing a random key and encrypting a zero, then encrypting a 1, then encrypting a 2, etc. The counter can als...
example 3
[0262]As with Example 1, only checksum even cells from the cells that were read to the cache. If the location to be read is in the area where the monolith kernel resides, also accumulate the contents of the odd cells that were read. (That can be done after all the even cells have been accumulated, and it need not be done in the order they appear.)
Communication Speeds
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com