Multifunction authentication systems
a multi-functional authentication and authentication system technology, applied in the field of multi-functional authentication systems, can solve the problems of users changing, prone to change, and the process of purchasing these types of instruments takes a considerable amount of time, so as to shorten the accounting cycle, increase the propensity to buy, and increase the sales propensity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
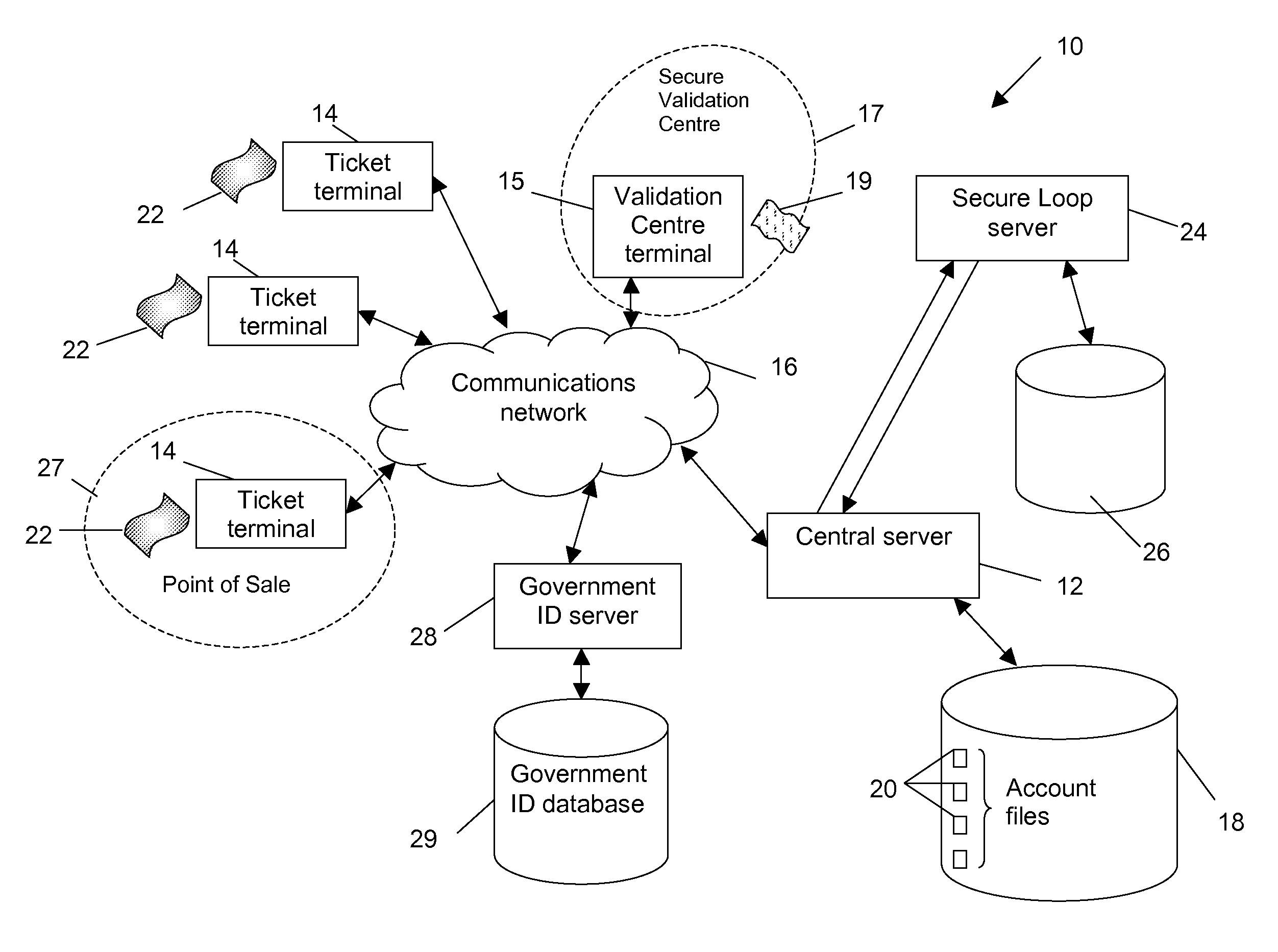
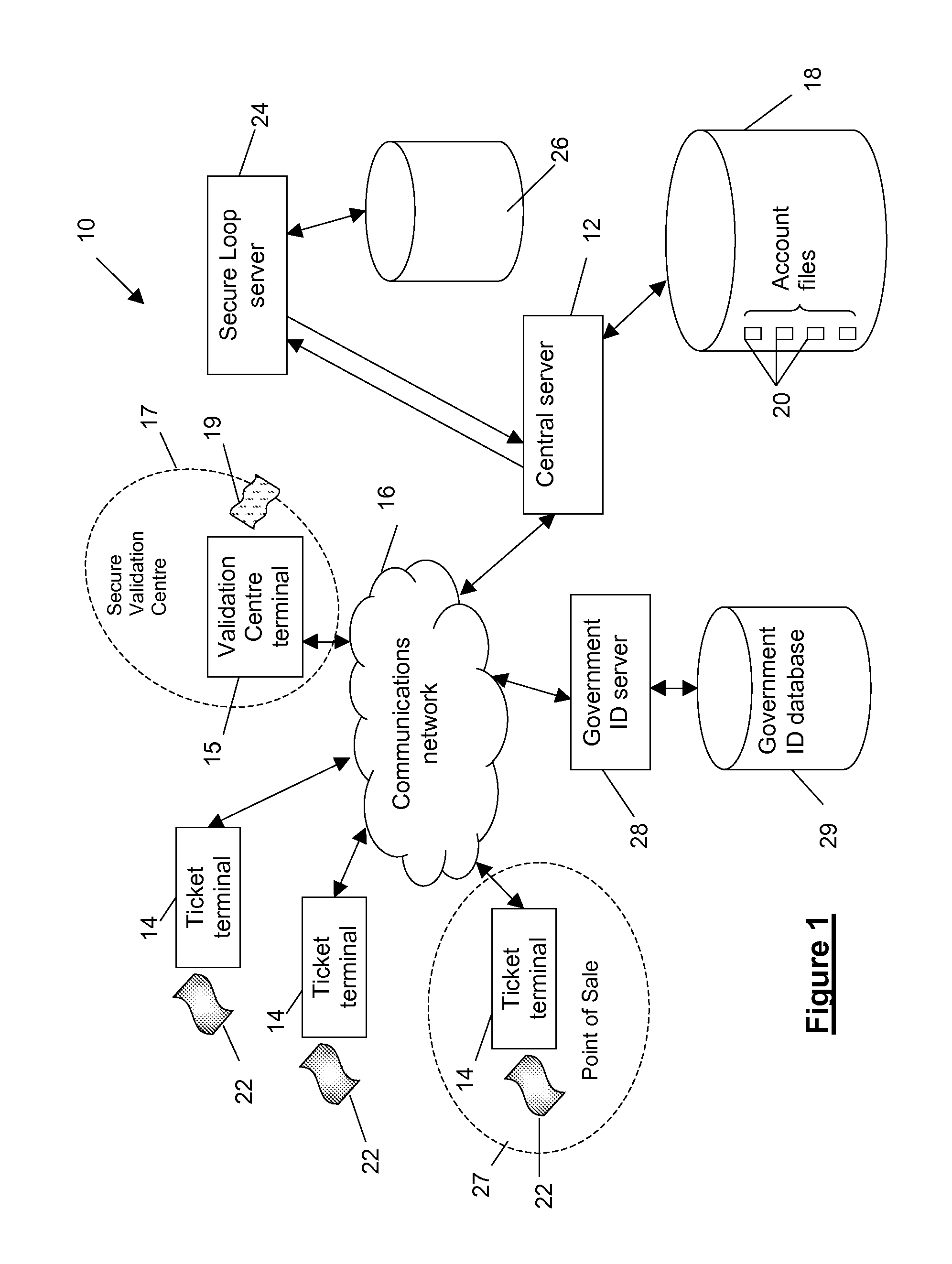
[0114]A first embodiment of the present invention is implemented on a terminal-based system 10 as shown in FIG. 1. The system 10 comprises a central server 12 and multiple lottery ticket terminals 14 in communication via a communications network 16 with the central server 12. The central server 12 has associated with it a central data store 18 in which are stored account files 20 relating to each of the authorised tickets 22 the ticket terminals 14 have issued. The account files 20 can be linked to a lottery or other form of prize draw event which is to take place at a given date and time. However, there are also other uses for the account files 20 which will become evident from the following description. The system also comprises a symbolic secure loop server 24 together with a corresponding local data store 26 which is used to further enhance the security of the decryption and encryption functionality of the central server (as will be explained in greater detail later).
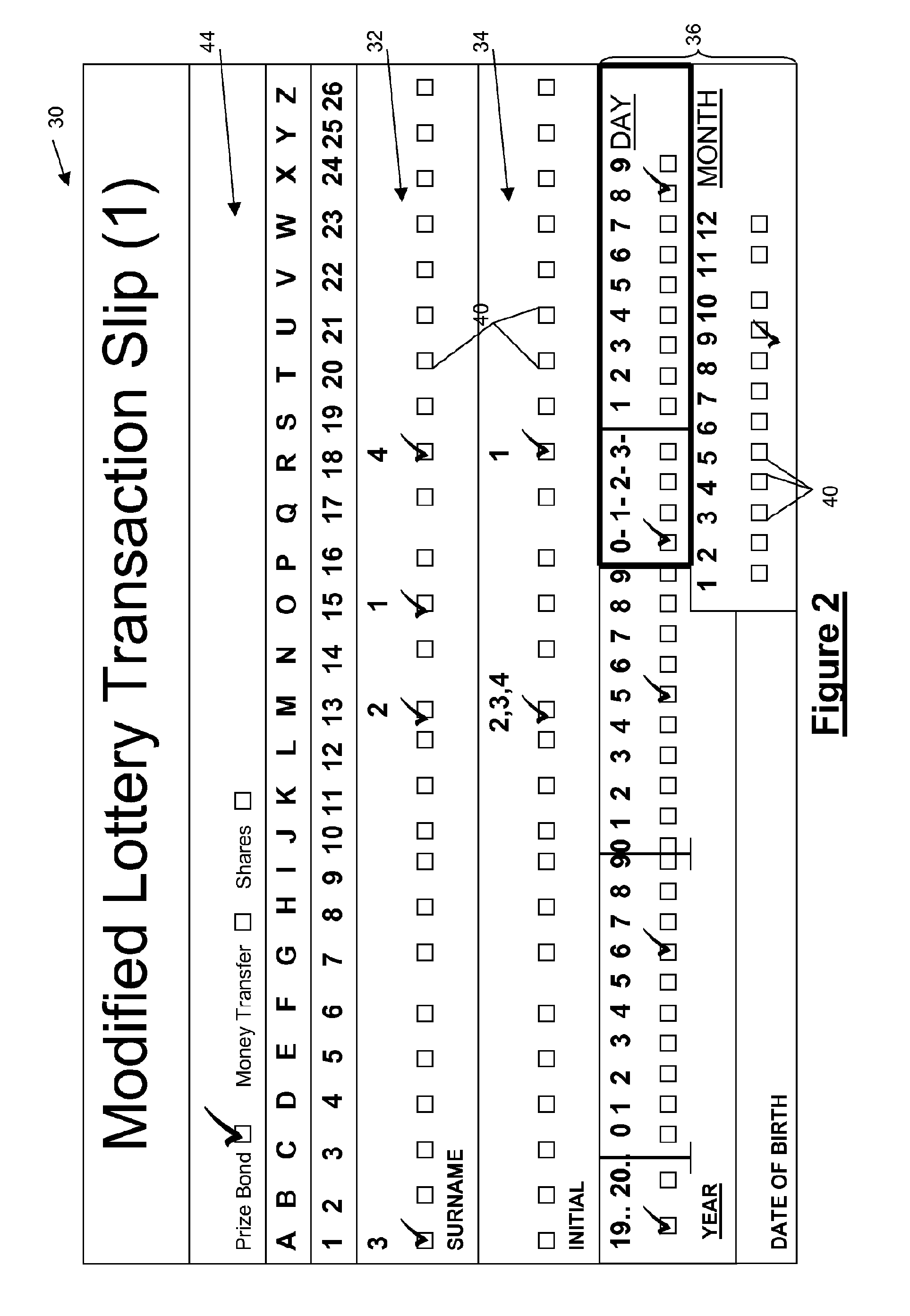
[0115]The t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com