Kernal-based intrusion detection using bloom filters
a technology of bloom filter and intrusion detection, applied in the field of kernal-based intrusion detection using bloom filter, can solve the problems of network infrastructures that are vulnerable to attack, network devices that are more vulnerable to attack, network devices that are easily damaged, etc., and achieve the effect of facilitating real-time detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
I. Overview
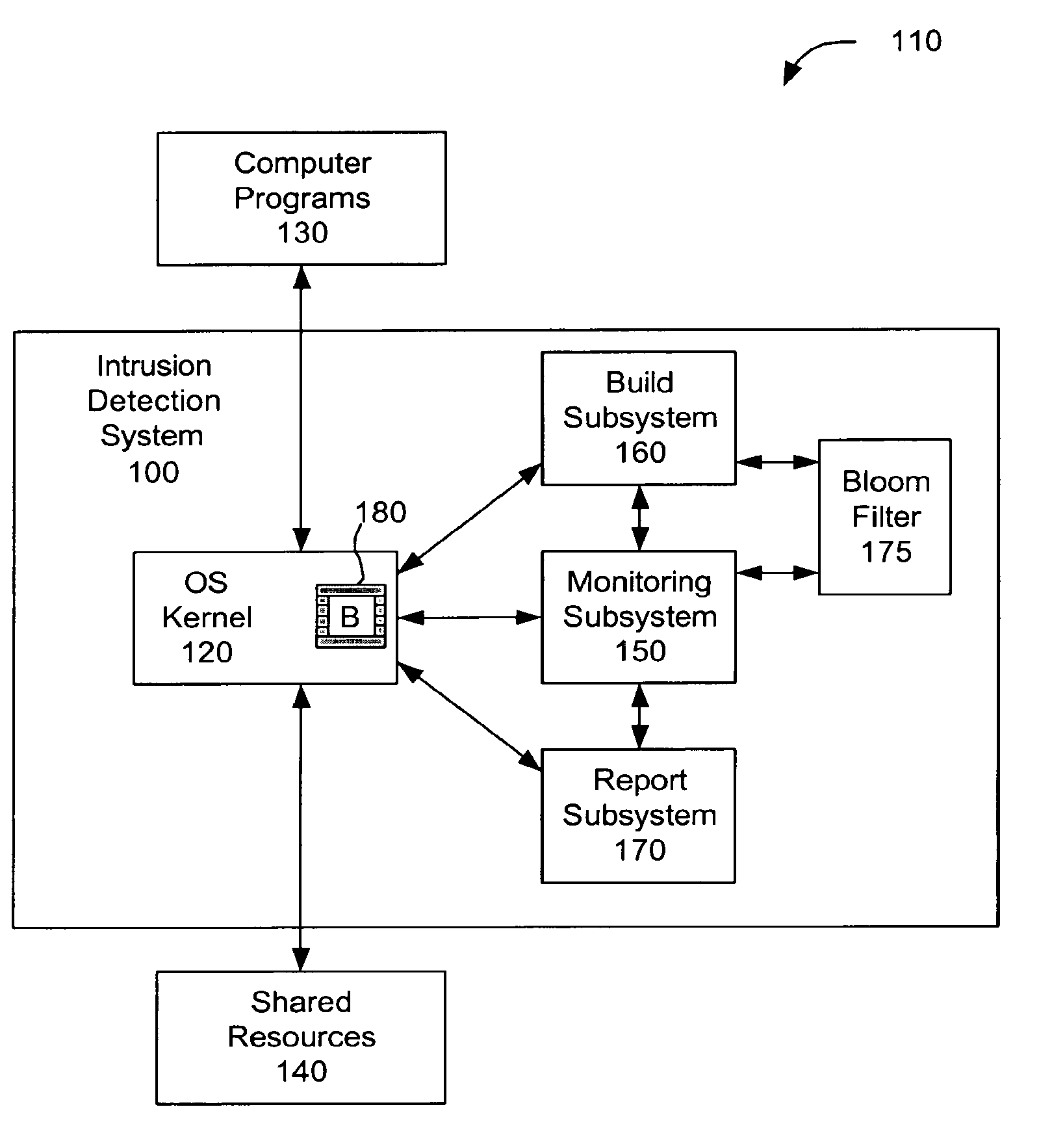
[0016]A system and method for kernel-based intrusion detection using Bloom filters are disclosed. More specifically, the disclosed system and method (collectively the “intrusion detection system”) use Bloom filters to detect intrusions (e.g., attacks from external sources) into computers or networks by monitoring the behavior of computer programs and comparing the monitored actual behavior with predefined Bloom filter data to identify any anomalous behavior that may indicate an intrusion attempt. The predefined Bloom filter data is representative of “normal” computer program behavior, which refers to behavior that is expected during operation of the computer programs when not subject to intrusion attempts.
[0017]The intrusion detection system may monitor behavior of a computer program by tracking system calls or system-call sequences (collectively “system-call behavior”) initiated by the computer program. As mentioned above, system calls refer to mechanisms used by compute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com