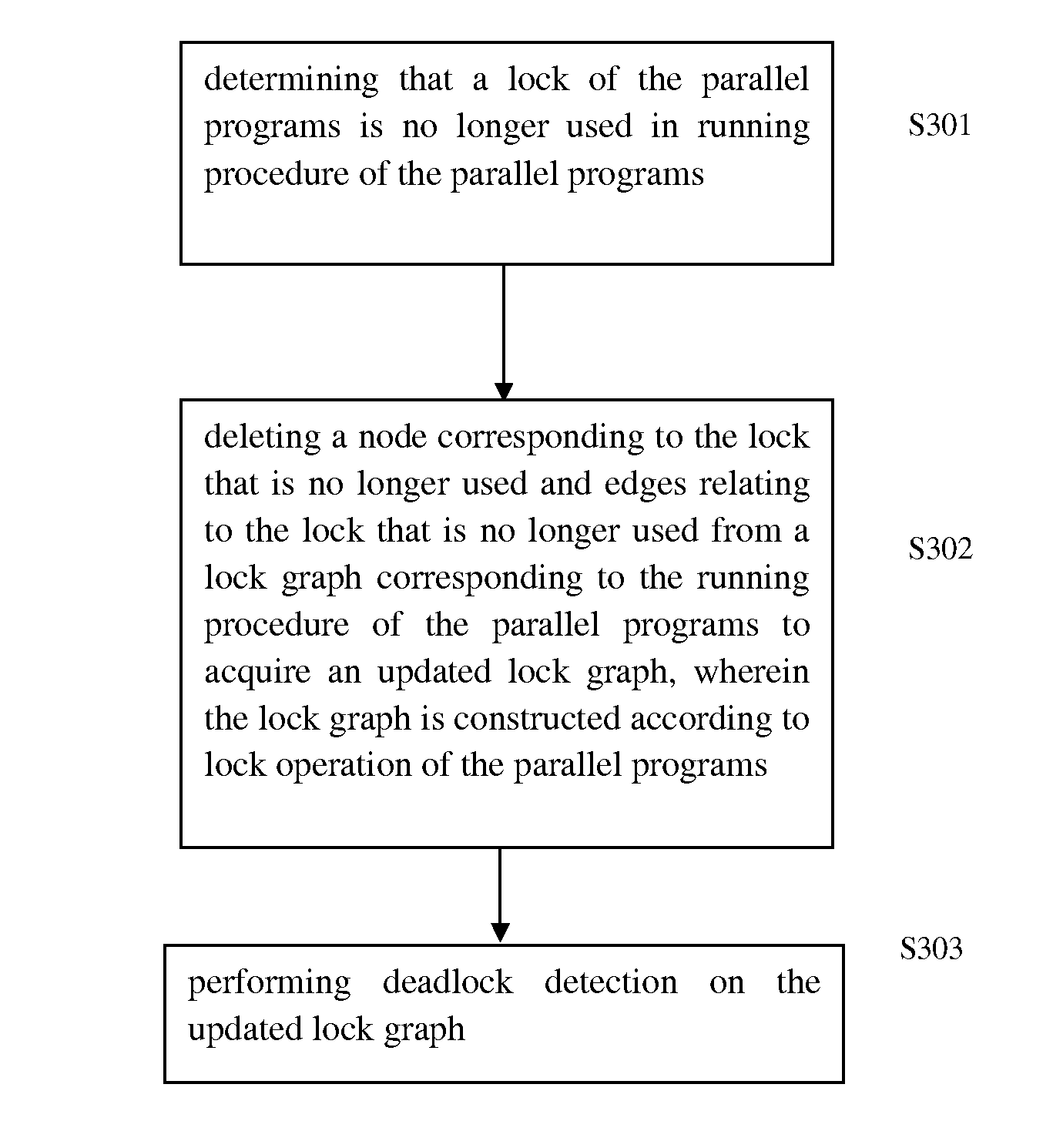
Deadlock detection method and system for parallel programs
a detection method and parallel program technology, applied in the field of parallel programs, can solve the problems of reducing affecting the performance of the algorithm, and the deadlock of the process (thread) is vital, so as to reduce the number of nodes, reduce the complexity of the algorithm, and save time and computing resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
[0033]An example of static code analysis on a c language program example1.c with an explicit function call to destroy a lock is shown below, in which the c language program example1.c contains the mutual exclusive lock Mutex in pthread library of Linux, and a function that destroys the mutual exclusive lock Mutex is: int pthread_mutex_destroy(pthread_mutex_t*mutex); static code analysis needs to scan source code of example1.c without executing the code, identify function code that matches the Mutex destroying function, identify locations that the lock is finally used in the running procedure of parallel programs, and add a mark in the vicinity of these locations to trigger an notification event that the lock is destroyed during running procedure of parallel programs.
1 :#controller thread, named as T12 : #include 3 :4 : pthread_mutex_t list_mutex;5 : pthread_mutex_t request_mutex;6 : pthread_mutex_t control_mutex;7 :8 : void controller_thread( )9 : {10 : ...11 : / / create worker_thr...
second embodiment
[0037]An example of static code analysis on a Java language program example2.java without an explicit function call that destroys a lock is shown below.
/ * main in Example2.java * / 01: new T1.start( );02 new T2.start( ); / * Thread 1, named as T1 * / 03: synchronized(G){04: synchronized(L1){05: synchronized(L2){ }06: }07: };08: t3 = new T3( );09: t2.start( );10: t3.join( );11: synchronized(L2){12: synchronized(L1){ }13: }14: / * Thread 2, named as T2 * / 15: synchronized(G){16: synchronized(L2){17: synchronized(L1){ }18: }19: }20: / * Thread 3, named as T3 * / 21: synchronized(L1){22: synchronized(L2){ }23: }24:
[0038]There is no explicit function call that destroys locks (G, L1 and L2) in the above example of Java language program, thus it is required to analyze the data stream of parallel programs to determine locations in the parallel programs where the lock is defined and used so as to find a set of locations where the lock may be finally used in the running procedure of parallel pro...
third embodiment
[0049]An example of dynamically analyzing byte code of Java language program Example3.java running on a JVM (Java virtual machine) by using garbage collection is shown below.
/ * main in Example3.java * / 1:2:3: new T1( ).start( ); / / start thread T14:5: T1:6:7: synchronized(G) {8: synchronized(L1) {9: synchronized(L2) {10: }11: }12: new T2( ).start( ); / / start thread T213: ...14: / / lock G is garbage collected at this moment15:16: T2:17:18: synchronized(L1) {19: synchronized(L2) { }20: }21: ...22 / / lock L1 is garbage collected at this moment
[0050]First, objects of locks G, L1 and L2 that require to be notified when reclaimed by GC are registered on the virtual machine, in response to receiving an event notification issued from JVM that lock G is reclaimed. When the. Java program proceeds to instruction at line 14, it is determined that lock G is no longer used. FIG. 6a shows a lock graph of Java program running on JVM corresponding to the third embodiment, nodes of lock G and edges ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com