Coordinate access control system of ternary structure
An access control and peer-to-peer technology, applied in transmission systems, electrical components, user identity/authority verification, etc., can solve the problems of network security, complex process of trust relationship establishment, and limited flexibility of access forms. The effect of high safety and safety performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
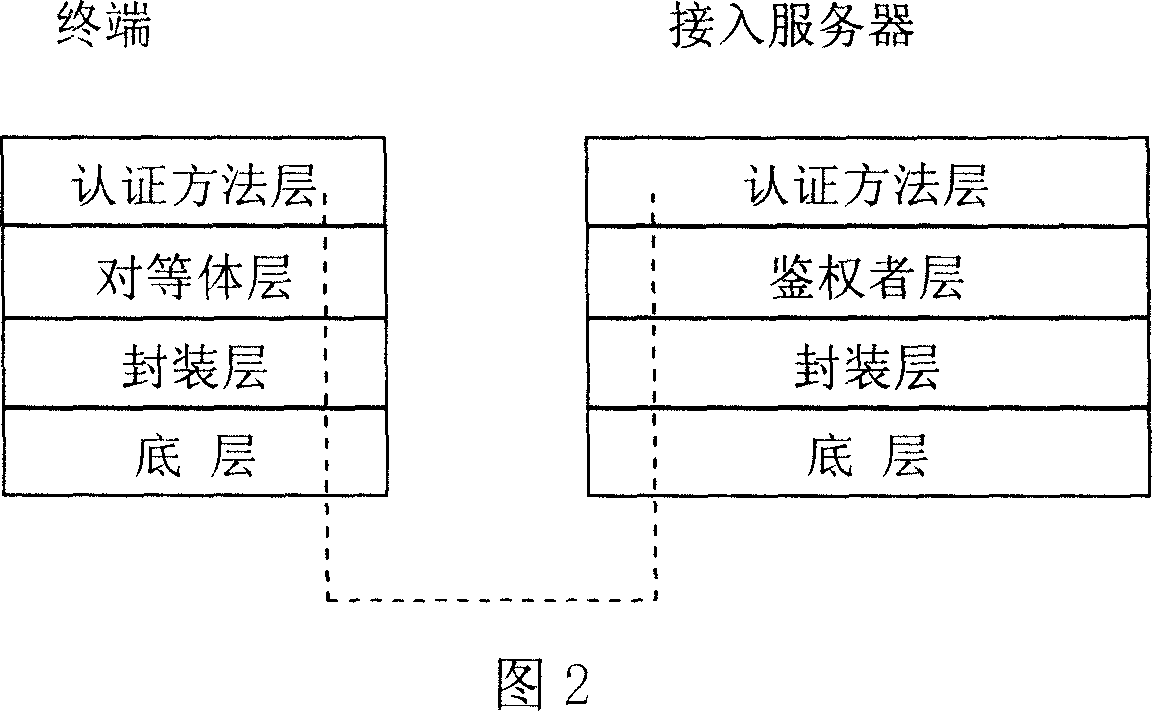
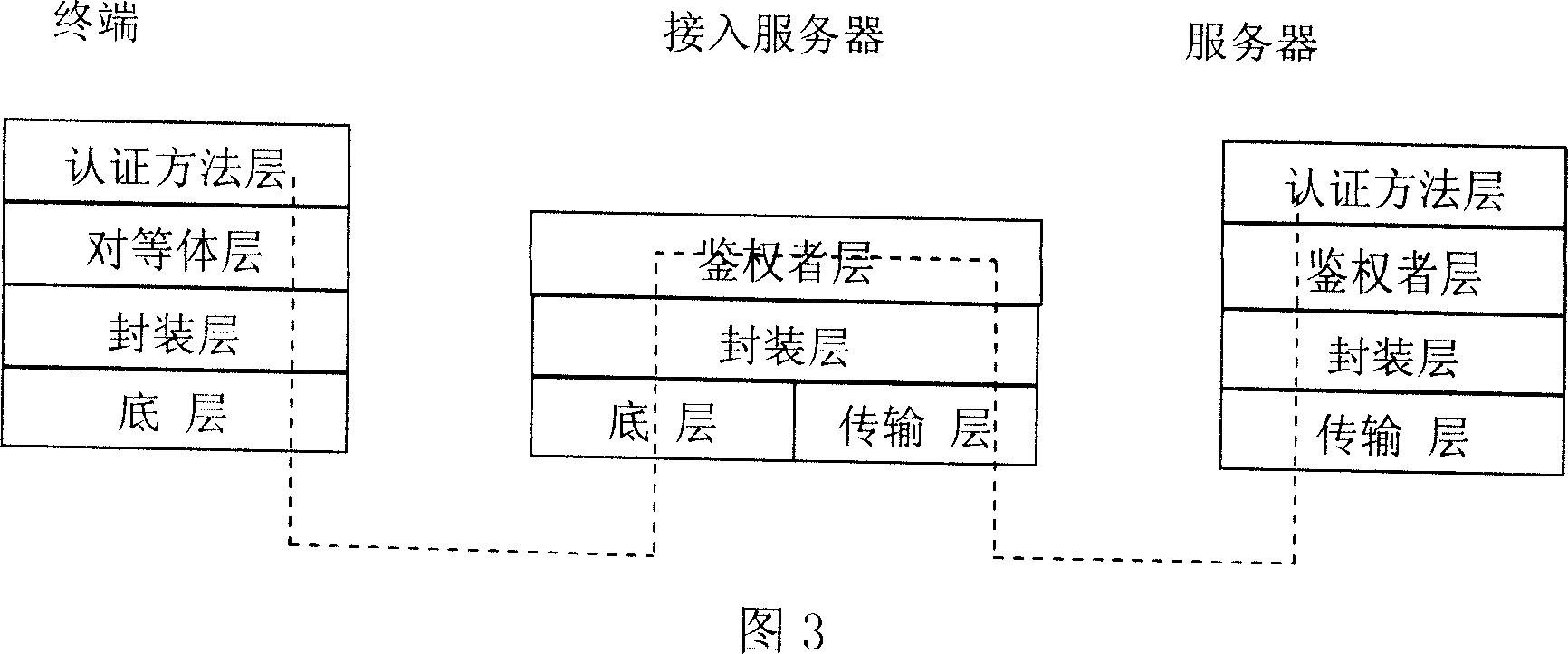
[0037] The specific structure of the peer-to-peer access control system of the present invention is shown in Figure 4, including a terminal, an access controller and a server. The peer layer (corresponding to the peer layer of the subject) and the authentication method layer (corresponding to the authentication method layer of the subject), the access controller (corresponding to the authenticator) includes the bottom layer (corresponding to the bottom layer of the authenticator), the transport layer ( Transport layer corresponding to the authenticator), encapsulation layer (encapsulation layer corresponding to the authenticator), authenticator layer (authenticator layer corresponding to the authenticator) and authentication method layer (authentication method layer corresponding to the authenticator) , the server includes a transport layer (corresponding to the transport layer of the authentication server), an encapsulation layer (corresponding to the encapsulation layer of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com