Key consulting method and its system for customer end and server
A key negotiation and server technology, applied in the field of client and server key negotiation methods and systems thereof, can solve the problems of easy interception of login passwords, insecurity, and easy interception of communication passwords.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
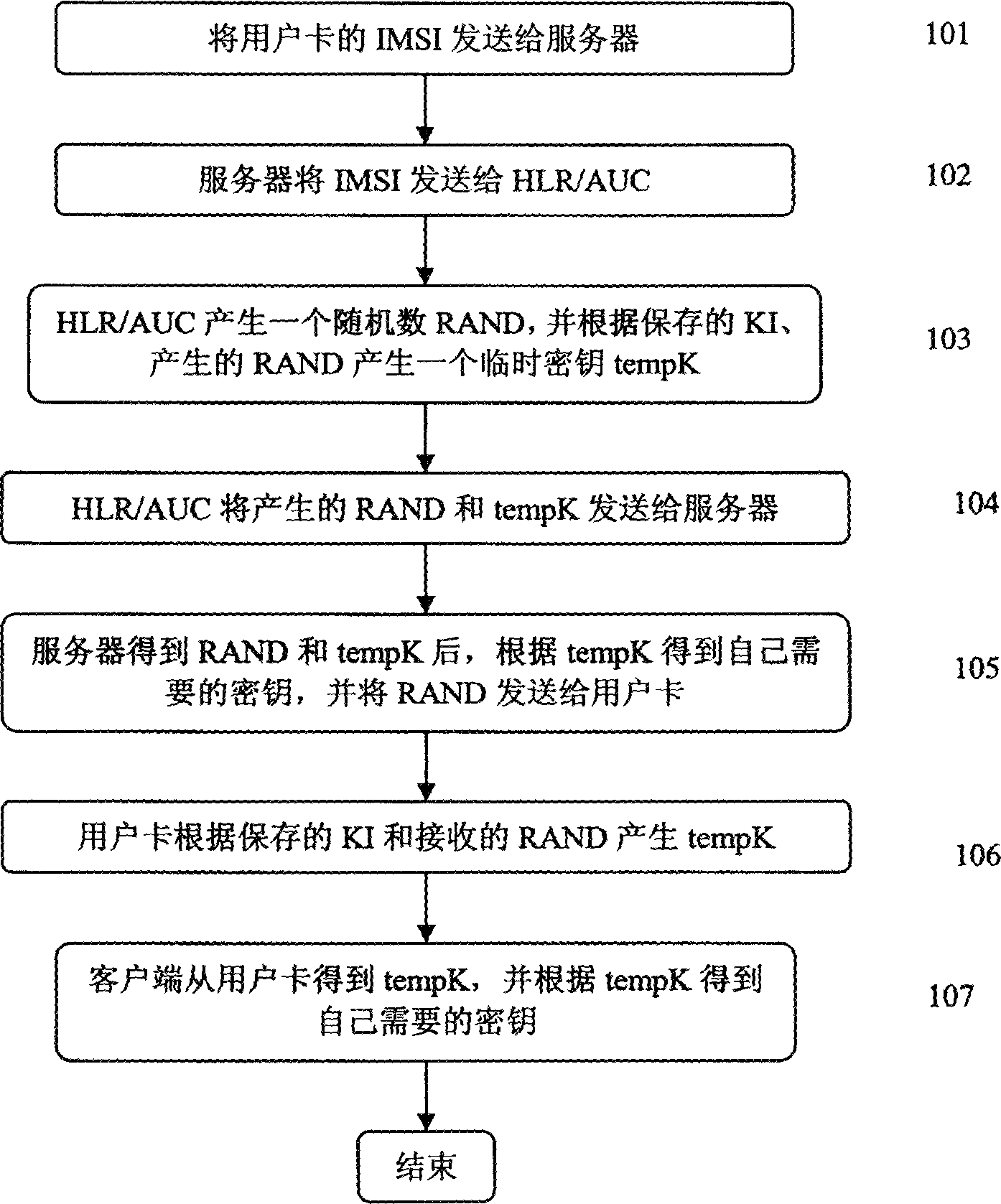
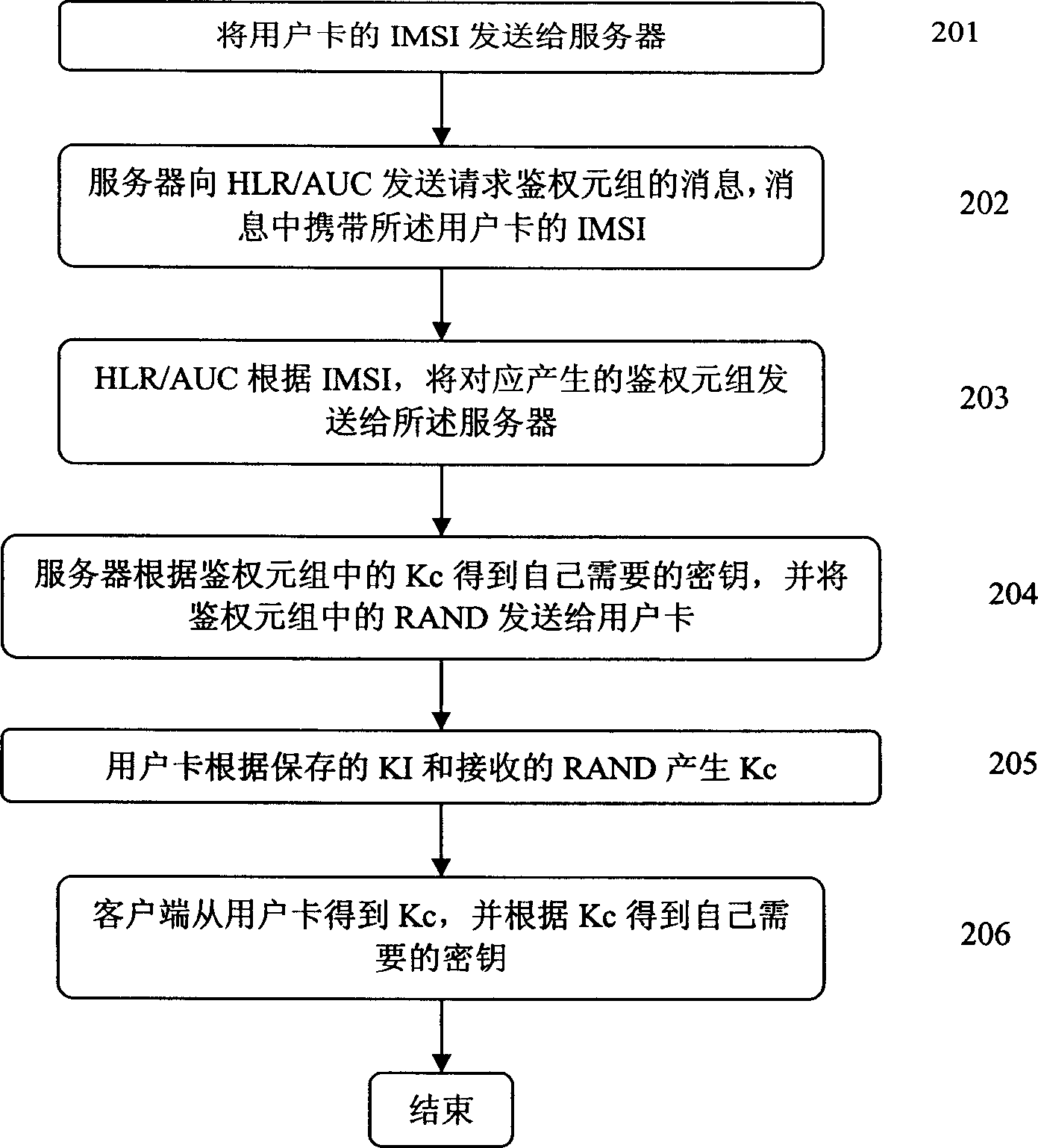
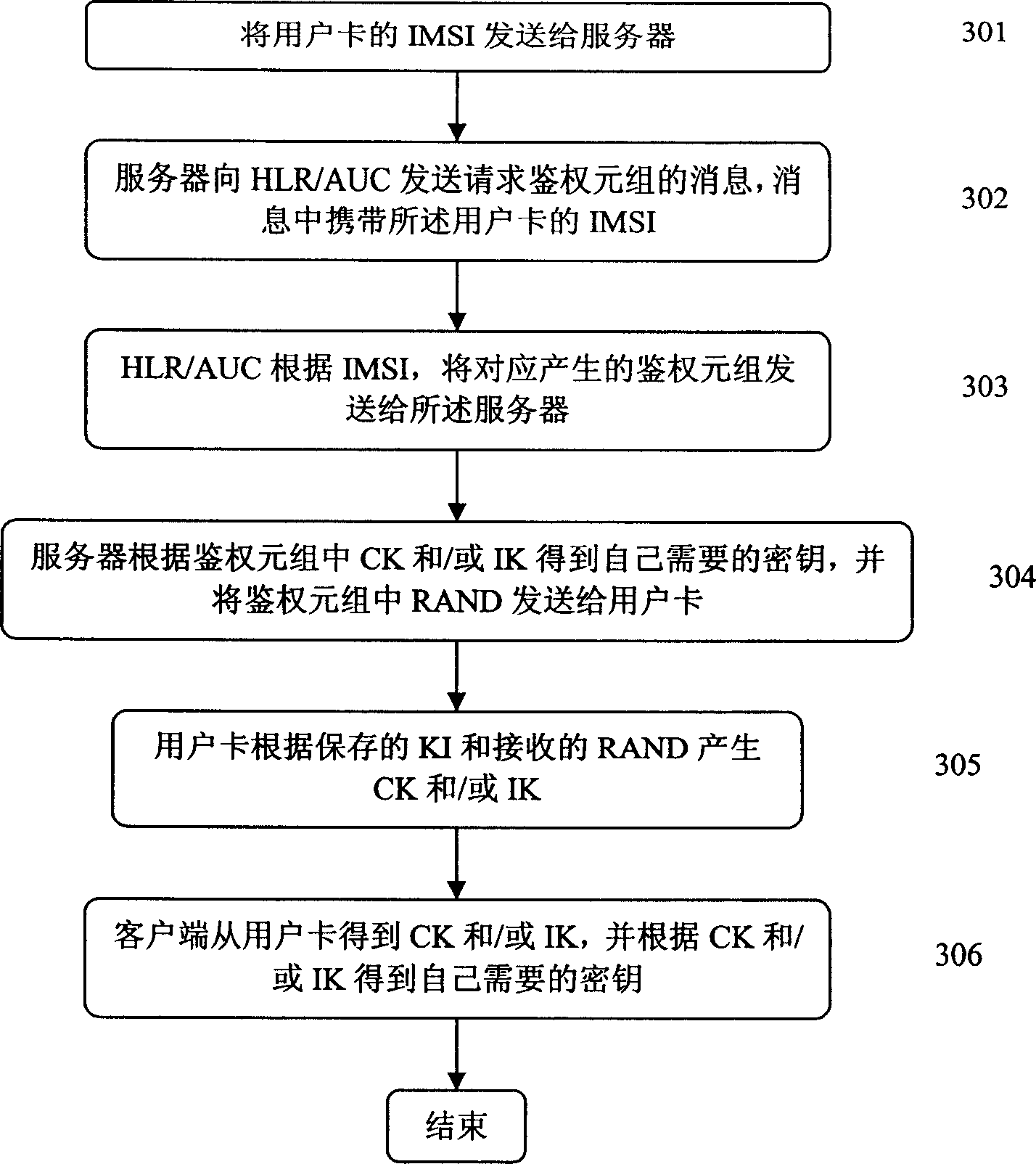
[0056] According to the key agreement method described in the present invention, the client generates the key it needs to negotiate according to the authentication key KI stored in the user card, and the server generates the key it needs to negotiate according to the authentication key KI stored in HLR / AUC. The negotiated key. The server requests the generated authentication tuple from the HLR / AUC, and the server can simulate a roaming MSC / VLR requesting the authentication tuple from the HLR / AUC when the server generates the authentication tuple. When generating the authentication tuple, the server first generates a random number RAND, and generates the authentication tuple according to the RAND and the KI stored by itself. According to the authentication tuple, the server contains the temporary key needed when the server and the client negotiate the key. For example, the temporary key can be the encryption key Kc for the 2G GSM system, and for the 3G WCDMA system , which can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com