Terminal user identity authentication and link system based on Internet
An identity authentication and end-user technology, applied in user identity/authority verification, transmission system, data exchange through path configuration, etc., can solve problems that affect business development, unreliability, and network users cannot establish trust relationships
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
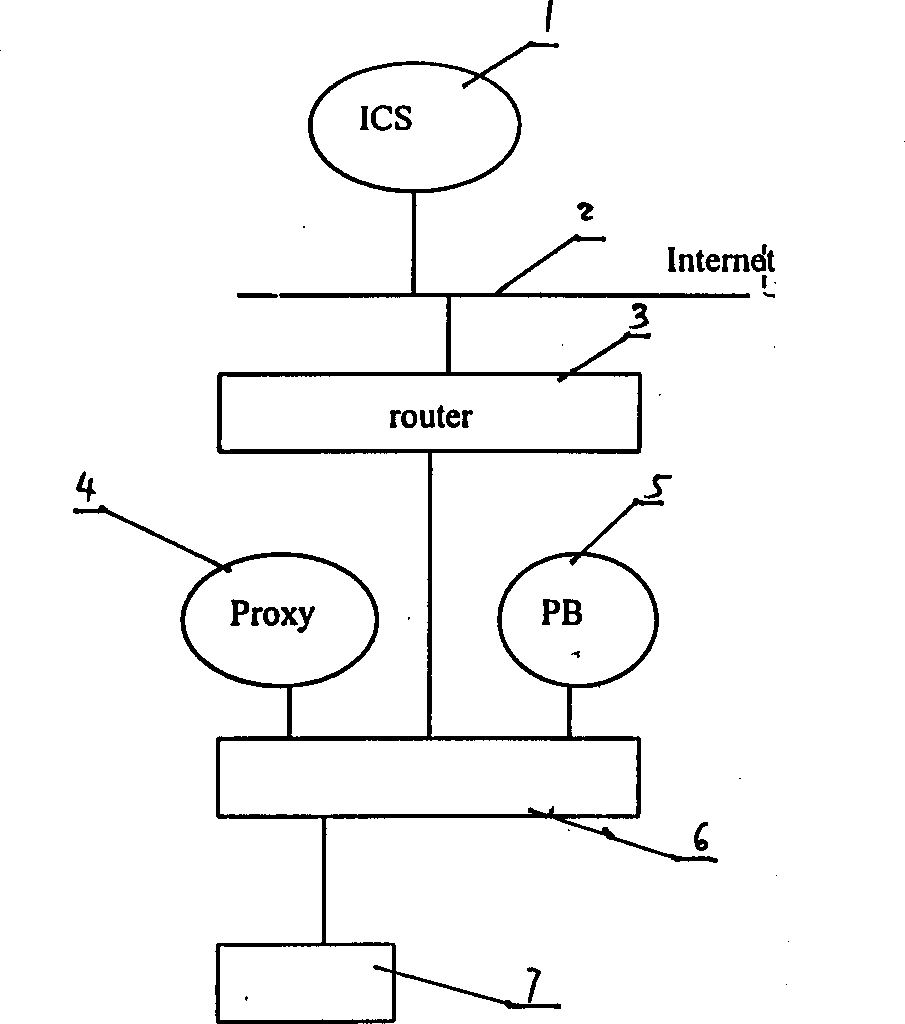
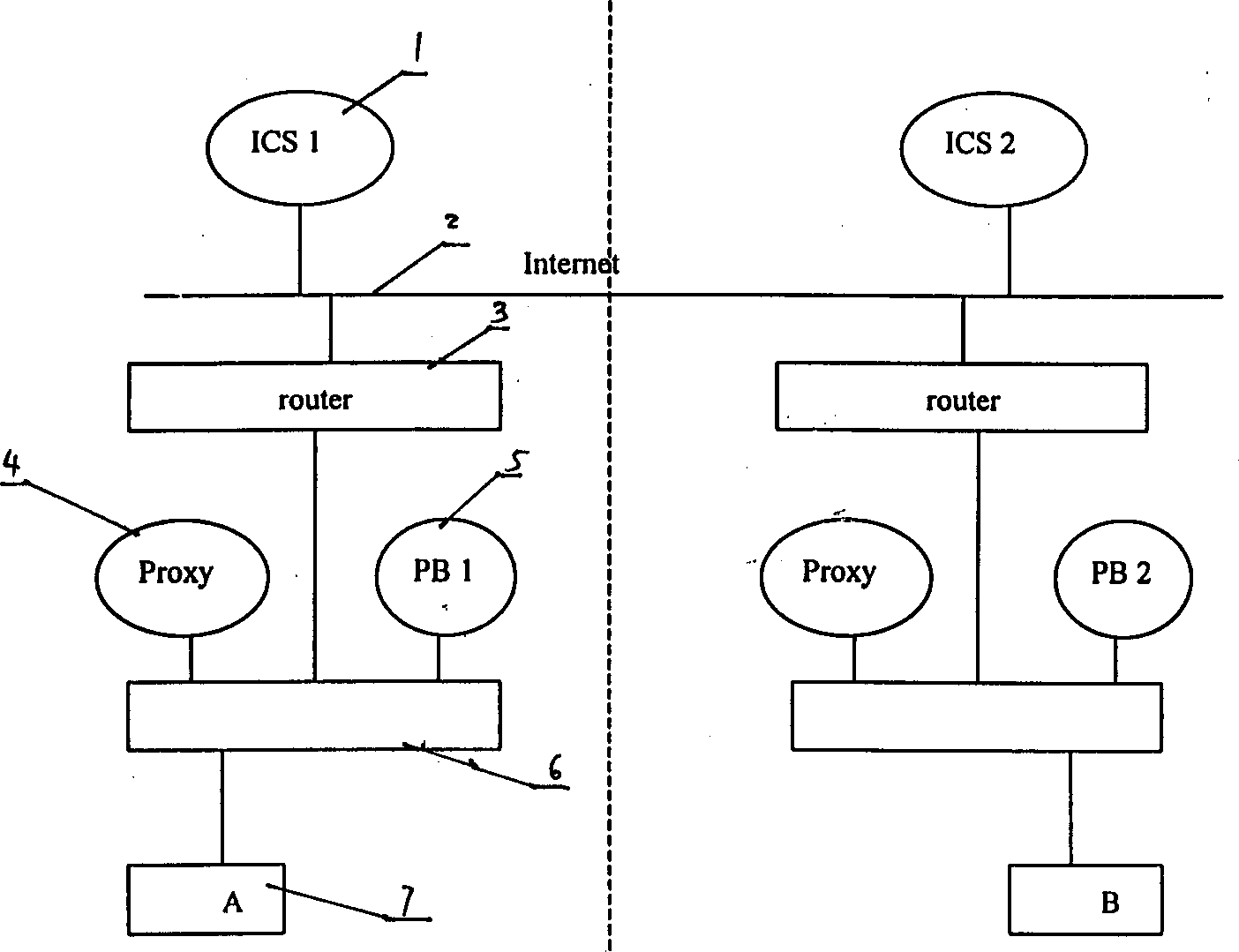
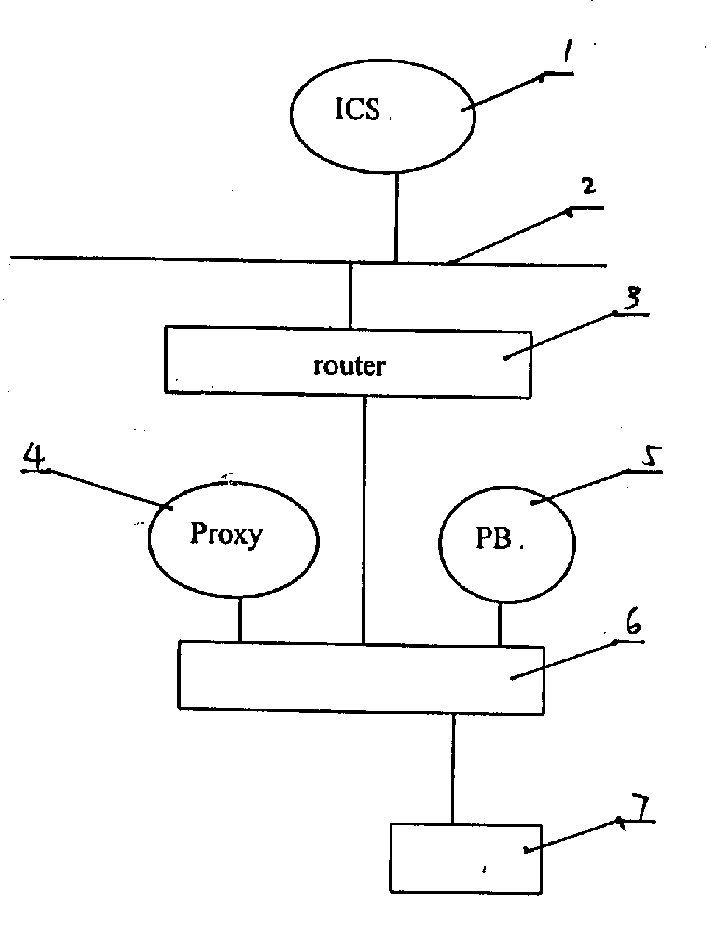
[0010] The operator management network structure managed by the identity authentication system is the prerequisite for identity authentication. Within a direct management scope, the user is unique. The user data within the same operator can be updated dynamically, and the interactive user data information can be updated at any time according to the data update between the management connection nodes. Set the code parser on the operator's registration server to provide a basis for the selection of communication channels. Each operator registration server has a list of operators, countries, and home regions. Country and region are unified for different operators. In the same country and region, different operators can manage users under their jurisdiction. Country code: The current internationally unified country code can be used, and the area code, user code and operator code are determined by the relevant agencies of the country, but the area code and user code must not use ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com