Method and system for realizing soft cipher module, storage medium and terminal
A technology for cryptographic modules and cryptographic services, applied in the field of implementing soft cryptographic modules, can solve problems such as key storage problems, and achieve the effect of ensuring confidentiality and integrity requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
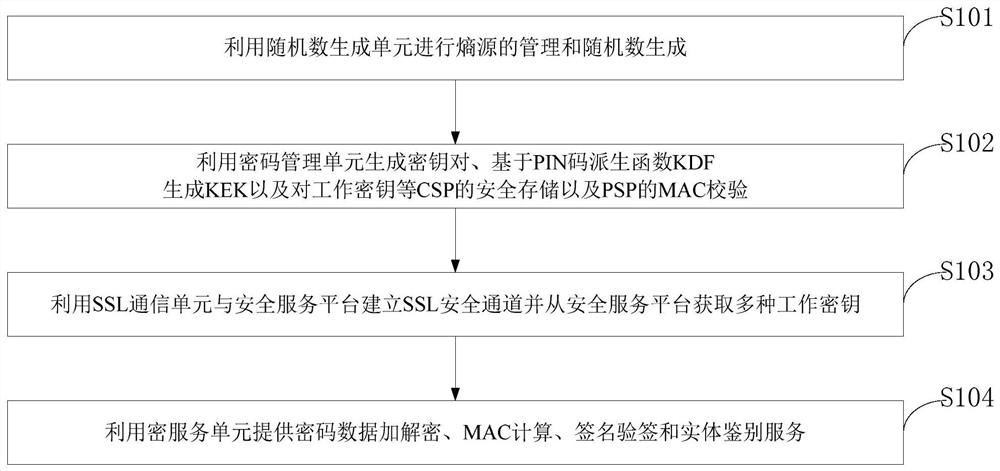
[0065] like figure 1 As shown, the method for implementing a soft cryptographic module provided by the embodiment of the present invention includes the following steps:
[0066] S101, using a random number generating unit to manage the entropy source and generate random numbers;
[0067] S102, utilize the key management unit to generate a key pair, generate KEK based on the PIN code derivation function KDF, and the safe storage of CSPs such as working keys and the MAC verification of the PSP;
[0068] S103, use the SSL communication unit and the security service platform to establish an SSL communication security channel and obtain multiple working keys from the security service platform;
[0069] S104, using a cryptographic service unit to provide cryptographic data encryption and decryption, MAC calculation, signature verification and entity authentication services.
Embodiment 2
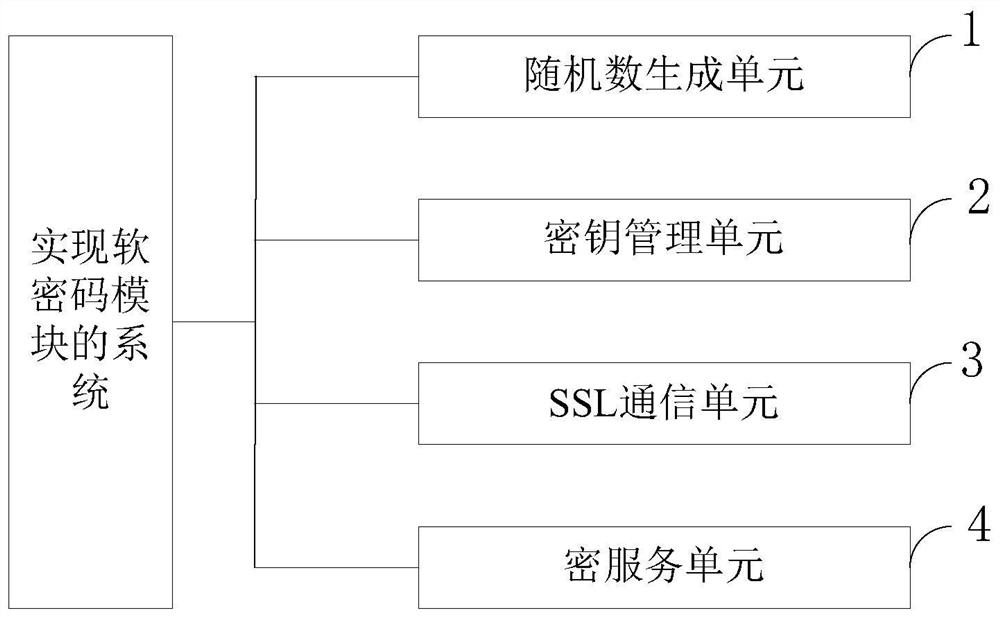
[0071] like figure 2 As shown, the system for realizing the soft cryptographic module provided by the present invention includes:
[0072] Random number generation unit 1, for managing the entropy source and generating random numbers;
[0073] The key management unit 2 derives the KEK through the PIN code, and securely stores the CSP and the PSP;
[0074] The SSL communication unit 3 is used to establish an SSL security channel with the security service platform, and obtain the working key from the security service platform;
[0075] The cryptographic service unit 4 is used to provide entity authentication, data encryption and decryption, signature verification and MAC calculation services.
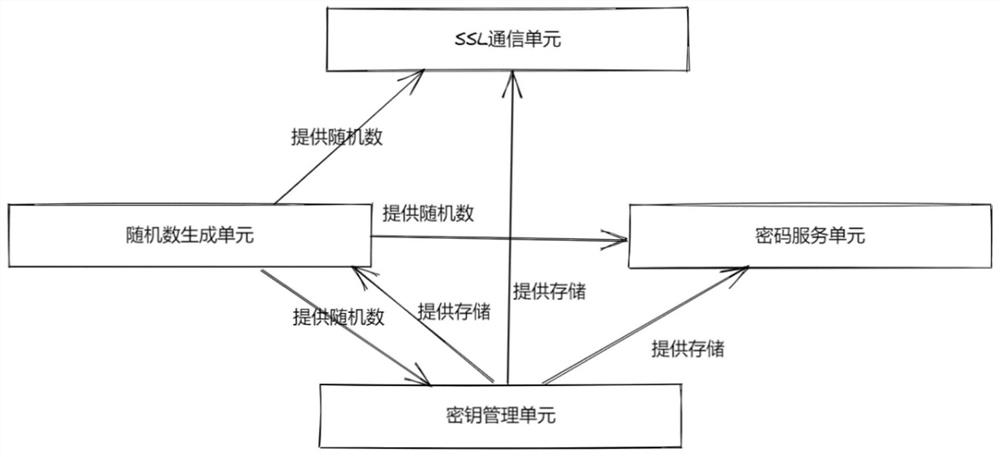
[0076] image 3 This is the system principle for implementing the soft cryptographic module provided by the embodiment of the present invention.
Embodiment 3
[0078] The method for implementing a soft cryptographic module provided by the embodiment of the present invention includes: a random number generating unit generates a random number and a public-private key pair, obtaining a working key from a security service platform through an SSL communication unit, and a key management unit using a PIN code and a salt value (The random number generated by the random number generation unit) derives the private key protection key and the HMAC key respectively. The former is used to encrypt the key security parameters (CSP) such as the work key, private key and random number to ensure its confidentiality; It is used by the user to perform MAC verification on public security parameters (PSP) such as public key, salt value and threshold of deterministic random bit generator (DRNG) to ensure its integrity; the cryptographic service unit decrypts and obtains the working key to provide cryptographic services for the application , and then destroy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com