Potential sudden criminal person identification method based on assumed evaluation and Bayesian learning
A Bayesian learning and person identification technology, applied in neural learning methods, computer systems based on knowledge-based patterns, and kernel methods, etc., can solve problems such as inability to prevent in advance, no analysis and modeling, and difficult identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
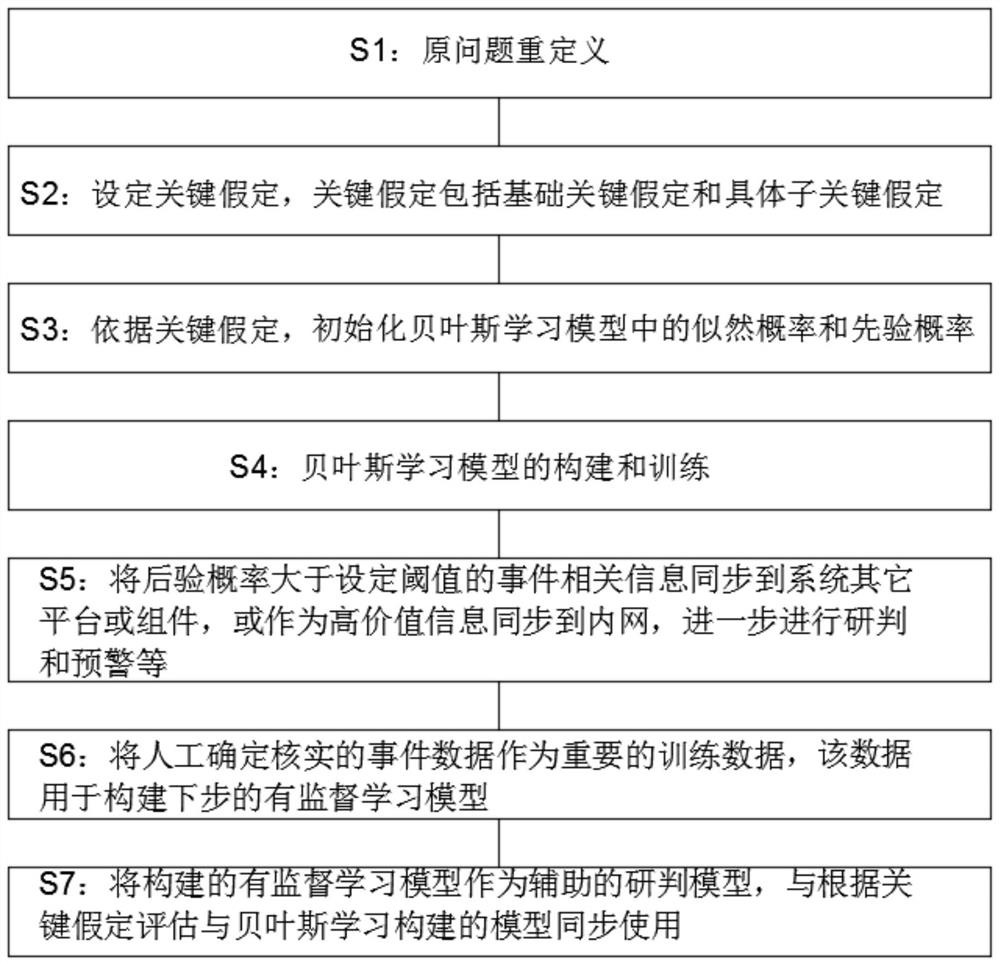
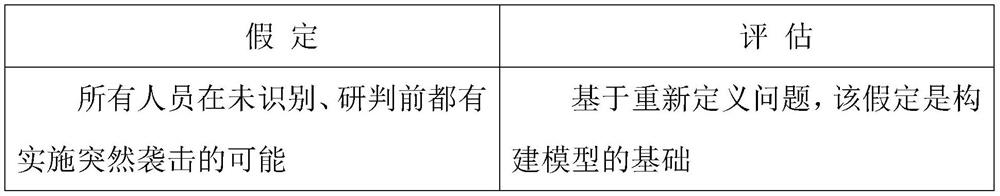
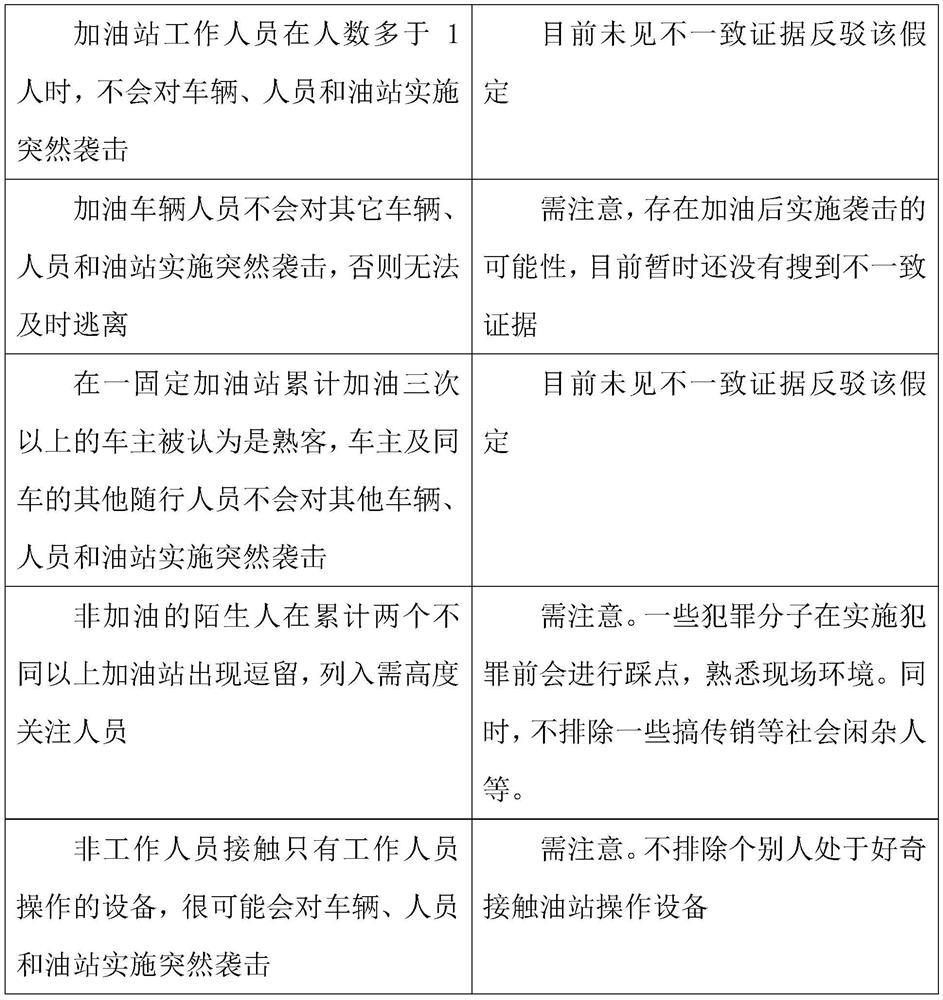
[0024] The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, but not all of the embodiments. The accompanying drawings and the embodiments are only used for illustrative description, and should not be construed as a limitation on the present patent. The present invention will be further described below with reference to the accompanying drawings and the embodiments.
[0025] Taking the gas station refueling scene as an example, it is reported that some people (non-vehicle owners) will suddenly pull out the fuel gun that is refueling, and use the lighter they carry with them to ignite the fuel gun, then burn the vehicle and flee the scene. Power departments and gas companies need to know "Is there a way for dangerous elements to preven...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com