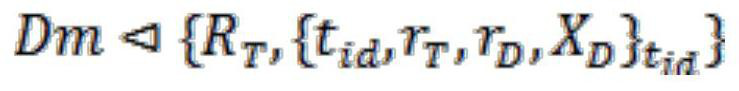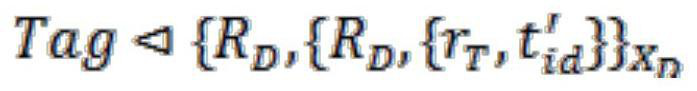Radio frequency identification system security authentication protocol based on ECC
A radio frequency identification system, security authentication technology, applied in the field of radio frequency identification system security authentication protocol, can solve privacy security threats, limited computing power, cost constraints and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
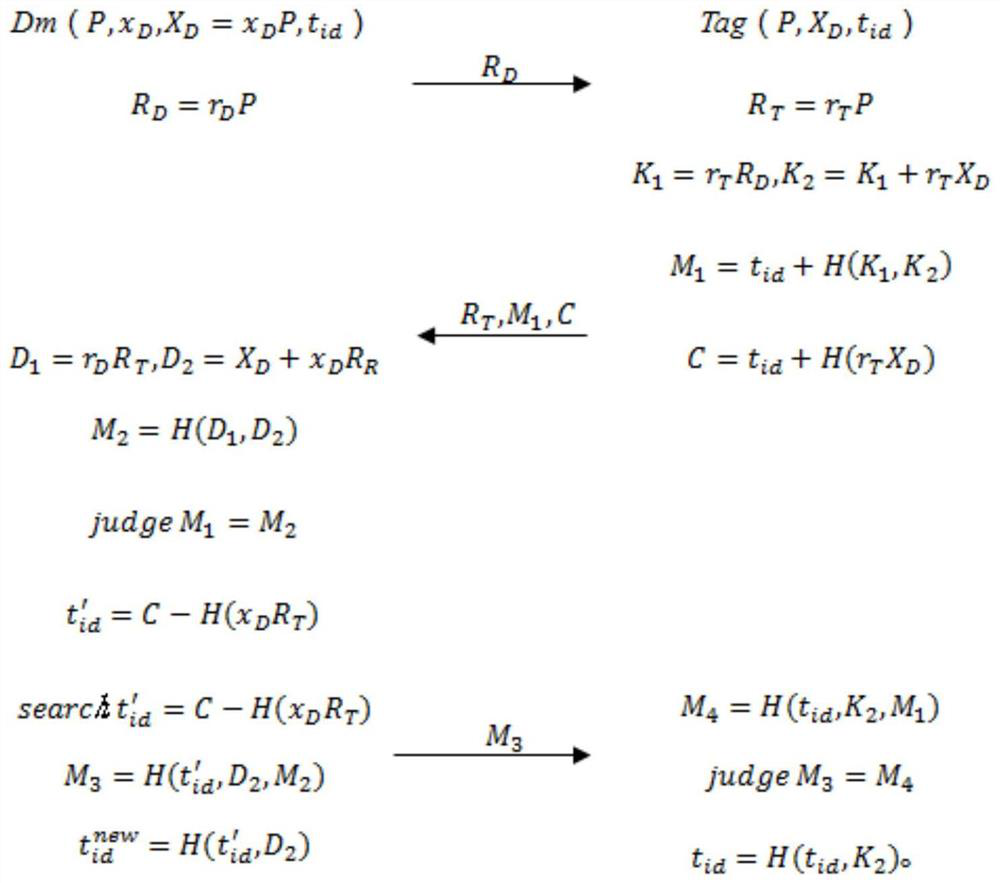
[0083] The protocol of the present invention performs the authentication process as follows:
[0084] First initialize the radio frequency identification system, using the public elliptic curve Secp256r1 parameters:
[0085] p=11579208921035624876269744694940,
[0086] a=11579208921035624876269744694937,
[0087] b=41058363725152142129326129780047,
[0088] P=(77329208548912624877826144612976, 78546487135463583287471836582647)
[0089] ①The reader generates the private key x D =6481648976871649785487158932158, then the reader calculates and generates the public key:
[0090] X D =x D P=(64532793678598714581687648731269,4871652169628452379122791561234), then assign an identifier to the electronic label
[0091] t id =64532793678598714581687648731269;
[0092] ②The reader generates a random number r D =92147648128924531715864325416972, and calculate R D =r D P=(21354700811932764913702964767183, 93254602933752849366400636085063), and set R D and the communication req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com