Vulnerability severity assessment method and system based on vulnerability event argument
A technology of severity and vulnerability, which is applied in the vulnerability severity evaluation method and system field based on vulnerability event arguments, and can solve problems such as unbalanced data sets, incomplete features, and large differences in the number of the same index
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
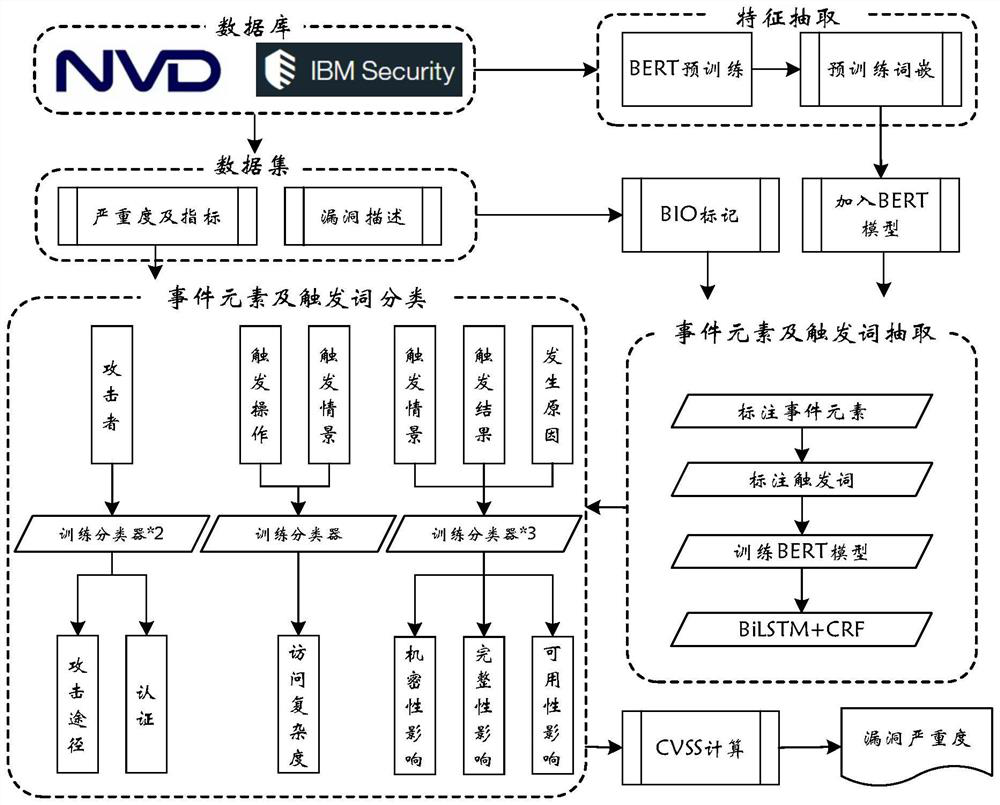
[0041] see figure 1 As shown, a vulnerability severity assessment method based on a vulnerability event argument provided by the present invention includes the following steps:
[0042] 1) There are multiple different vulnerability databases. According to the CVE-ID, the vulnerability reports are crawled from two of the multiple different vulnerability databases, namely the vulnerability database NVD and the vulnerability database IBMX-Force, to obtain the description text, Vulnerability severity level, vulnerability severity index, the cause of the vulnerability, attacker, triggering operation, triggering result, and triggering scenario are used as event arguments to construct an event argument label set;
[0043] Use the BIO tagging method to manually label the cause of the vulnerability, attacker, trigger operation, trigger result, and trigger scenario. B (Begin) indicates that the word is the word at the beginning of the vocabulary, I (Inside) indicates that the word is th...
Embodiment 2
[0066] Corresponding to the vulnerability severity assessment method based on vulnerability event arguments in Embodiment 1, this embodiment 2 provides a vulnerability severity assessment system based on vulnerability event arguments. Please refer to figure 1 As shown in the figure, it includes the argument label set module, the pre-training word embedding module, the extraction vulnerability event argument module, and the classification calculation module;
[0067] The argument label set module is used to crawl vulnerability reports from two of the multiple different vulnerability databases, namely the vulnerability database NVD and the vulnerability database IBMX-Force according to the CVE-ID, and obtain the description text and the severity of the vulnerability in the vulnerability report. Vulnerability level and vulnerability severity index, the cause of the vulnerability, attacker, triggering operation, triggering result, and triggering scenario are used as event arguments...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com