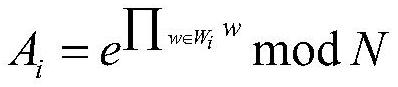Pairing-free searchable encryption method supporting revocation and verification
An encryption method and encryption index technology, which is applied to user identity/authority verification and key distribution, can solve the problems of undiscussed key revocation, etc., and achieve the effect of fast operation speed, high security, and low calculation cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
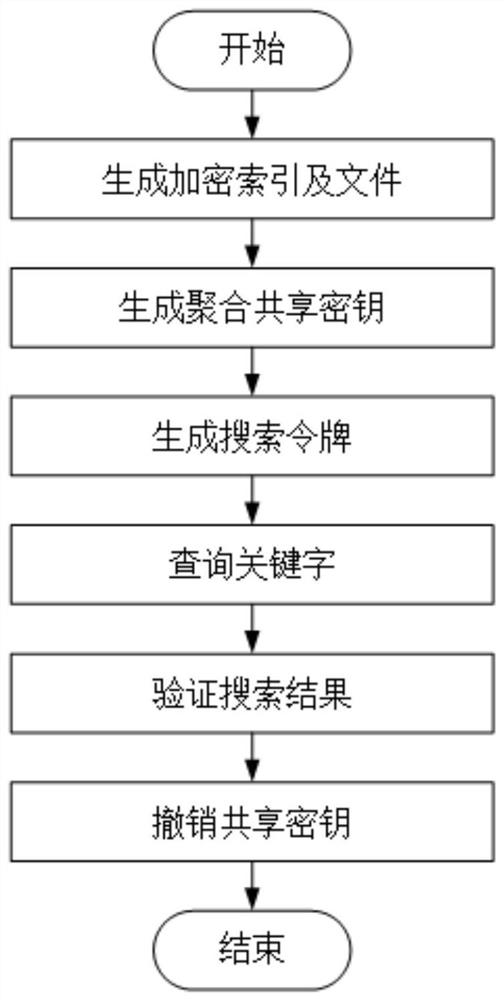
[0104] The unpaired searchable encryption method supporting revocation and verification of this embodiment consists of the following steps (see figure 1 ):
[0105] (1) Generate encrypted indexes and files
[0106] The methods for generating encrypted indexes and files are as follows:
[0107] 1) Data owners from the group of p-order integers Select the private key α from , and determine the public key β as follows:
[0108] β=g α
[0109] where g is the group from order p A random element selected in , p>2 λ , λ is a parameter, λ is a finite positive integer, and the value of λ in this embodiment is 80.
[0110] 2) Determine the accumulator A as follows i :
[0111]
[0112] N=q 1 ×q 2
[0113] Among them, W i Represents the keyword set, i∈{1,2,...,n}, n represents the number of documents uploaded by the data owner, n is a finite positive integer, n in this embodiment is 1000, and w is the keyword set W i keyword in , q 1 , q 2 is a randomly selected lar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com