Intrusion study and judgment method and system based on Web log
A log and unified technology, applied in the Internet field, to achieve the effect of improving efficiency, high log parsing power, and convenient secondary analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
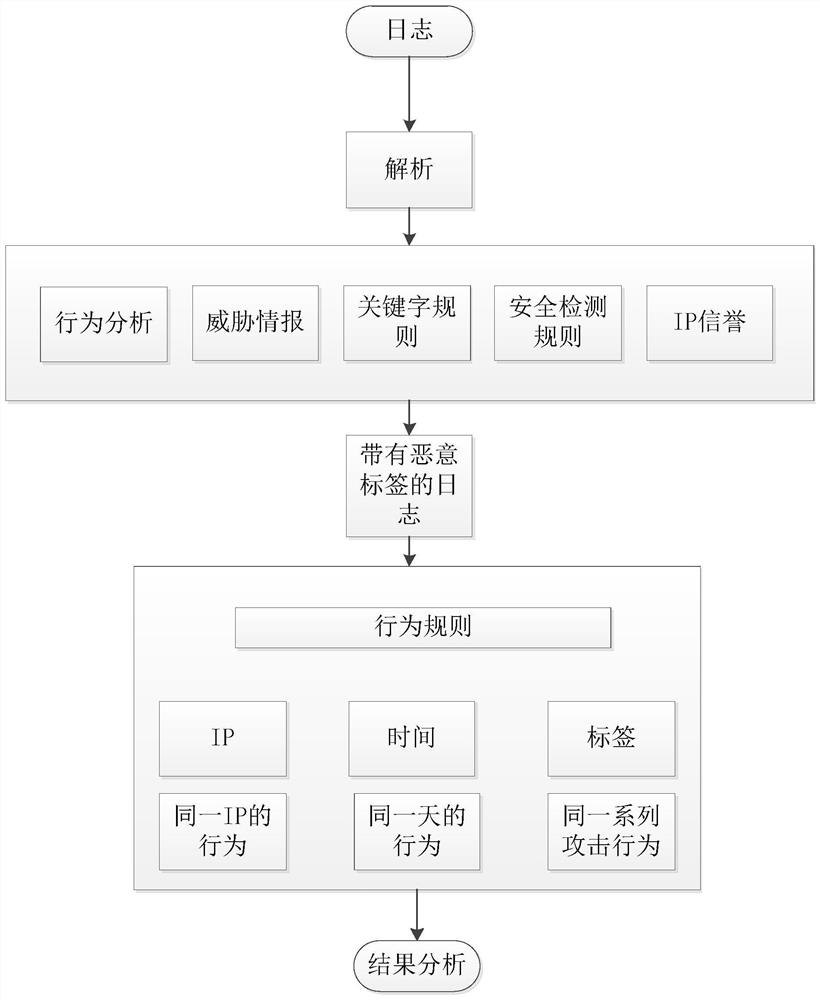
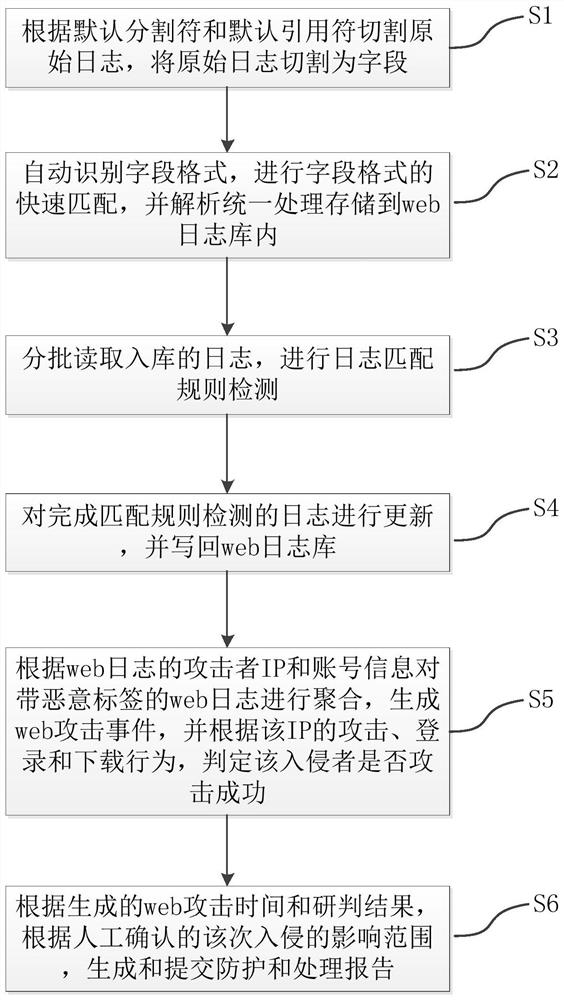
[0038] The present invention provides an intrusion research and judgment method based on Web logs. By cutting web logs, unifying analysis, rule matching detection, and log aggregation, the intrusion research and judgment of the attacker's IP is realized, which effectively solves the problem of low efficiency of manual web log research and judgment. Workload problem. The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
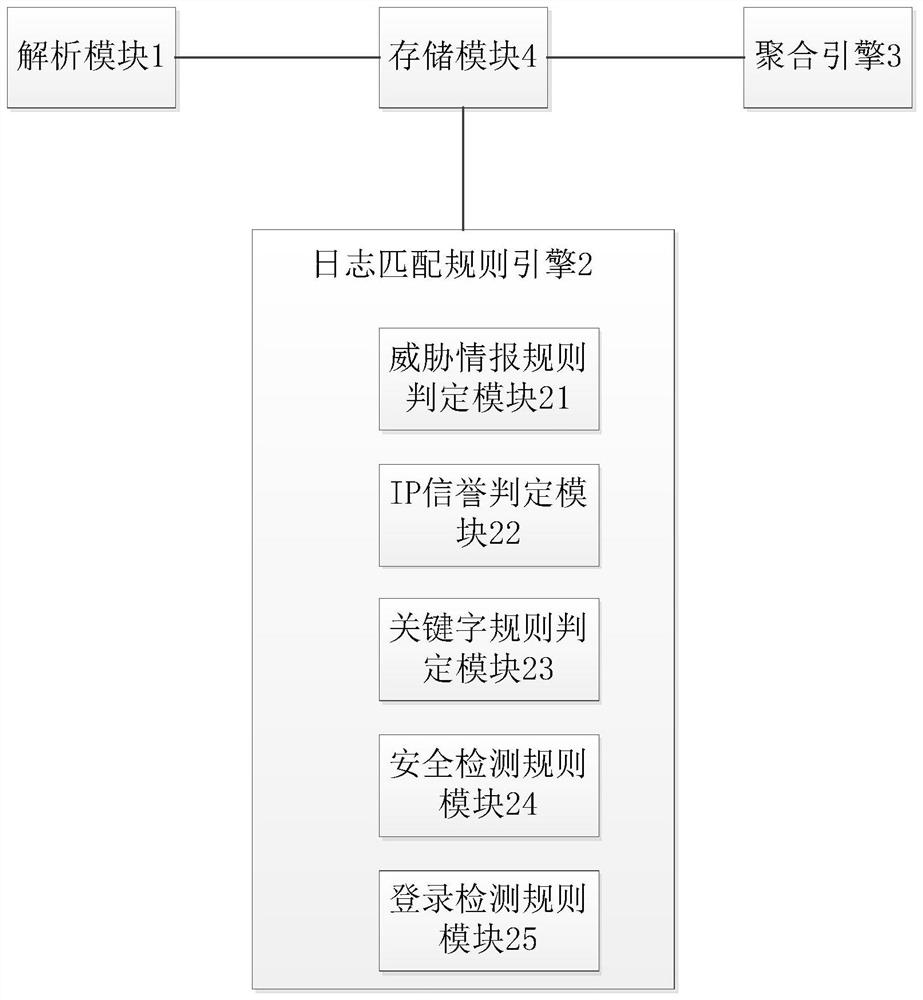
[0039] Such as figure 1 As shown, the web log-based intrusion research and judgment system provided by the present invention includes an analysis module 1 , a rule matching engine 2 , an aggregation engine 3 and a storage module 4 . The parsing module 13 is used to cut the original log into fields according to the default delimiter and default quoting character, and automatically identify the format of the field, quickly match the format of the field, analyze and process it into the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com