Container real-time migration method based on trusted computing
A technology of real-time migration and trusted computing, applied in the field of virtualization security, can solve problems such as short downtime, and achieve the effect of improving security, integrity and confidentiality assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
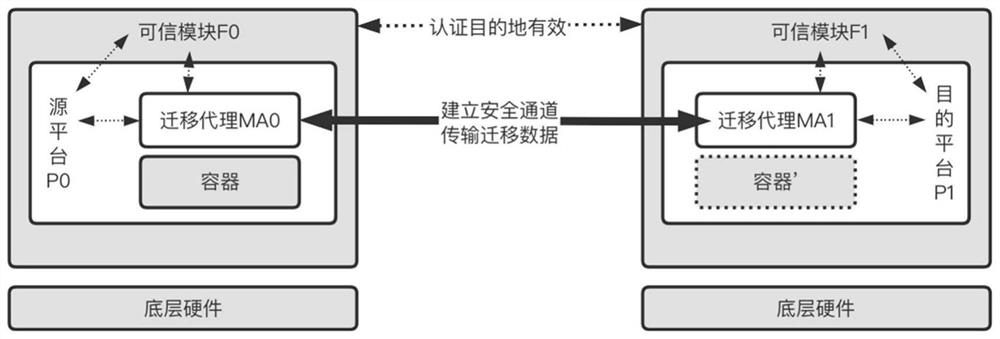
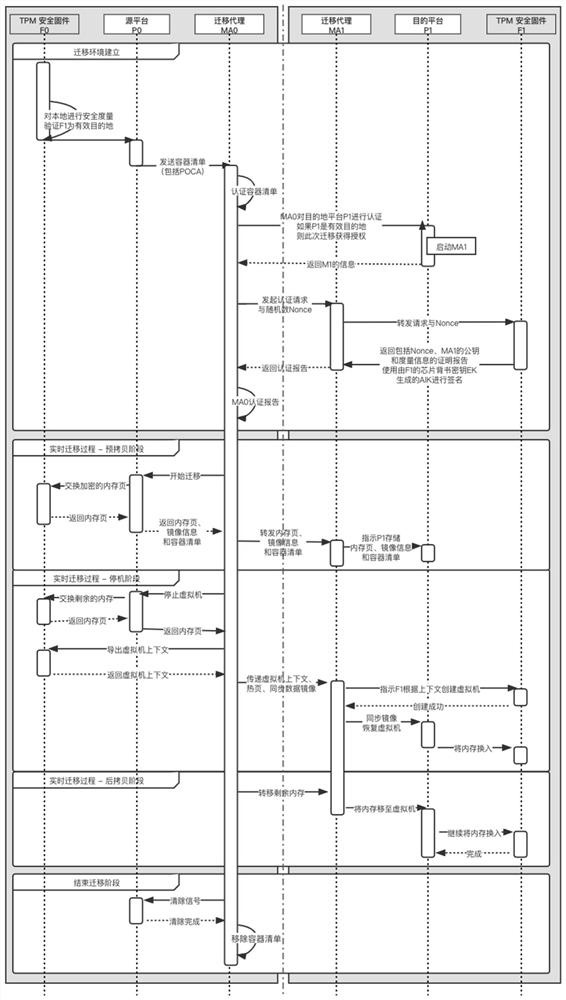
[0050] The purpose of the invention is to propose a method for real-time migration of containers based on trusted computing. The solution includes the following three stages: establishment of a migration environment, a stage of real-time migration, and a stage of end migration.
[0051] 1. Migration environment establishment
[0052] This step includes the stage of platform certification and resource preparation for both sides of the migration. The implementation steps are as follows:
[0053] Step 1: After the trusted chip F0 of the source platform P0 has passed the security measurement of the local environment, use the endorsement key to generate the corresponding identity authentication key AIK as the platform authentication key, record it as the hardware platform authentication key, and pass the hardware platform authentication key. A certification CA signs a certificate attesting to its authenticity. For each platform, a certificate is signed by the platform owner's cer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com