Access control vulnerability detection method and system based on state deviation analysis
A technology for access control and vulnerability detection, applied in the field of network security, can solve the problems of incapable of modeling and reducing complex data relationships, and achieve the effects of improving detection efficiency, improving detection efficiency, and reducing dependence.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further explained below in conjunction with accompanying drawing and specific embodiment:
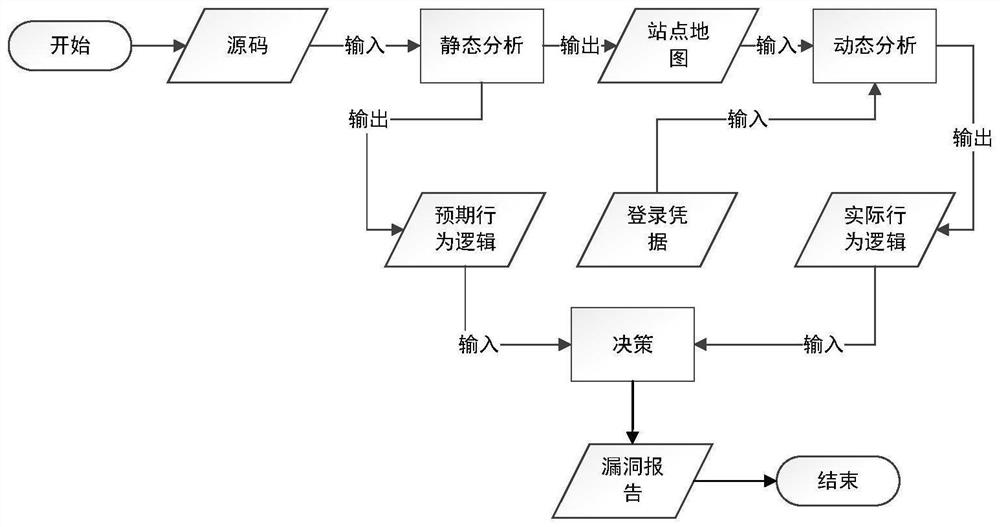
[0049] Such as figure 1 As shown, an access control vulnerability detection method based on state deviation analysis, including:
[0050] Taking the source code of the web application as input, the site map and the expected behavior logic contained in the code are extracted through static analysis, and then the generated site map is used as a guide for dynamic analysis, and the login credentials of multi-role and multi-user are input for Obtain HTTP requests and HTTP responses under different login states;
[0051] Use the finite state machine (FSM) to model the web application, formalize the discovery of access control vulnerabilities into the difference comparison between the expected FSM behavior model and the actual FSM behavior model, identify access control vulnerabilities and generate vulnerability reports; including : Static analysis is use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com