User data encryption and decryption method and device and electronic equipment
A technology for user data and encryption methods, applied in electrical components, digital video signal modification, image communication, etc., can solve the problems of reduced compression efficiency, reduced security, and high encryption complexity, to ensure security, avoid decryption resources, Avoid the effect of transmission insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
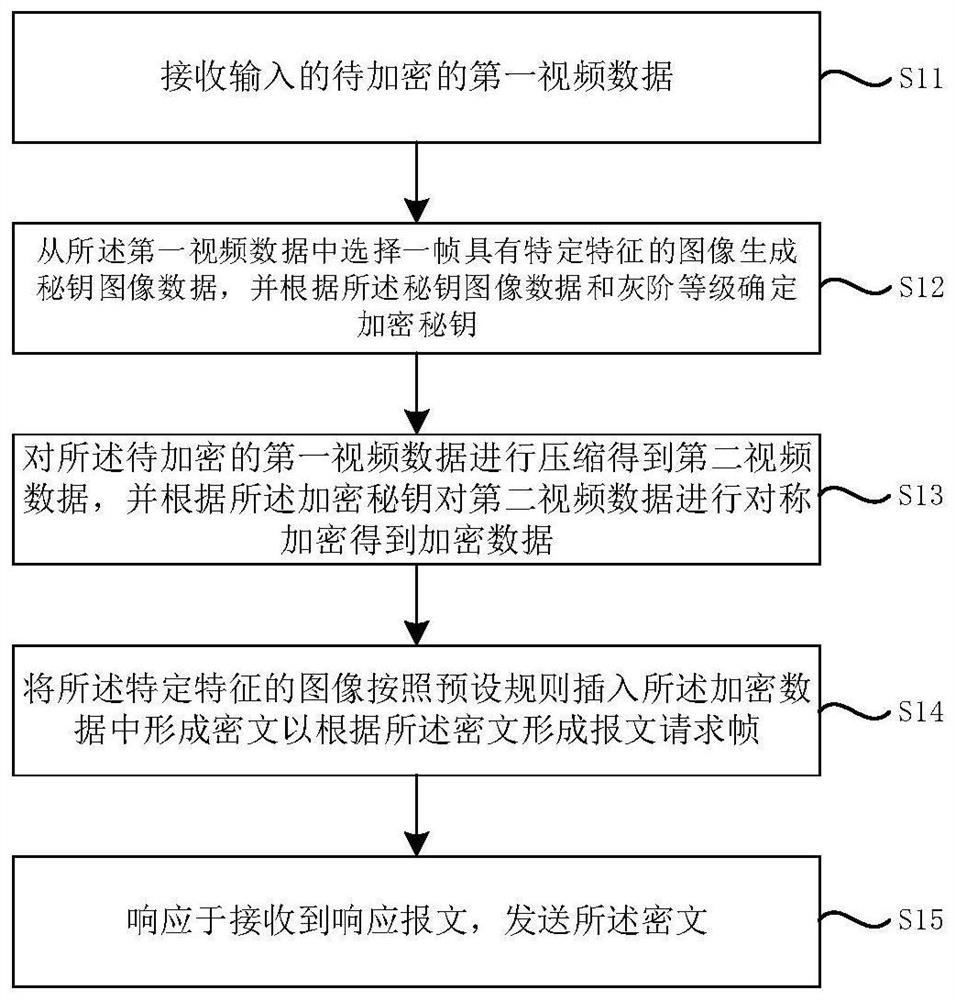
[0068] See figure 1 , figure 1 It is a schematic flowchart of a user data encryption method provided by an embodiment of the present invention, including:
[0069] S11. Receive the input first video data to be encrypted, wherein the first video data is uncompressed data; in this embodiment, the input first video data to be encrypted is the video used for face recognition For example, the user records video data in real time on a dedicated device as the first video data.
[0070] S12. Select an image with specific characteristics from the first video data to generate key image data, and determine the encryption key according to the key image data and gray scale; since the video is used for face recognition Therefore, an image with specific features is an image with a human face, and one frame is randomly selected from multiple frames of the video and human face images as the image for generating the key image data.
[0071] The encryption key of the user data encryption meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com