Encrypted malicious traffic detection method
A detection method and technology for malicious traffic, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problem of high false positive rate, machine learning model is not suitable for processing multiple heterogeneity, TLS encrypted malicious traffic detection recall rate is low, etc. problem, to achieve the effect of low false alarm rate, reduce overall complexity, and prevent training overfitting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039]The technical solutions in the examples of the present invention will be analyzed and expressed in a more comprehensive and complete manner below in conjunction with the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only part of the embodiments of the present invention. In order to further improve the present invention Explanations are provided to enable those skilled in the art to clearly and thoroughly understand the present invention, and are not intended to limit the present invention.
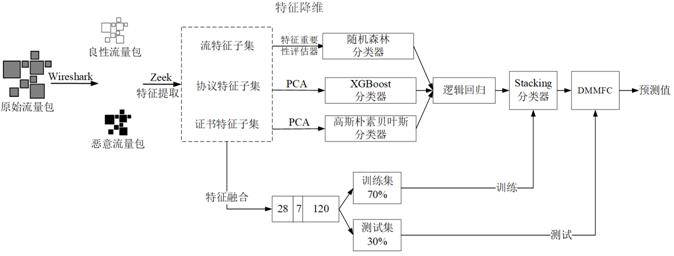
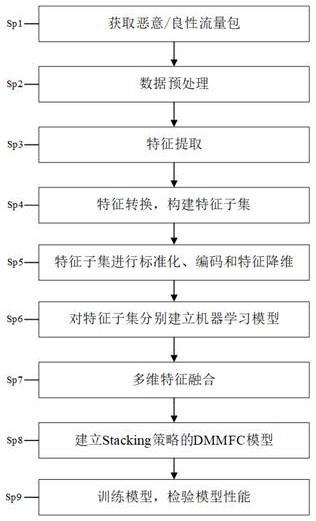
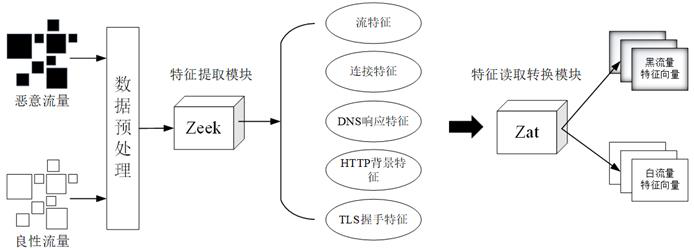
[0040] like Figure 1-4 As shown, the design process of an encrypted malicious traffic detection method provided by the embodiment of the present invention is as follows: divide the original traffic packets into benign traffic packets and malicious traffic packets, perform feature extraction, feature subset construction, feature encoding, and dimensionality reduction. Create a classifier model for each feature subset after...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com