Intranet security protection method and system based on behavior strategy, and medium
A security protection and behavior technology, applied in transmission systems, digital transmission systems, security communication devices, etc., can solve problems such as inability to guarantee security, and achieve the effect of avoiding transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
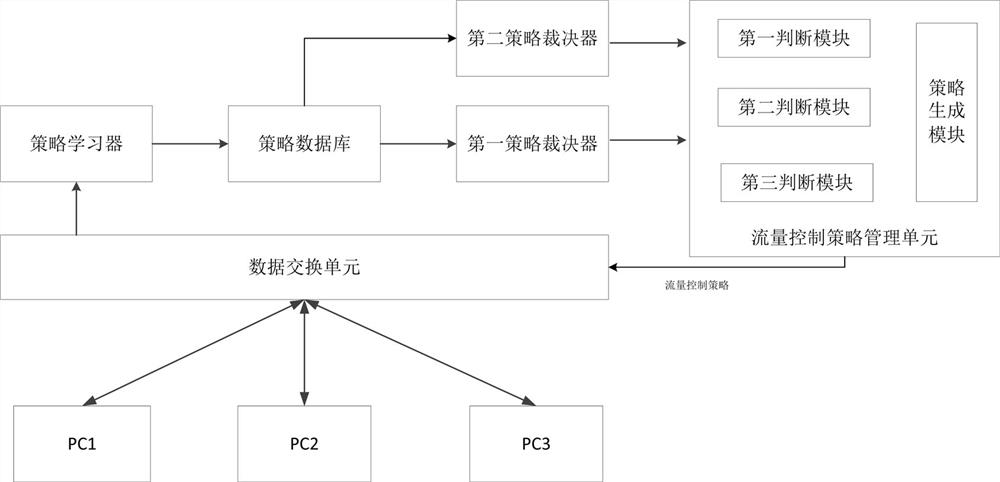
Image
Examples
Embodiment 1
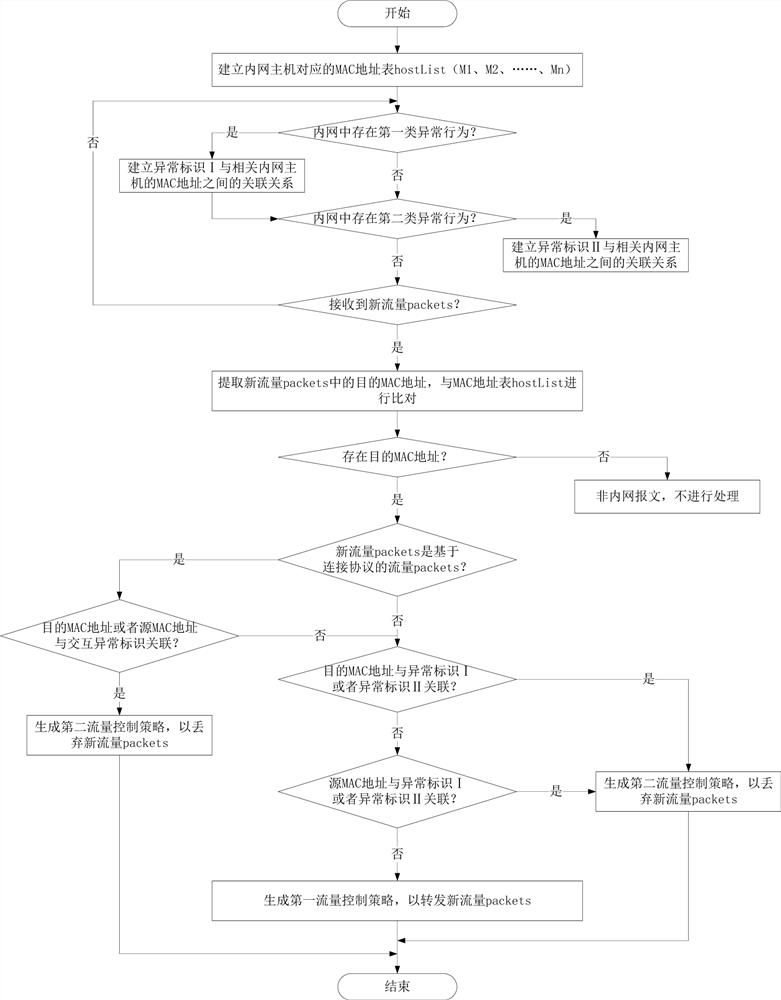
[0041] figure 2 A flow chart of an intranet security protection method based on a behavior policy is shown, and the behavior policy-based intranet security protection method includes the following steps:
[0042] Establish a MAC address table hostList (M1, M2, ..., Mn) corresponding to the intranet host, where M1 to Mn represent n MAC addresses corresponding to the intranet host;
[0043] Determine whether there is the first type of abnormal behavior in the intranet, and if there is the first type of abnormal behavior in the intranet, establish an association between the abnormality identifier I and the MAC address of the relevant intranet host;
[0044]Determine whether there is a second type of abnormal behavior in the intranet, and if there is a second type of abnormal behavior in the intranet, establish an association between the abnormality identifier II and the MAC address of the relevant intranet host;
[0045] Determine whether new traffic packets are received, and i...
Embodiment 2
[0065] It should be noted that SMAC, SIP, SPORT, DMAC, DIP, DPORT, FTYPE, and LENGTH abnormalities correspond to the first type of abnormal behavior and are marked by the abnormality identifier Ⅰ.
[0066] This embodiment provides a specific implementation method for identifying the first type of abnormal behavior, as shown in the attached Figure 4 As shown, when determining whether the first type of abnormal behavior exists in the intranet, execute:
[0067] Read each traffic packets transmitted by the data exchange unit, establish and update the data traffic record table hostData of each intranet host to learn the traffic behavior of each intranet host; the data traffic record table hostData_i of the i-th intranet host (SMAC, SIP, SPORT, DMAC, DIP, DPORT, FTYPE, LENGTH), SMAC means source MAC address, SIP means source IP address, SPORT means source port number, DMAC means destination MAC address, DIP means destination IP address, DPORT means Destination port number, FTYPE ...
Embodiment 3
[0077] It should be noted that abnormalities in Layer 2 communication protocols, Layer 3 communication protocols, application layer communication protocols, network traffic rates, or the total amount of network data correspond to the second type of abnormal behavior and are marked by the abnormality indicator II.
[0078] This embodiment provides a specific implementation method for identifying the second type of abnormal behavior, as shown in the attached Figure 5 As shown, when determining whether there is the second type of abnormal behavior in the intranet, execute:
[0079] According to the preset time interval and the corresponding data traffic record table hostData, create and update the behavior record table action (X 1 、X 2 ,...,X 6 ), where X 1 Indicates the Layer 2 communication protocol, X 2 Indicates the three-layer communication protocol, X 3 Indicates the application layer communication protocol, X 4 Indicates the network traffic rate, X 5 Indicates the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com