Key management method based on block chain
A key management and blockchain technology, applied in the field of blockchain-based key management, can solve the problems such as the sender and the receiver cannot receive information normally, unstable data reception, theft, etc., so as to reduce loss or theft. Possibility, security and more comprehensive access to records, the effect of transparency in key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
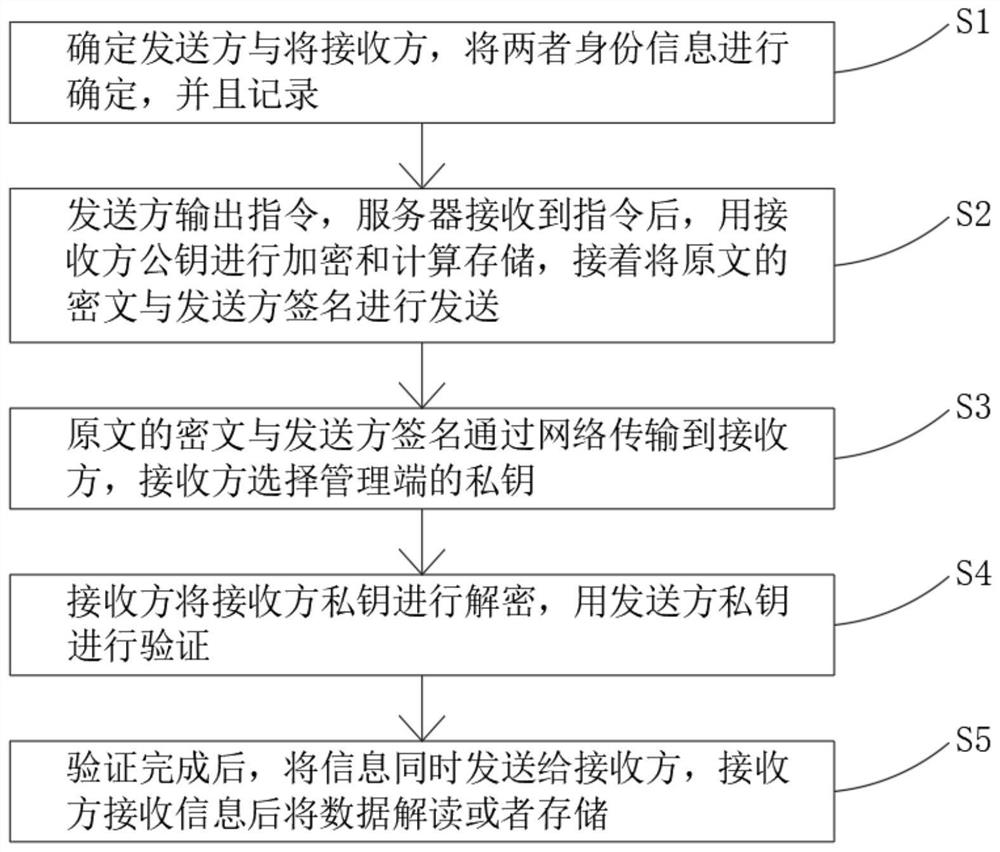
[0029] Such as figure 1 As shown, the present invention provides a technical solution, a method for key management based on blockchain, comprising the following steps:
[0030] S1. Determine the sender and the receiver, determine the identity information of the two, and record them;
[0031] S2. The sender outputs the command. After the server receives the command, it encrypts, calculates and stores it with the receiver's public key, and then sends the ciphertext of the original text and the sender's signature;
[0032] S3. The ciphertext of the original text and the signature of the sender are transmitted to the receiver through the network, and the receiver selects the private key of the management terminal;
[0033] S4. The receiver decrypts the receiver's private key and uses the sender's private key for verification;
[0034] S5. After the verification is completed, the information is sent to the receiver at the same time, and the receiver interprets or stores the data ...
Embodiment 2
[0049] Such as figure 1 As shown, the present invention provides a technical solution, a method for key management based on blockchain, comprising the following steps:
[0050] S1. Determine the sender and the receiver, determine the identity information of the two, and record them;
[0051] S2. The sender outputs the command. After the server receives the command, it encrypts, calculates and stores it with the receiver's public key, and then sends the ciphertext of the original text and the sender's signature;
[0052] S3. The ciphertext of the original text and the signature of the sender are transmitted to the receiver through the network, and the receiver selects the private key of the management terminal;
[0053] S4. The receiver decrypts the receiver's private key and uses the sender's private key for verification;
[0054]S5. After the verification is completed, the information is sent to the receiver at the same time, and the receiver interprets or stores the data a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com