Privacy protection k-means clustering method and device, medium and terminal
A clustering method and privacy protection technology, which is applied in the field of privacy protection, can solve problems such as high time cost, inaccurate clustering results, and insufficient security, and achieve low calculation cost and time cost, saving calculation time cost, and efficient privacy The effect of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
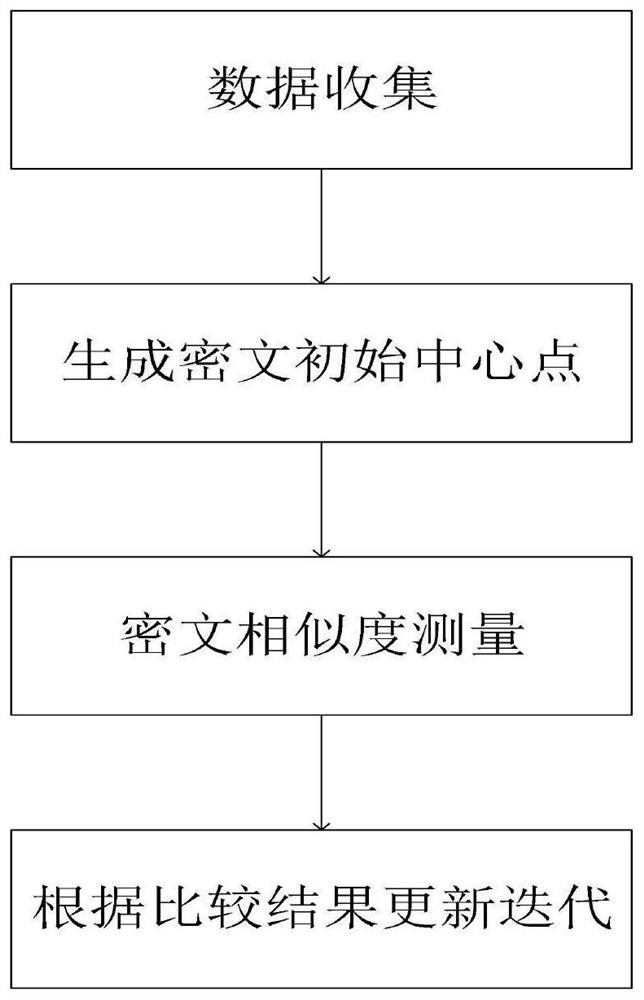
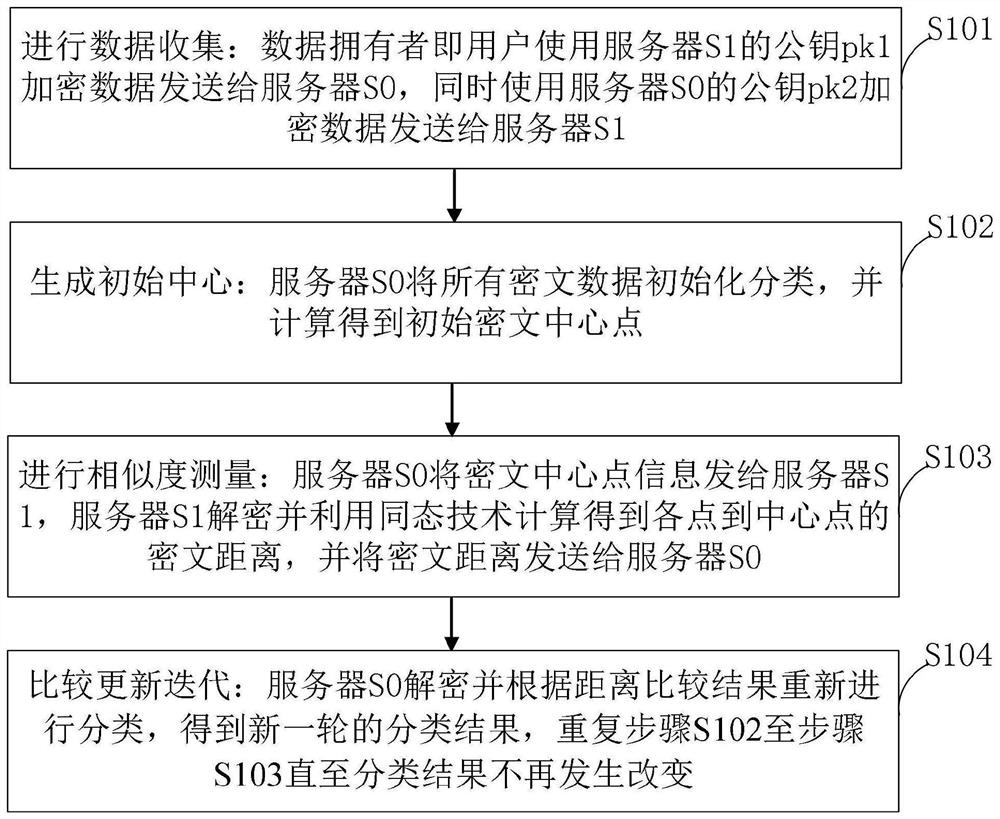
[0094] A kind of efficient privacy protection k-means clustering algorithm that the example of the present invention provides comprises the following steps:
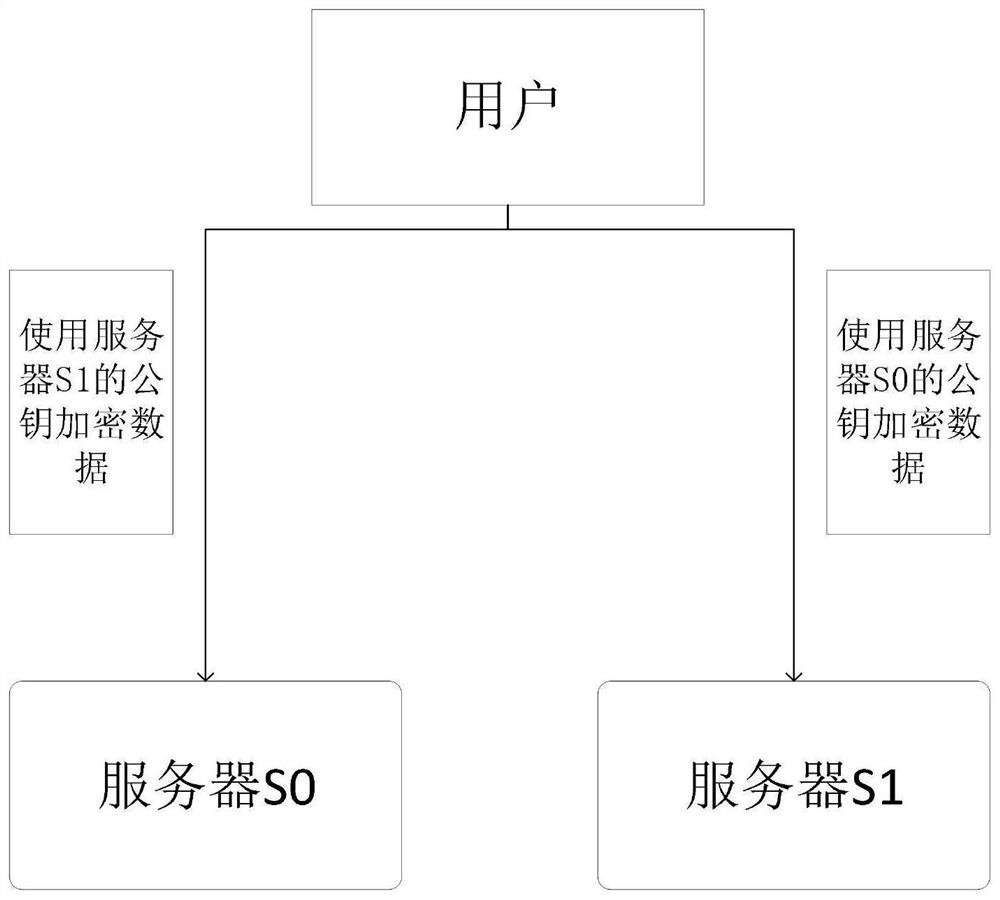
[0095] 1. Data collection: the data owner (user) uses the server S 1 public key pk 1 Encrypted data sent to server S 0 , and then use server S 0 public key pk 0 Encrypted data sent to server S 1 .
[0096] 2. Similarity measurement: server S 0 Send the ciphertext central point information to the server S 1 , server S 1 Decrypt and use homomorphic technology to calculate the ciphertext distance from each point to the center point, and send the ciphertext distance to the server S 0 .
[0097] 3. Compare update iteration: server S 0 Decrypt and reclassify according to the distance comparison results to get a new round of classification results, repeat the second and third steps until the classification results do not change.
[0098] 4. Compare update iteration: server S 0 Received from server S 1 Sent distance...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com