Vulnerability restoration method based on knowledge graph
A knowledge graph, vulnerability repair technology, applied in knowledge expression, special data processing applications, instruments, etc., can solve the problems of easy attack of hosts and systems, long repair time, etc., to reduce errors, improve security, improve efficiency and effect of speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the above objects, features and advantages of the present invention more comprehensible, specific implementations of the present invention will be described in detail below in conjunction with the accompanying drawings. In the following description, numerous specific details are set forth in order to provide a thorough understanding of the present invention. However, the present invention can be implemented in many other ways different from those described here, and those skilled in the art can make similar improvements without departing from the connotation of the present invention, so the present invention is not limited by the specific embodiments disclosed below.
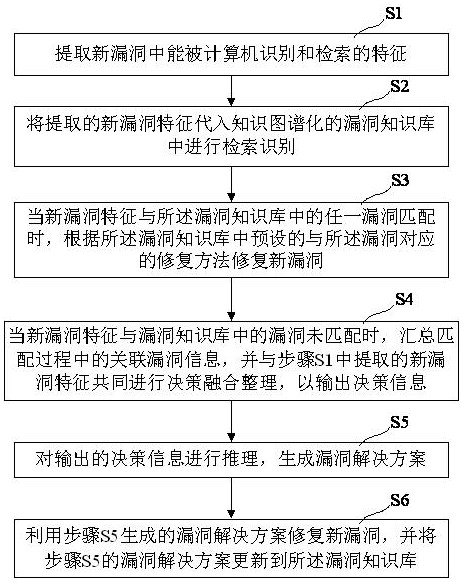
[0020] The present invention provides a vulnerability repair method based on a knowledge map. The vulnerability repair method first constructs a vulnerability knowledge base based on a knowledge map, which can also be understood as a knowledge map-based vulnerability knowledge base. Vulne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com