Multi-relational graph network-based vulnerability model construction method and detection method thereof
A construction method and relationship diagram technology, applied in biological neural network models, neural learning methods, neural architectures, etc., can solve the problem of low detection accuracy of vulnerability detection models, achieve poor detection results, improve accuracy, reduce The effect of false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
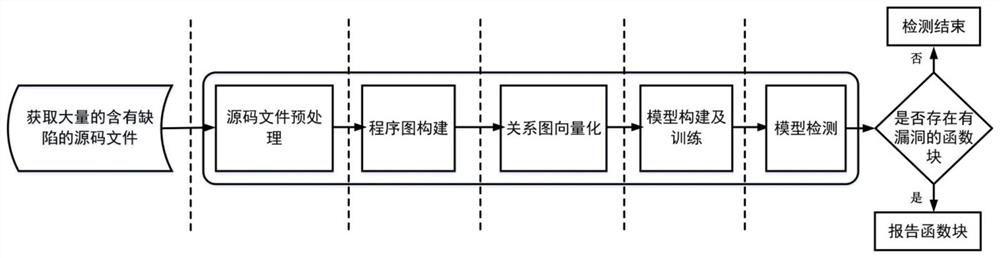
[0122] This embodiment provides a method for constructing a vulnerability model based on a multi-relational graph network. The method is performed according to the following steps:
[0123] Step 1. Collect the source code program files, and preprocess the source code program files to obtain function blocks. According to whether the function names corresponding to the function blocks contain good and bad, the corresponding labels are function blocks without loopholes and function blocks with loopholes;
[0124] In this embodiment, source code program files are collected from SARD.
[0125] Step 2, processing the function blocks without loopholes and the function blocks with loopholes to obtain their corresponding second abstract syntax trees; performing a first traversal on the second abstract syntax trees to obtain 7 kinds of edge relationships, and generating a relationship graph; At the same time, PCDG obtained by traversing the second abstract syntax tree; connecting the re...
Embodiment 2
[0178] This embodiment provides a detection method based on a multi-relational graph network vulnerability model, the method comprising the following steps:
[0179] Step 1: Collect new source code program files, and preprocess the source code program files to obtain function blocks. According to whether the function name corresponding to the function block contains good and bad, the corresponding labels are non-vulnerable function blocks and vulnerable function blocks ;
[0180] Step 2, performing the processing of step 2 to step 3 as claimed in claim 1 on the function block without loopholes obtained in step 1 and the function block with loopholes to obtain an adjacency matrix for detection;
[0181] Step 3, inputting the adjacency matrix obtained in step 2 for detection into the optimal GGNN vulnerability model obtained in step 4 of claim 1, if there is a function block containing double-free vulnerabilities in the test results, then report For this function block, if ther...
example 1
[0183] Following the above technical scheme, in the experiment of vulnerability detection, Figure 11 Shows the evaluation results of each type of vulnerability in the C language Top30 on the present invention, the results include accuracy, precision, recall and F1 score, where the detection accuracy of each type of vulnerability exceeds 80%, and some exceed 90% %, with an average of over 85%. Figure 12 Demonstrated the method of the present invention and VULDEEPECKER, μVULDEEPECKER, LIN et al., VUDDY, DEEPBUGS and DEVIGN to perform vulnerability detection on open source warehouses. The first three methods are based on BiLSTM, VUDDY uses hash functions to find vulnerable code clones, and DEEPBUGS uses Feed-forward neural network checks for defects, and DEVIGN uses standard GNN operations that do not distinguish between types of AST edges. All methods, except μVULDEEPECKER, use a binary decision to predict whether a code contains a vulnerability. Among them, the successfully i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com