A learned side-channel attack method and encryption device for automatically discovering leaked models
A side-channel attack and automatic discovery technology, applied in the field of side-channel attack methods and encryption equipment, can solve problems such as side-channel high-level attacks, improve reliability, avoid manual reasoning or guessing, and improve analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
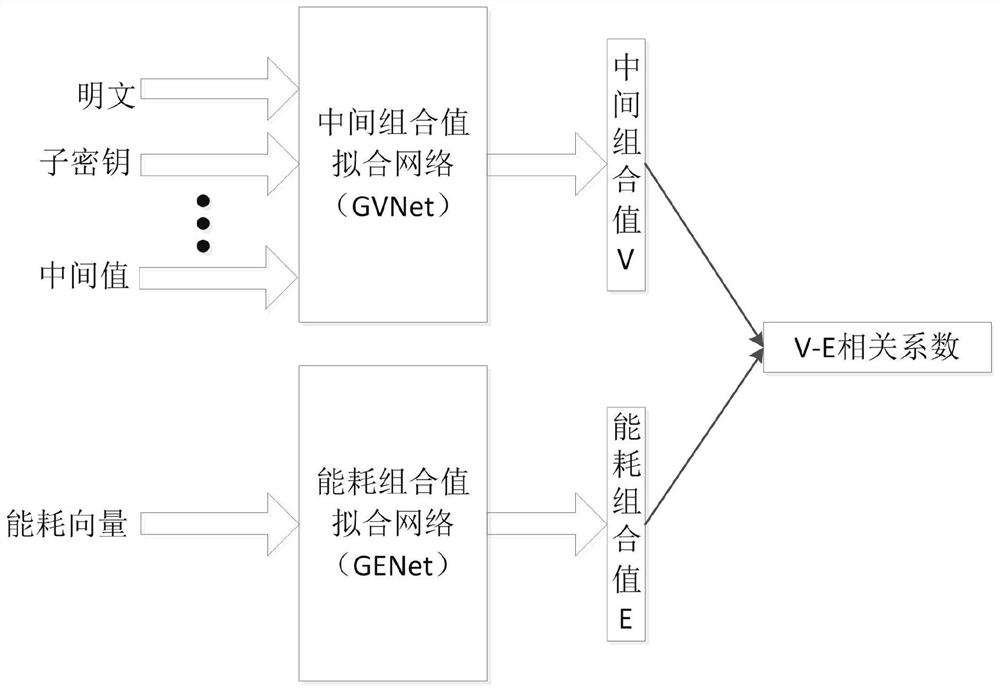
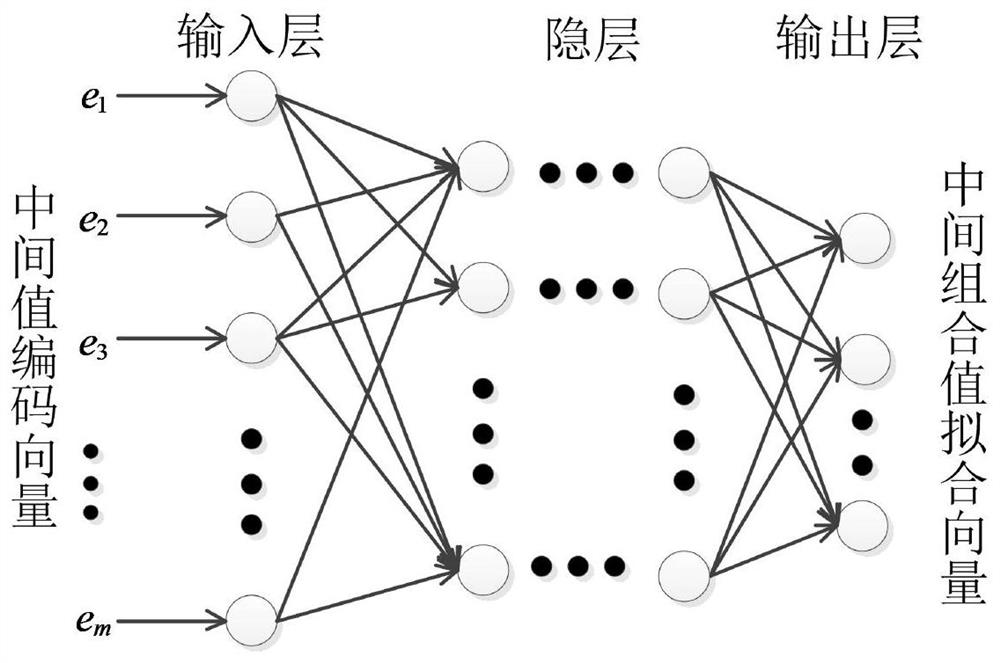
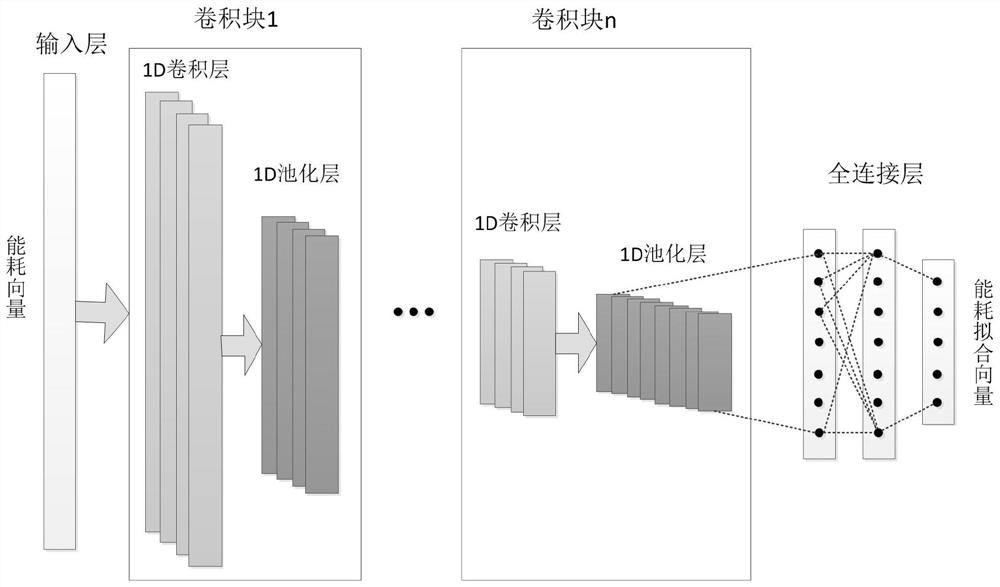
[0079] In a specific embodiment, the intermediate combination value fitting network GVNet of the attack model is defined as the input layer width of 48, which is used to input a plaintext byte of [-1,1] encoded 8-bit data, a subkey byte of [-1,1] Encoded 8-bit data, encrypted intermediate value ROUND-IN, ADD-KEY, SBOX-IN and SBOX-OUT with one byte of [-1,1] encoding a total of 32-bit data; The layer is 3 fully connected layers with a width of 128, and the neuron activation function is tanh; the output layer is a fully connected layer with a width of 8 neurons, and the neuron activation function is tanh. The energy consumption combination value fitting network GENet is a convolutional upgrading network. The input layer size is 10000, which is used to input all energy consumption samples generated by the SBOX0 encryption process; 5 convolution blocks are used, and each convolution block contains a 1D convolutional layer with stride 2 and a 1D stride 2 max pooling layers. The a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com