Text verification code recognition method and device based on cross-domain element learning and storage medium
A recognition method and meta-learning technology, applied in the fields of computer vision and image processing, can solve problems such as poor cross-domain effects of meta-learning algorithms and unbalanced data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
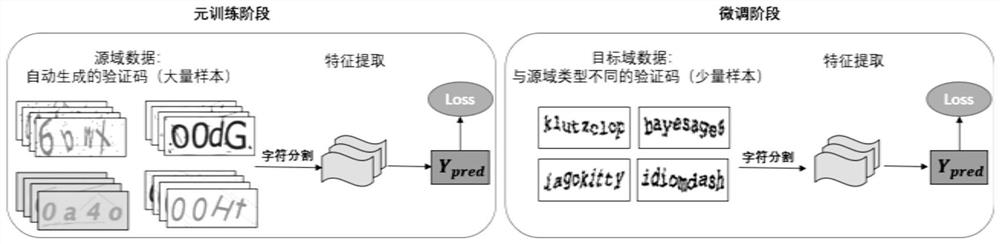
[0082] A text verification code recognition method based on meta-learning, such as figure 1 shown, including the following steps:
[0083] (1) Meta-training stage
[0084] First, generate a large number of verification code pictures with different security features as basic training data through the verification code generator;
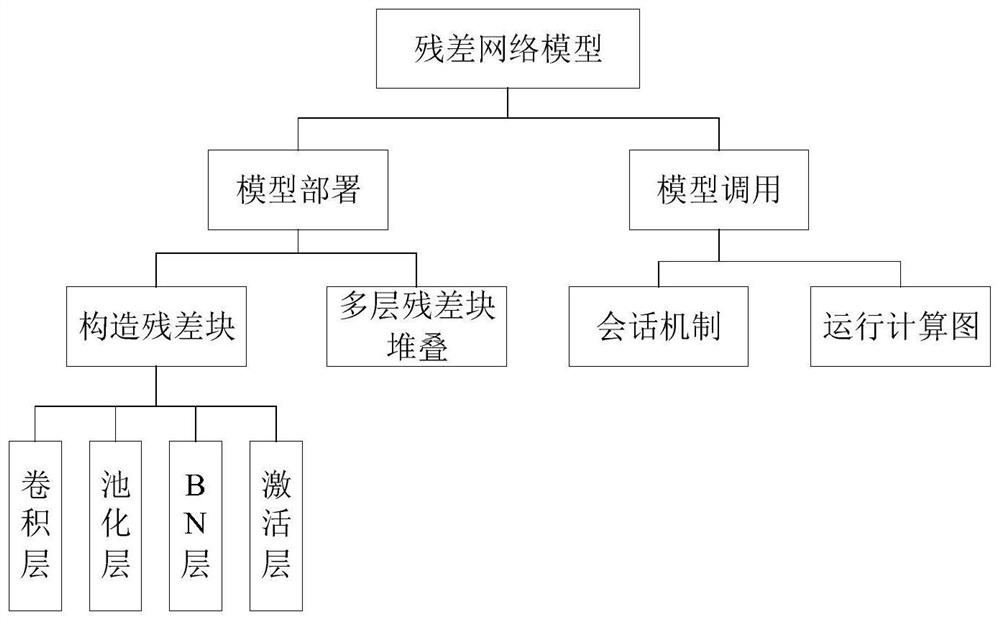
[0085] Then, use contour detection to segment the verification code pictures with different security features in the basic training data, and input the segmented characters into the ResNet neural network model for feature extraction;
[0086] Finally, the loss value of the estimated category is obtained;
[0087] (2) Fine-tuning stage
[0088] Label a small number of verification code pictures different from the basic training data in the meta-training stage, fine-tune the ResNet neural network model, and obtain the final recognition result.
Embodiment 2
[0090] According to the meta-learning-based text verification code recognition method described in Embodiment 1,
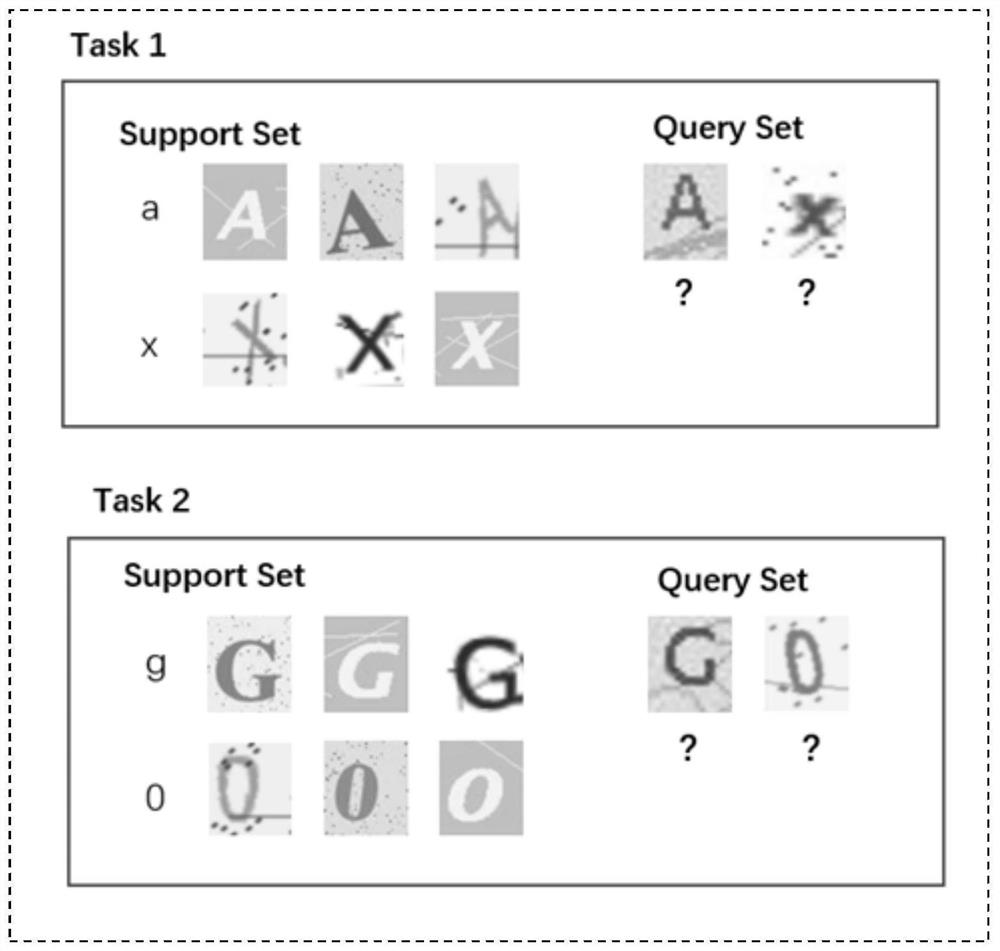
[0091] In the cross-domain meta-learning task, the source domain data, that is, the basic training data, is denoted as (x s ,y s ), where x s Indicates the source domain data sample, y s Indicates the label corresponding to the source domain data sample, and the target domain data is a small number of verification code pictures of different types from the basic training data, expressed as (x t ,y t ), where x t Indicates the target domain data sample, y t Indicates the label corresponding to the target domain data sample, and there is a difference between the source domain data and the target domain data in one or more items in the feature space, category space or marginal distribution. Such as figure 1 As shown, the verification code in the source domain data and the verification code in the target domain data contain different fonts, colors, background in...
Embodiment 3
[0136] A computer device includes a memory and a processor, the memory stores a computer program, and when the processor executes the computer program, the steps of the text verification code recognition method based on cross-domain meta-learning described in Embodiment 1 or 2 are realized.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com