Self-adaptive host intrusion detection sequence feature extraction method and system
A feature extraction and intrusion detection technology, applied in computer parts, computer security devices, instruments, etc., can solve problems such as overfitting of classification models, increase in the number of subsequences, and increase in computational cost of subsequences, and achieve good adaptability. , Characterize the comprehensive effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] An adaptive host intrusion detection sequence feature extraction method, comprising:
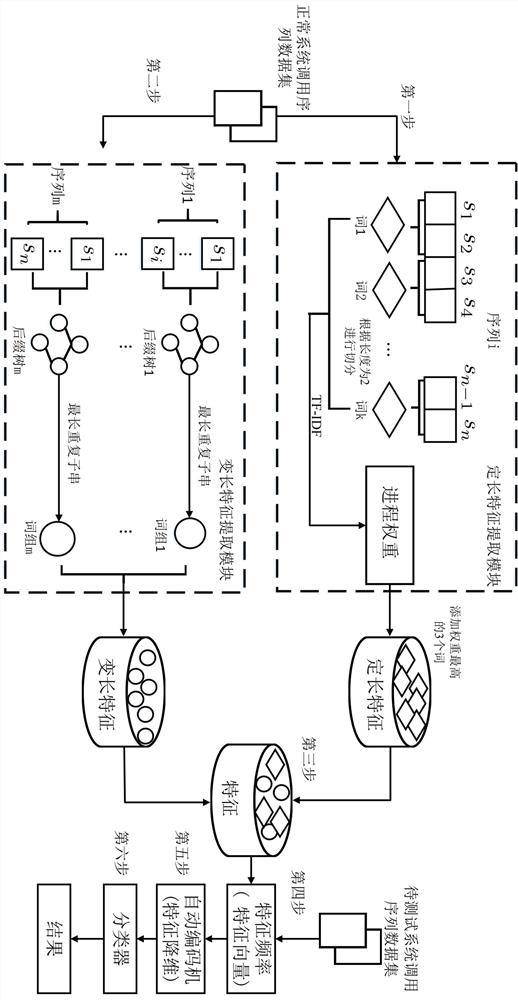
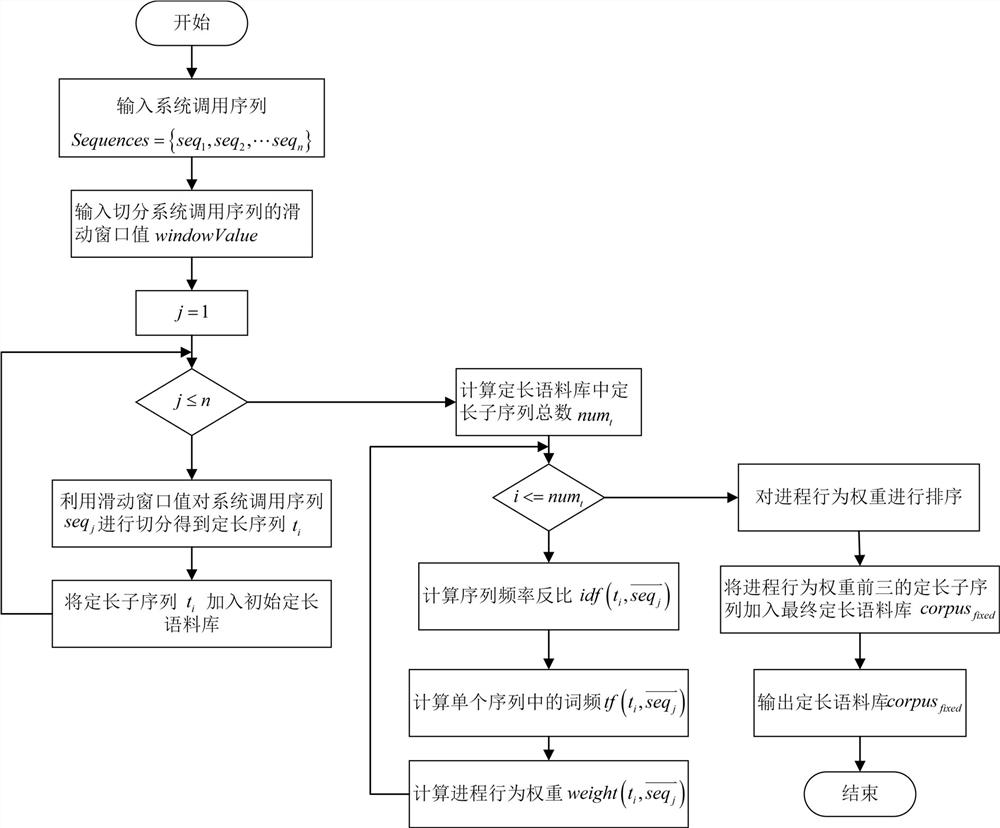
[0048] S1: Extract fixed-length features: call the system call sequence of the normal system call training data set (that is, the training data) Use the N-Gram (N-element model) sliding window value to divide each system call sequence into fixed-length subsequences, and use TF-IDF to weight each subsequence, and then filter the subsequences according to the size of the weight to obtain fixed-length subsequences , the fixed-length subsequence set is the fixed-length corpus, such as figure 2 shown.
[0049] The calculation method of using TF-IDF to weight each subsequence in the above step S1 is as follows:
[0050] : To calculate the inverse ratio of sequence frequency, first use N-Gram to divide the system call sequence into equal-length subsequences with a length of 2, that is, a subsequence with a length of 2 is a fixed-length subsequence. Then count each fixed-length subseque...
Embodiment 2
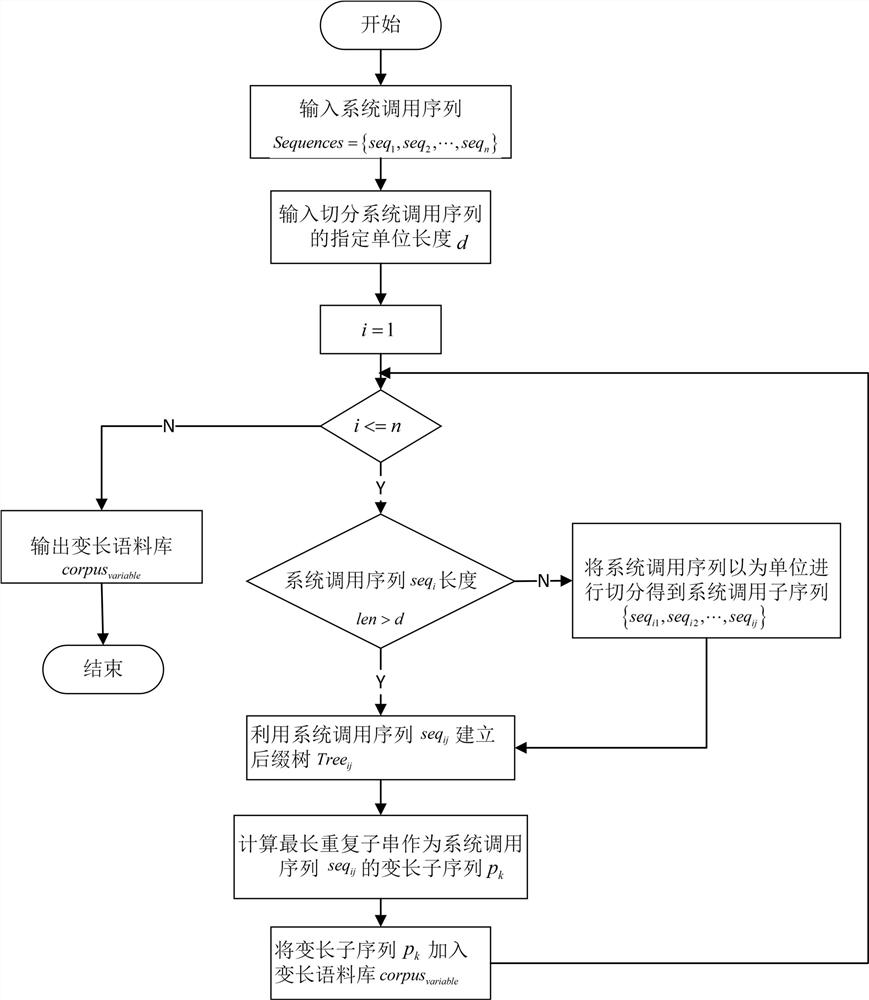
[0074] combined with figure 1 As shown, an adaptive host intrusion detection sequence feature extraction system includes a fixed-length feature extraction module, a variable-length feature extraction module, a feature fusion module, an automatic encoding machine module and a classifier module, wherein:
[0075] Fixed-length feature extraction module: use N-Gram technology to segment the input normal system call sequence with window value. Count each fixed-length subsequence Appears in different system call sequences frequency in . Then, the process behavior weight is calculated, and the process behavior weight can be obtained by the inverse ratio of the calculated frequency of a single fixed-length subsequence to the frequency of all sequences . Because process behavior weights represents the fixed-length subsequence t i , thus illustrating the taxonomic contribution of this fixed-length subsequence to anomaly detection. Finally, according to the size of the process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com