A blind signature generation method based on sm9 digital signature algorithm
A digital signature and blind signature technology, applied in the field of information security, can solve the problems that the signer does not know the specific content of the signed message and cannot sign the signature, and achieves the effect of strong security, guaranteeing correctness and guaranteeing privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
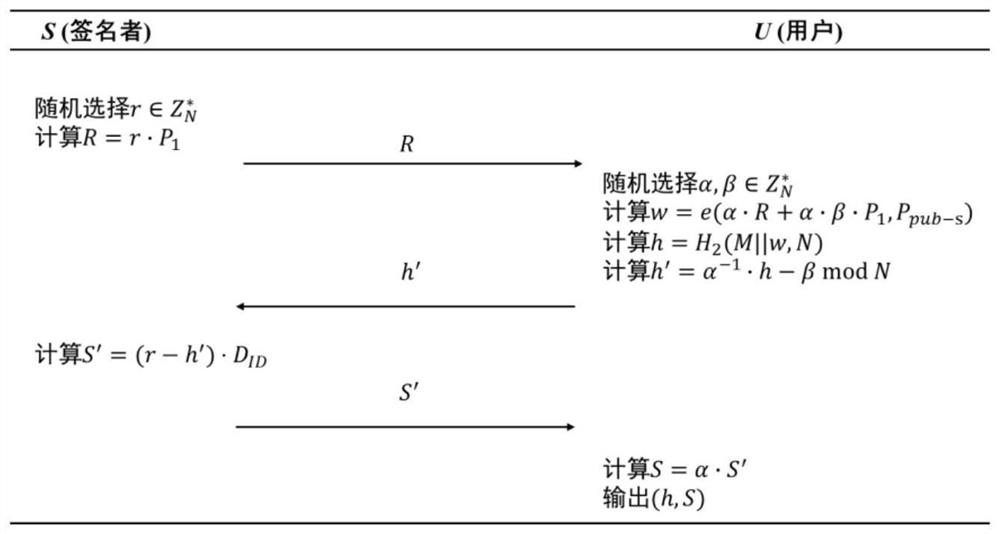
[0020] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
[0021] The meaning of the parameters in this example:
[0022] KGC: Key Generation Center
[0023] Signer, User: Both parties of the communication.
[0024] Additive cyclic group of order prime N.
[0025] A multiplicative cyclic group of order prime N.
[0026] e: from arrive bilinear pairing.
[0027] g u : Multiplicative group where g is raised to the power of u.
[0028] H 1 ( ), H 2 ( ): by {0, 1} * arrive cryptographic hash function.
[0029] ID U : The identity of the communicating party U, which can uniquely determine the public key of the communicating party U.
[0030] D ID : The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com