Implementation method of SM4-GCM network encryption transmission system based on FPGA
An encryption transmission and system implementation technology, applied in the field of FPGA-based SM4-GCM network encryption transmission system implementation, can solve problems such as slowing down encryption/decryption efficiency, system performance bottlenecks, and increasing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
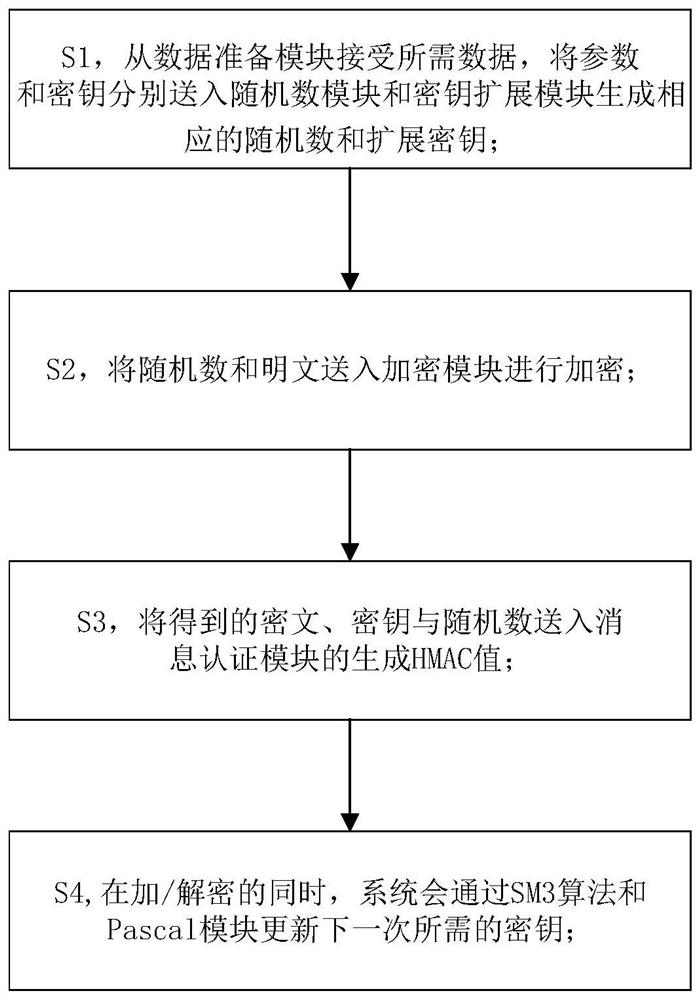
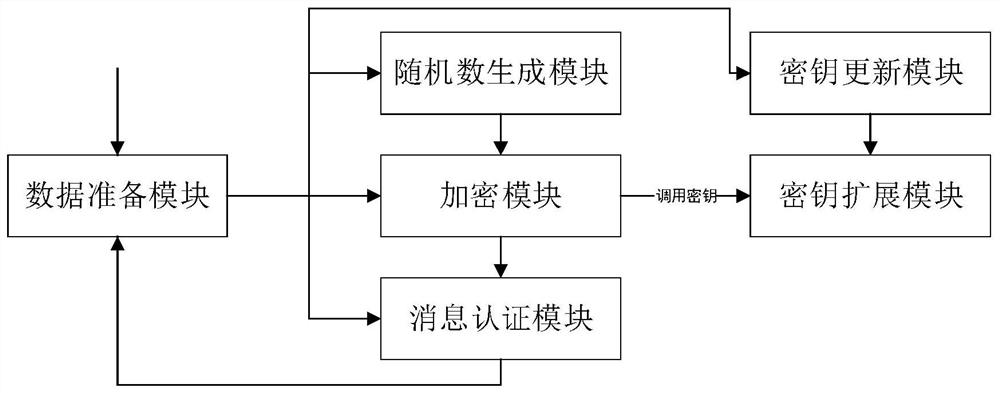
[0034] refer to figure 1 The FPGA-based SM4-GCM network encrypted transmission system implementation method step flowchart of the present embodiment; figure 2 A schematic diagram of the module relationship of the FPGA-based SM4-GCM network encrypted transmission system of an embodiment of the present invention; image 3 Be the top-level hardware structure of the SM4-GCM network encrypted transmission system based on FPGA of an embodiment of the present invention;
[0035] Specifically, an FPGA-based SM4-GCM network encrypted transmission system implementation method is characterized in that: comprising the following steps:
[0036] S1, receiving the required data from the data preparation module, sending the parameters and keys to the random number module and the key expansion module to generate corresponding random numbers and expansion keys;
[0037] S2, send the random number and plaintext to the encryption module for encryption;
[0038] S3, sending the obtained cipher...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com