Multi-center revocable key strategy attribute-based encryption method and device and storage medium
An attribute-based encryption and multi-center technology, applied in the field of data security, can solve problems such as fixed number of users, single point of failure, and lack of flexibility in key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
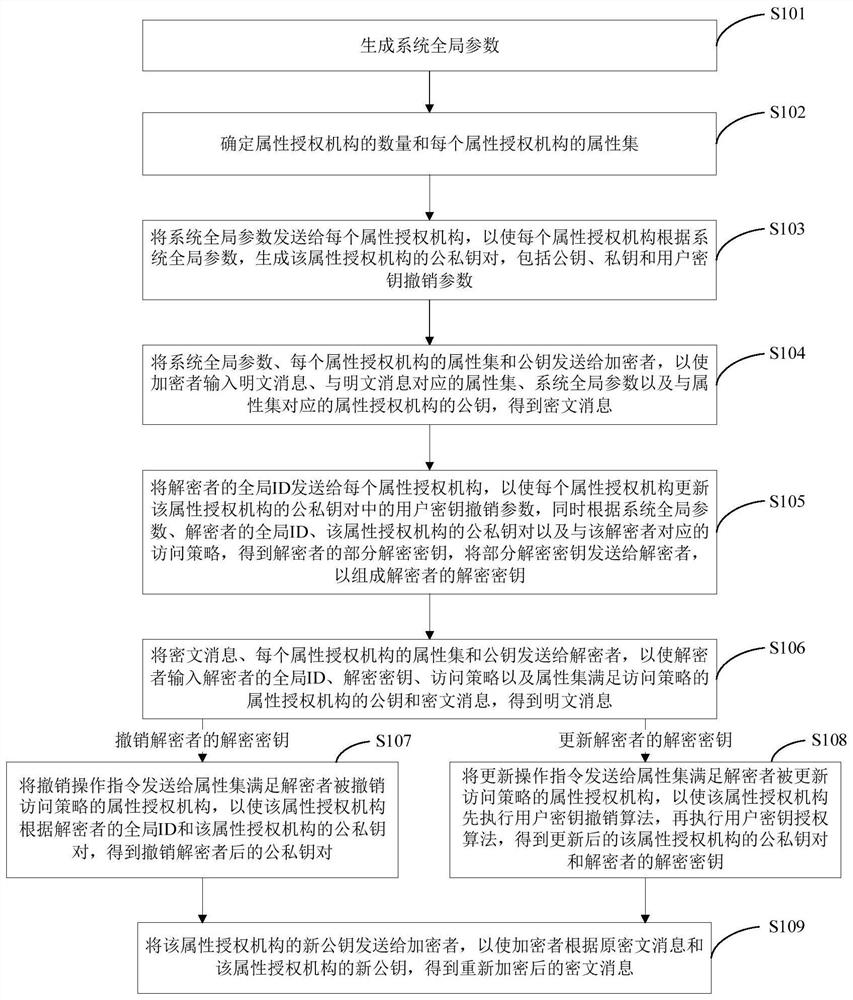
[0106] Such as figure 1 As shown, this embodiment provides a multi-center revocable key policy attribute-based encryption method, which includes the following steps:
[0107] S101. Generate system global parameters.
[0108] Specifically, let G and G T is a bilinear group with prime order p, and e is a bilinear map e: G×G→G T , g is the generator, after determining the security parameter δ, input the security parameter δ to generate the global parameters of the system: sp=(G, G T , e, g, p), complete the initialization of the system.
[0109] S102. Determine the number of attribute authorities and the attribute set of each attribute authority.
[0110]In this embodiment, the number of attribute authorization organizations is N. Under the premise of a given attribute space u, each attribute authorization organization manages mutually disjoint attribute sets. Generate any interaction to complete initialization of the property authority.
[0111] S103. Send the system globa...
Embodiment 2
[0172] Such as Figure 8 As shown, this embodiment provides a multi-center revocable key policy attribute-based encryption device, which includes a generation module 801, a determination module 802, a first sending module 803, a second sending module 804, and a third sending module 805 and the fourth sending module 806, the specific functions of each module are as follows:
[0173] The generating module 801 is configured to generate system global parameters.
[0174] A determining module 802, configured to determine the number of attribute authorities and the attribute set of each attribute authority.
[0175] The first sending module 803 is used to send the system global parameters to each attribute authority, so that each attribute authority generates the public-private key pair of the attribute authority according to the system global parameters, including public key, private key and user Key revocation parameters.
[0176] The second sending module 804 is used to send t...
Embodiment 3
[0186] This embodiment provides a computer device, which can be a computer, such as Figure 9 As shown, a processor 902, a memory, an input device 903, a display 904 and a network interface 905 are connected through a system bus 901, the processor is used to provide computing and control capabilities, and the memory includes a non-volatile storage medium 906 and an internal memory 907, the non-volatile storage medium 906 stores an operating system, a computer program, and a database, the internal memory 907 provides an environment for the operation of the operating system and the computer program in the non-volatile storage medium, and the processor 902 executes the During the computer program, realize the multi-center revocable key policy attribute-based encryption method of the above-mentioned embodiment 1, as follows:
[0187] Generate system global parameters;
[0188] Determine the number of attribute authorities and the set of attributes for each attribute authority;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com