Mobile phone battery protection board security authentication method and device based on encryption chip
A mobile phone battery and encryption chip technology, applied in the field of security authentication, can solve problems such as cracking the verification method of the mobile phone battery protection board, and achieve the effect of ensuring security and strengthening security verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
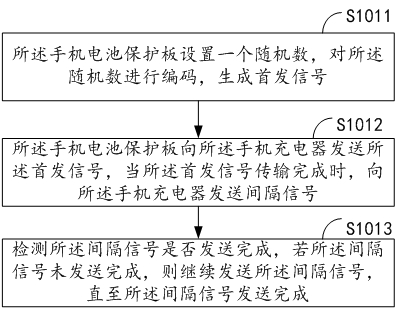
[0084] The mobile phone battery protection board sets a random number, encodes the random number, and generates a first signal;
[0085] Assuming that the width of the initial signal is 2M, the time slot signal a and the preset time slot threshold a s Compare;
[0086] If the time slot signal is less than the time slot threshold, the first signal is defined as A 1 , the empty transmission width of the first signal is defined as M / 2, the width of the high-level signal is 3M / 2, the interval between the first signal and the time slot signal is aM, and the first signal is transmitted to mobile phone charger;
[0087] When the transmission of the initial signal is completed, send an interval signal to the mobile phone charger to detect whether the interval signal has been sent, if the interval signal has not been sent, continue to send the interval signal until the interval signal send completed;
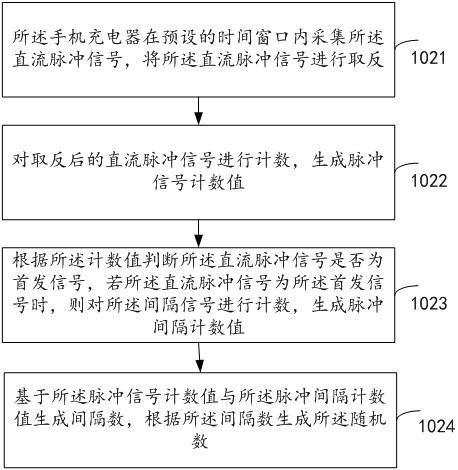
[0088] The mobile phone charger collects the DC pulse signal, and judges whether...
Embodiment 2
[0093] The mobile phone battery protection board sets a random number, encodes the random number, and generates a first signal;
[0094] Assuming that the width of the initial signal is 2M, the time slot signal a and the preset time slot threshold a s Compare;
[0095] If the time slot signal is greater than the time slot threshold, the first signal is defined as A 2 , the empty transmission width of the first signal is defined as 3M / 2, the width of the high-level signal is M / 2, and the interval between the first signal and the time slot signal is (a s -a), transmitting the first signal to the mobile phone charger;
[0096] When the transmission of the initial signal is completed, send an interval signal to the mobile phone charger to detect whether the interval signal has been sent, if the interval signal has not been sent, continue to send the interval signal until the interval signal send completed;
[0097] The mobile phone charger collects the DC pulse signal, judges ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com