Safety verification method and device based on 5G information, storage medium and equipment
A security verification and security certification technology, applied in security devices, wireless communications, electrical components, etc., can solve problems such as poor customer experience and loss of customer funds, and achieve the effect of improving security and customer experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
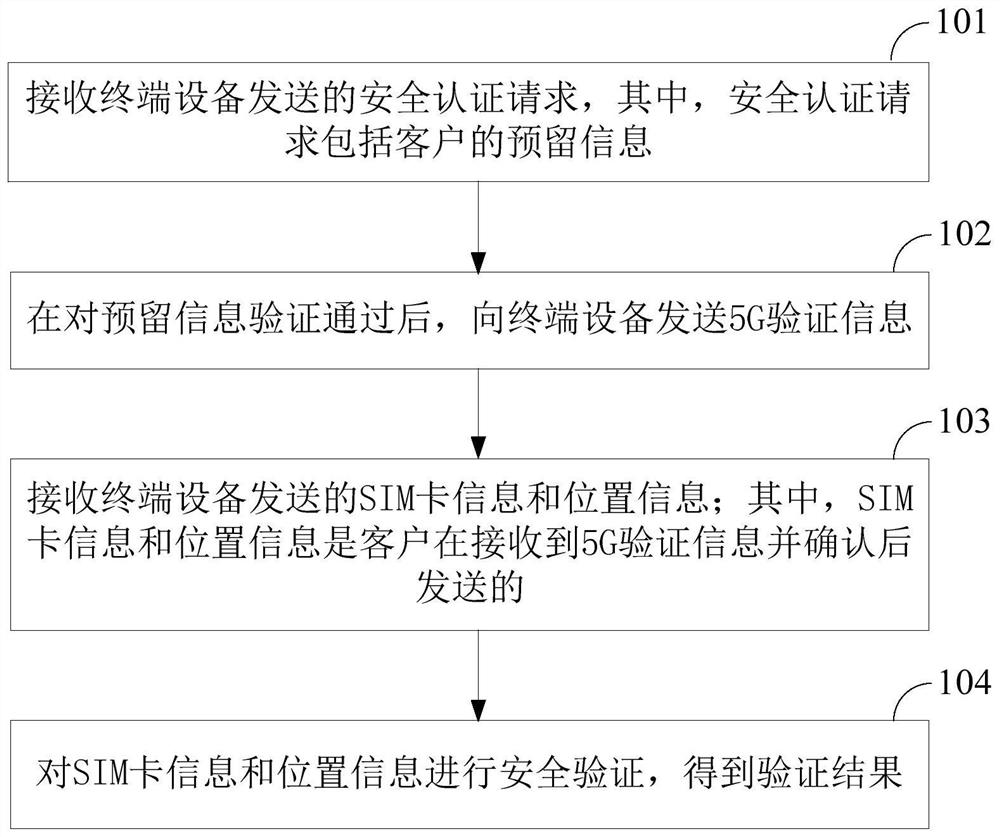
[0042] see figure 1 , which is a schematic flow diagram of a security verification method based on 5G information provided in this embodiment, the method includes the following steps:
[0043] S101: Receive a security authentication request sent by a terminal device, where the security authentication request includes customer reservation information.
[0044] It should be noted that with the gradual maturity of the fifth generation mobile communication technology (5th generation mobile networks or 5th generation wireless systems, 5th-Generation, 5G for short), the 5G messaging service is also coming, and industry users can use chatbots ( Chatbot) interacts with individual users through the carrier network. Among them, Chatbot refers to a service presented in the form of dialogue provided by industry customers to end users. The service is usually based on artificial intelligence software, which simulates human intelligent dialogue and provides users with specific service func...
no. 2 example
[0067] This embodiment will introduce a security verification device based on 5G information. For related content, please refer to the above method embodiment.
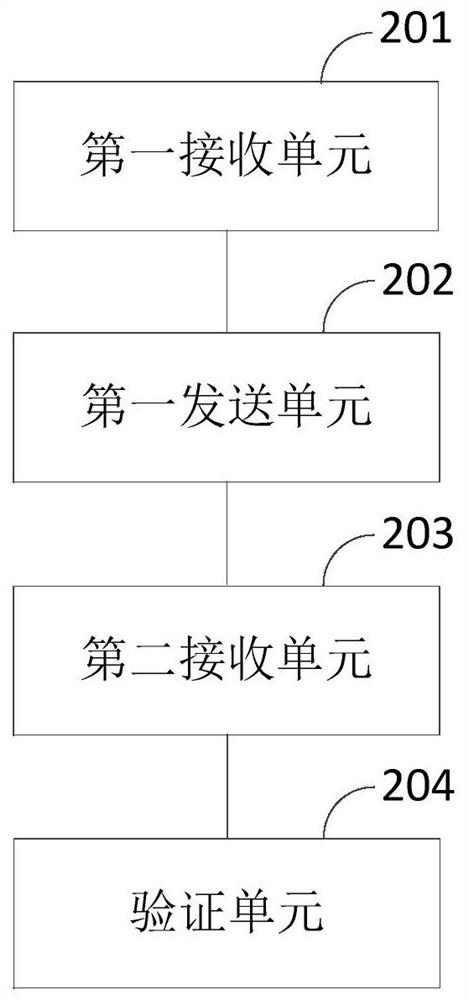
[0068] see figure 2 , which is a schematic diagram of the composition of a 5G information-based security verification device provided in this embodiment, the device includes:
[0069] The first receiving unit 201 is configured to receive a security authentication request sent by the terminal device, where the security authentication request includes the reserved information of the client;
[0070] The first sending unit 202 is configured to send 5G verification information to the terminal device after the verification of the reservation information is passed;
[0071] The second receiving unit 203 is configured to receive SIM card verification information and location information sent by the terminal device; the SIM card verification information and location information are sent by the customer after receiving and c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com