Hardware Trojan attack method for on-chip interconnection structure of reconfigurable accelerator
An interconnection structure, hardware Trojan technology, applied in the protection of instruments, digital computer parts, internal/peripheral computer components, etc., can solve problems such as Trojan horse attack accelerator, affect artificial intelligence processing system, etc., achieve good concealment, reduce network reasoning The effect of precision, low hardware resource overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
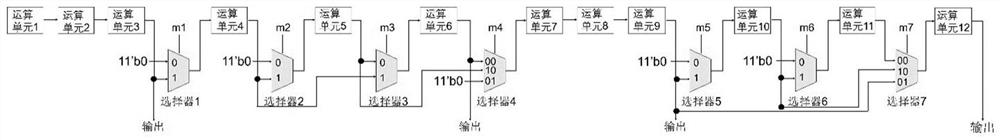
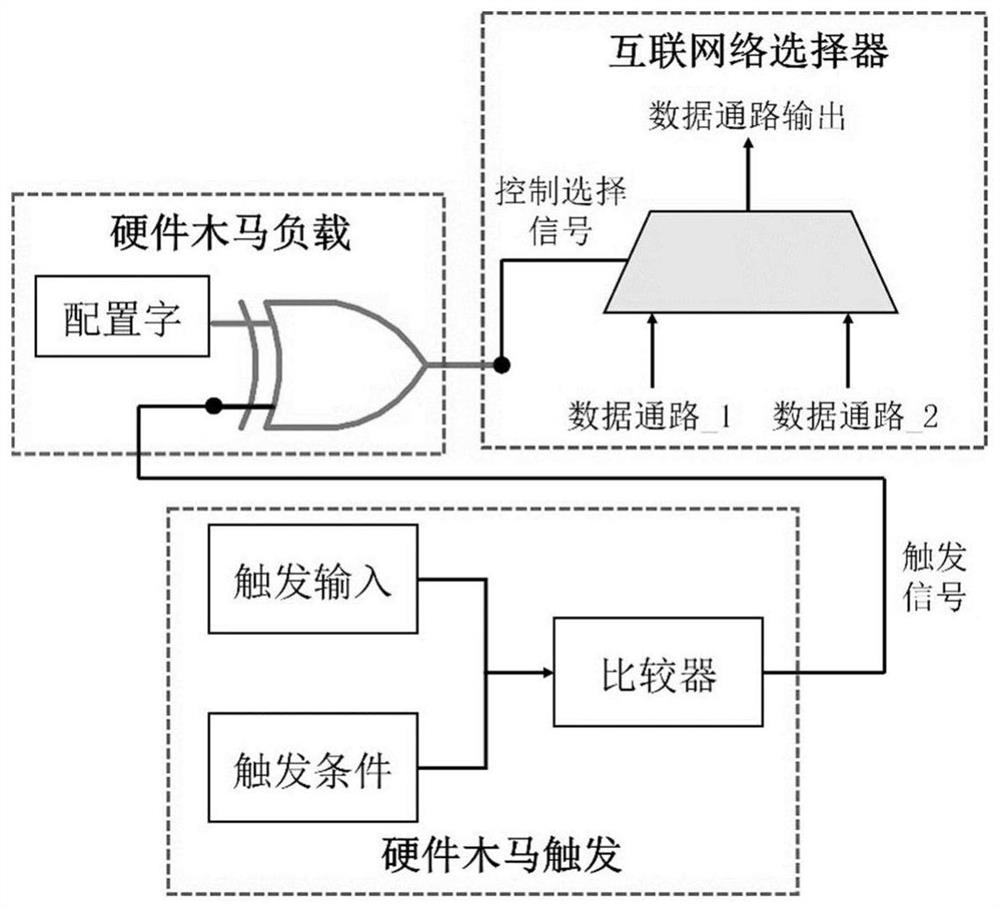
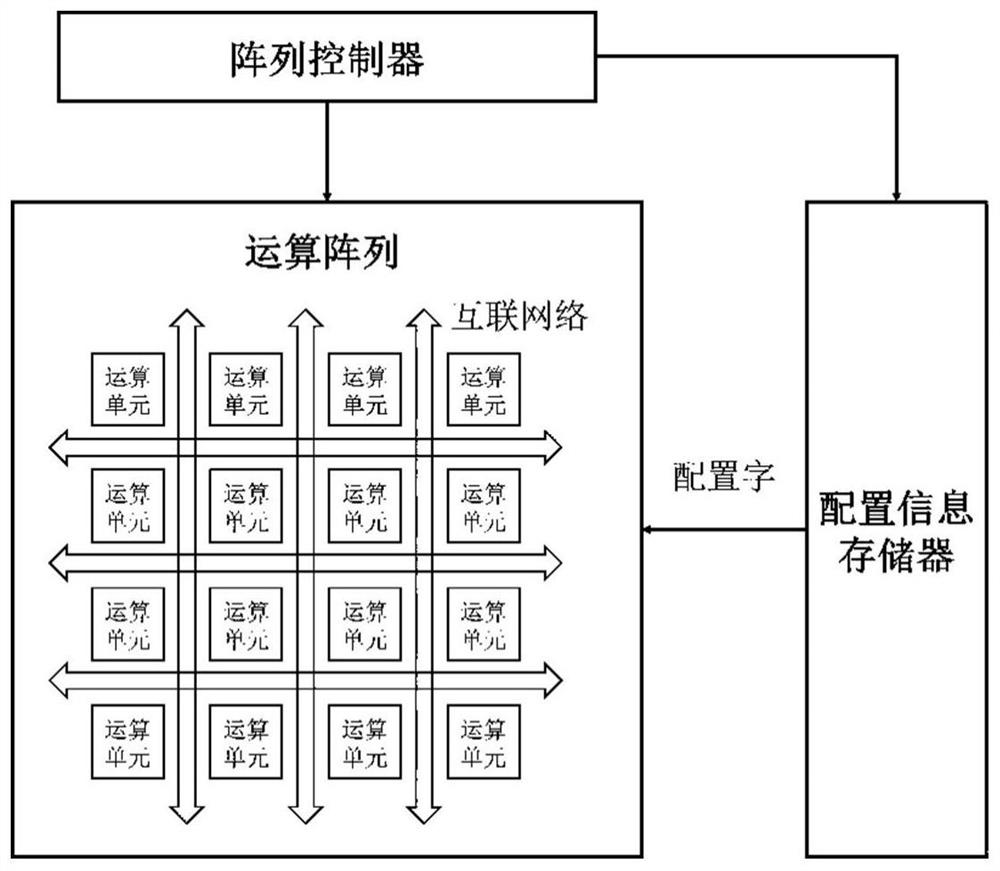
[0088] In the reconfigurable convolutional neural network accelerator that has been designed, its on-chip interconnect structure is as follows: figure 1 As shown, the convolution operation of three convolution kernel sizes of 3×3, 5×5, and 11×11 can be realized by configuring the word organization operation array in Table 1. By modifying the RTL-level Verilog code, a hardware Trojan horse is implanted in the on-chip interconnection structure, and then two trigger conditions are preset respectively, and two kinds of trigger input hardware Trojan horse attacks are implemented.
[0089] Take the operation array to perform the 3×3 convolution kernel size operation and select the operation array and some structures of the Internet as an example, such as Figure 8 As shown in , it illustrates the hardware Trojan horse attack situation of image data triggering input. Figure 8 It is shown that the hardware trojan in the reconfigurable interconnection network modifies the control sel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com