Secret key generation method and device, storage medium and electronic equipment
A technology of key generation and key generation center, which is applied in the blockchain field and can solve problems such as leakage and theft of user keys and reduction of user key security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
application example 1
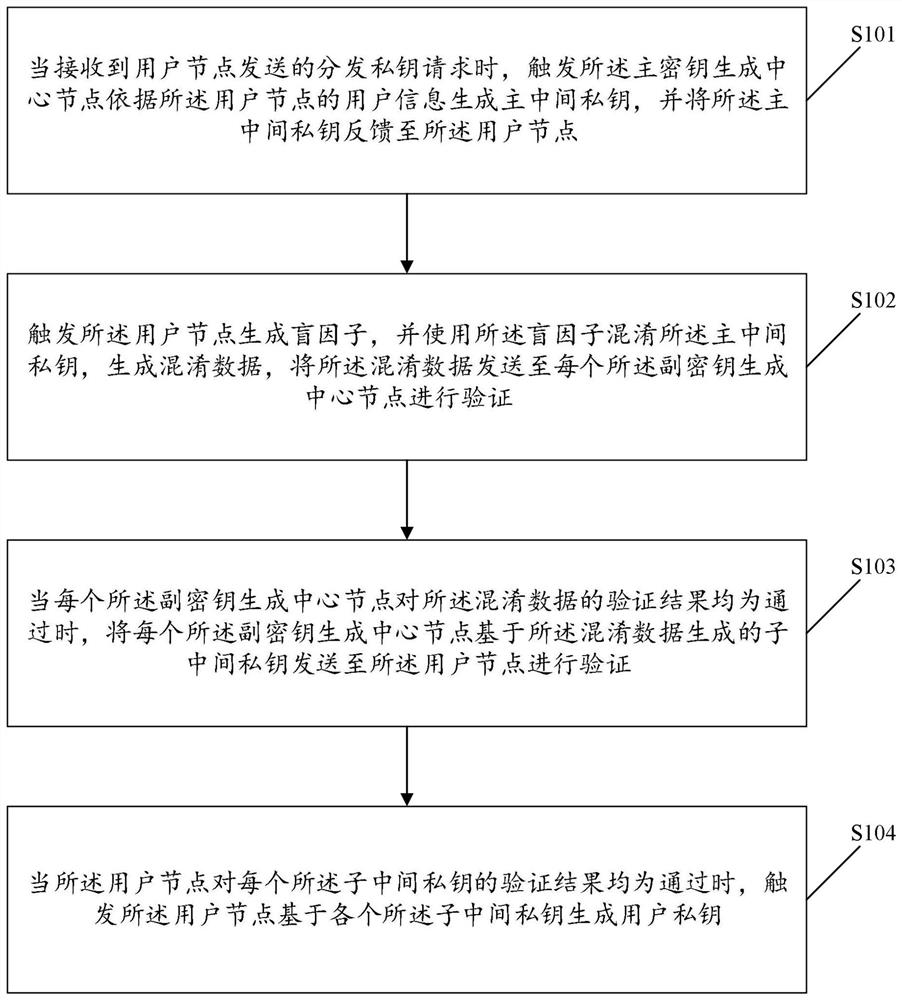
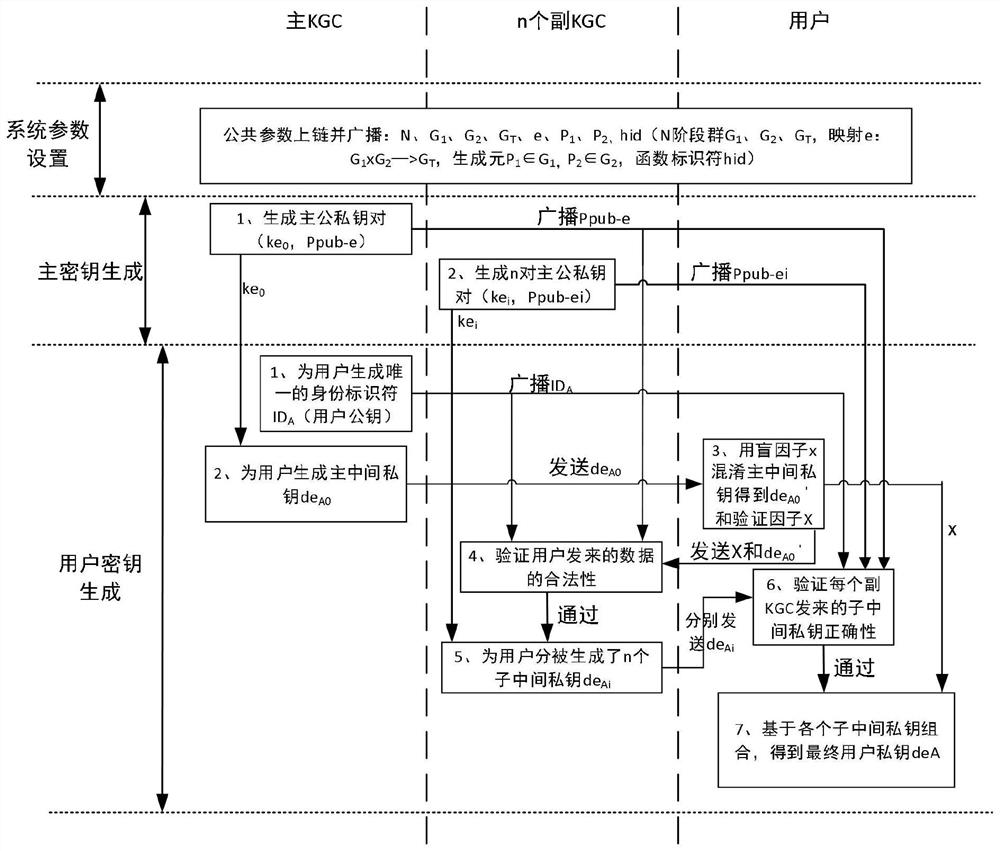
[0143] When the user requests to generate an encryption key, for the encryption and decryption process, the main KGC and the secondary KGC respectively generate their own encryption master key pair, and generate an intermediate key for the user to encrypt, and finally the user assembles the user's encrypted private key. key. Subsequent user U A ID A and the master public key P of the master KGC pub-e , the primary public key P of each secondary KGC pub-ei Encrypted, using the identity identifier ID A and user private key de A Decryption; wherein, the user is the user node in the above example; the main KGC is the main KGC node in the above example; the secondary KGC is the secondary KGC node in the above example.
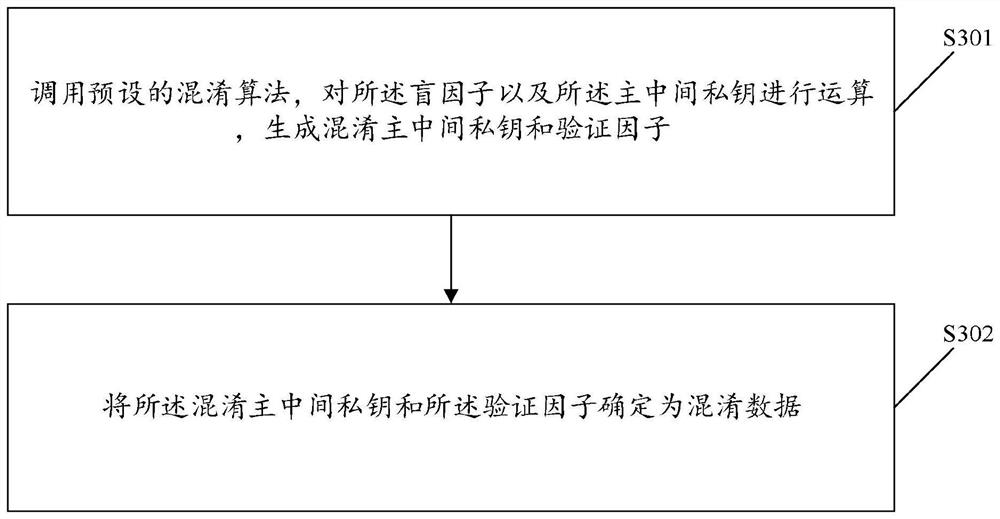
[0144] When receiving the private key distribution request sent by the user, the private key distribution request is specifically a request to distribute an encryption key, and the master KGC invokes the Create KGC-key service to generate a master-public-privat...
application example 2
[0177] It should be noted that some descriptions in the application example 2 may refer to the content in the application example 1, and details will not be repeated in the application example 2.
[0178] When the user requests to generate a signature key, for the signature verification process, the main KGC and the secondary KGC respectively generate their own signature master key pair, and generate an intermediate key for the user to sign, and finally the user assembles the user signature private key. Subsequent user U A ID A and user private key ds A To sign, use the identity identifier ID A and the master public key P of the master KGC pub-s , each vice P pub-si Check the signature.
[0179] When receiving the private key distribution request sent by the user, the private key distribution request is specifically a request to distribute the signature key, and the master KGC invokes the Create KGC-key service to generate the master-public-private key pair (ks 0 ,P pu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com