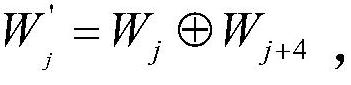SM3 cryptographic hash algorithm message extension serial optimization system and method
A hash algorithm and optimization method technology, applied in the field of information security, can solve the problems of large intermediate storage value, low operation efficiency, low utilization rate of registers or storage units, etc., to achieve less registers, reduce the number of operation rounds, and shorten operation time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
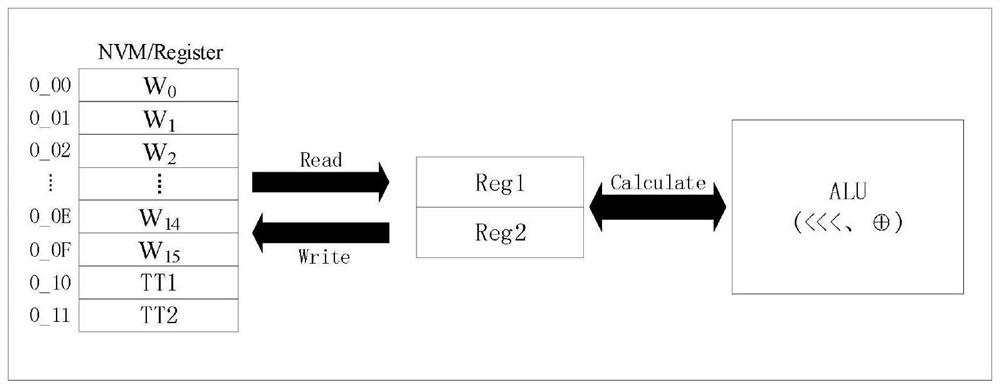
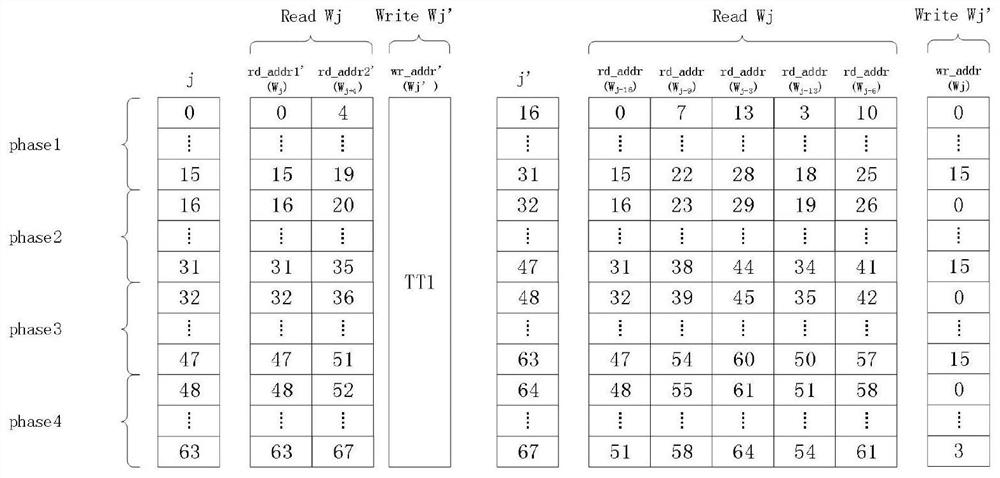
[0025]In the SM3 cryptographic hash algorithm, the message extension is defined as follows: group the message into B(i)Expand to 132 words W according to the following method0,W1,...W67,W’0,W’1,...W’63For the compression function CF:
[0026]A) Group the message B(i)Divided into 16 words W0,W1,...W15.
[0027]For j=16 To 67
[0028]
[0029]B)End For
[0030]For j=0 To 63
[0031]
[0032]C)End For
[0033]Among them, the symbols and characters are interpreted as:
[0034]B(i): The i-th message group
[0035]CF: Compression function
[0036]Word: a bit string of length 32
[0037]P1: Permutation function in message extension,
[0038]X in the formula is a word
[0039]32-bit exclusive OR operation
[0040]<<
[0041]According to the above definition, usually in the process of implementing SM3 cryptographic hash algorithm, 16-67 rounds of W must be calculated first.j52 rounds of calculation are needed, and then W’j64 rounds of calculation are required. In addition, a 132-word memory pair W0,W1,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com