Iris confidential authentication method
An authentication method, iris technology, applied in the direction of homomorphic encryption communication, user identity/authority verification, complex mathematical operations, etc., can solve the problems of low overall performance and high complexity, and achieve good recognition accuracy, good computing efficiency and safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
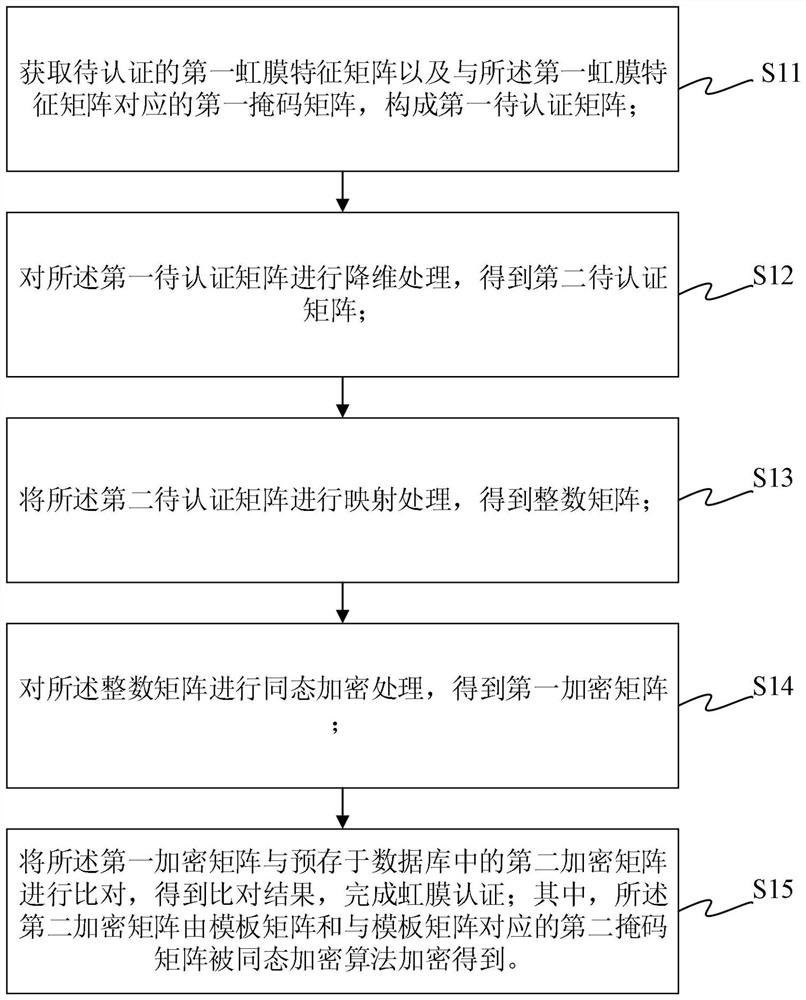
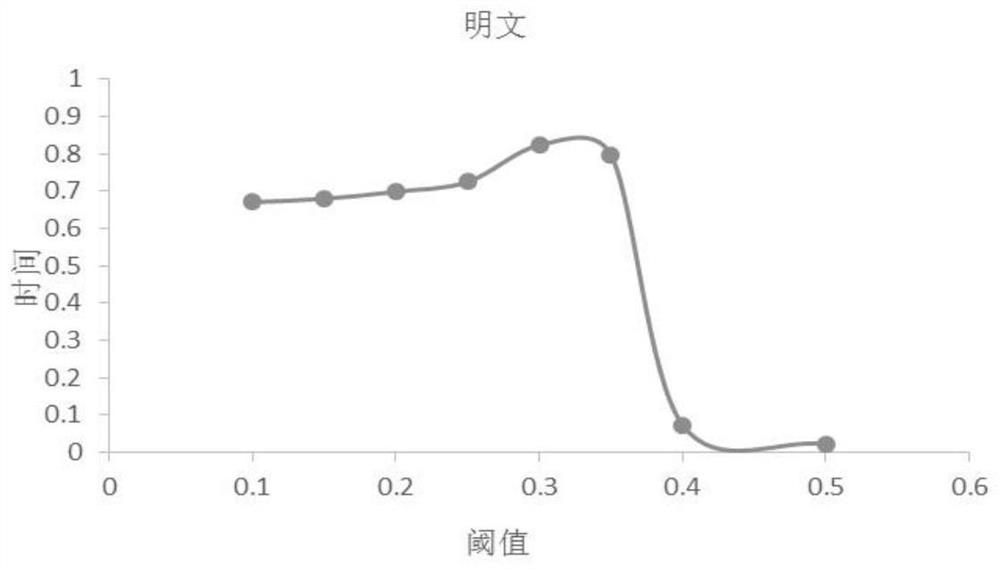
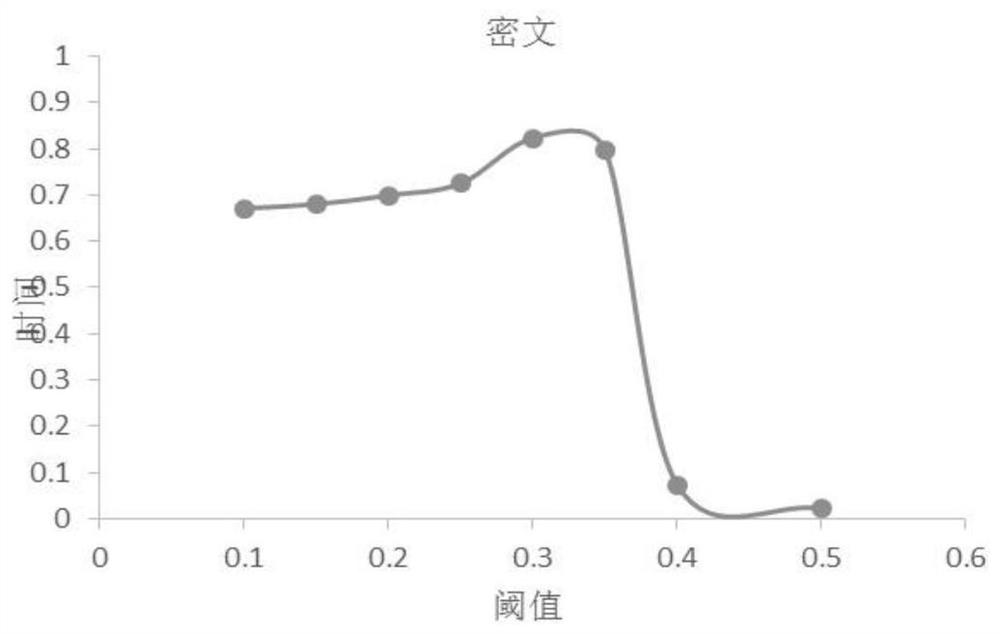
[0057]The following describes the implementation of the present invention through specific specific examples. Those skilled in the art can easily understand other advantages and effects of the present invention from the content disclosed in this specification. The present invention can also be implemented or applied through other different specific embodiments, and various details in this specification can also be modified or changed based on different viewpoints and applications without departing from the spirit of the present invention. It should be noted that the following embodiments and the features in the embodiments can be combined with each other if there is no conflict.
[0058]It should be noted that the illustrations provided in the following embodiments only illustrate the basic idea of the present invention in a schematic manner. The figures only show the components related to the present invention instead of the number, shape, and number of components in actual implemen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com