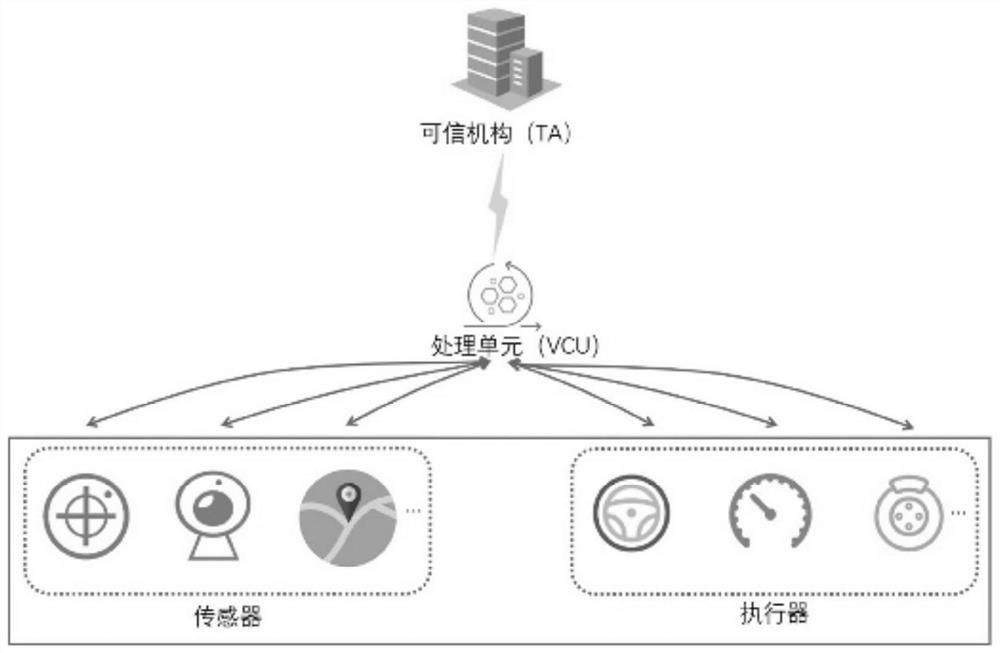
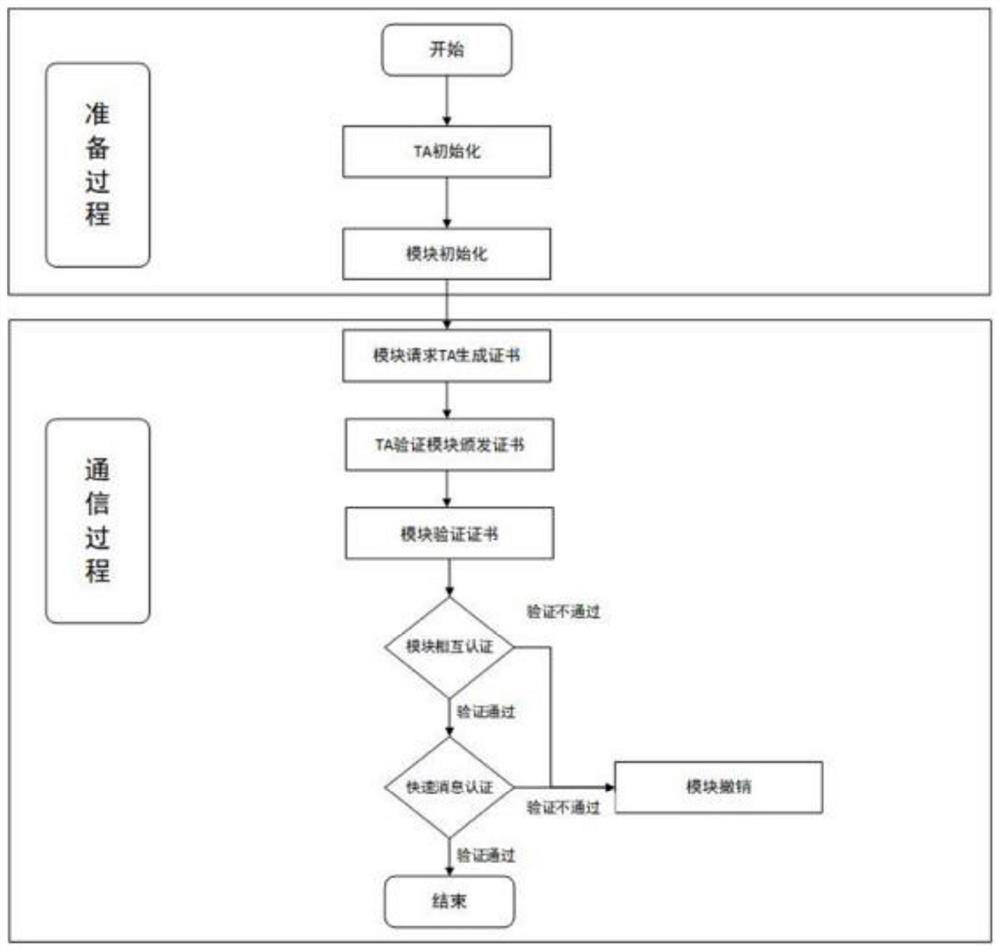
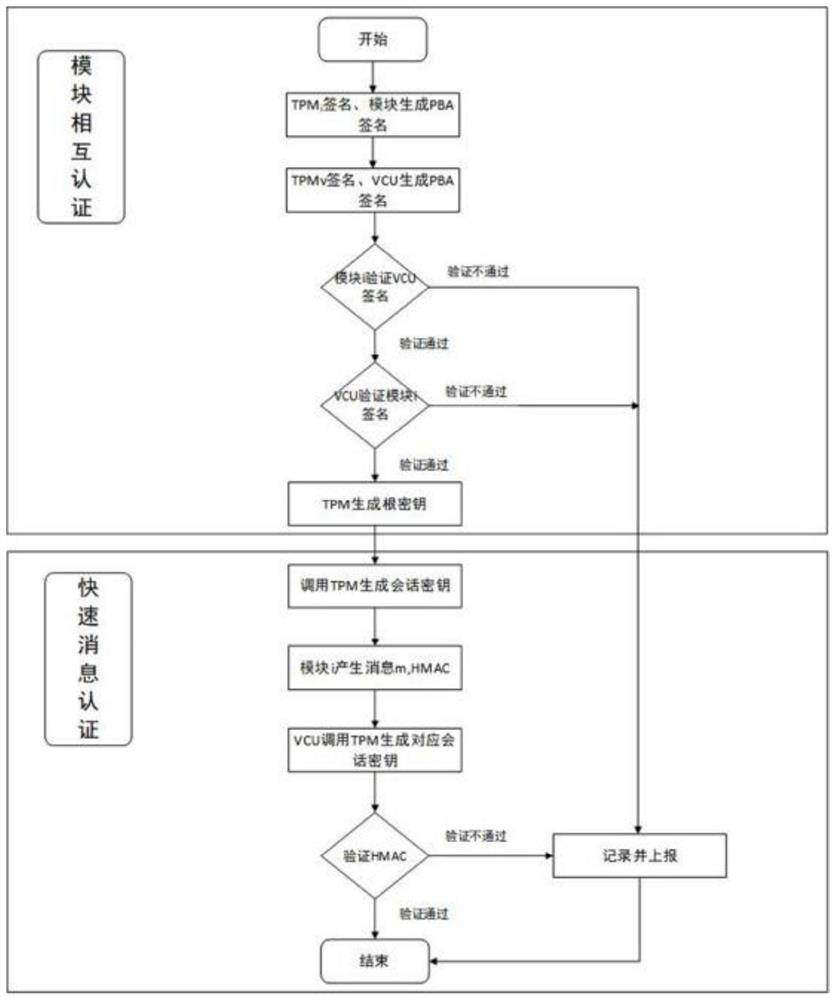
Method and system for credible authentication between modules in intelligent networked vehicle
An authentication method and inter-module technology, applied in transmission systems, digital transmission systems, secure communication devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0108] In this embodiment, related experiments are carried out in the linux system, wherein the calculation related to the trusted platform module TPM is implemented in Intel SGX (Software Guard Extensions). Figure 5 Indicates the time when TA issues certificates and in-vehicle module verification certificates. exist Figure 6 In this example, the time overhead of related PBA signatures is shown. The message authentication time for messages of different lengths from 1KB to 2MB is as follows: Figure 7 shown.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com