Access control method for node resources
A node and resource technology, applied in the blockchain field, can solve problems such as out of control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
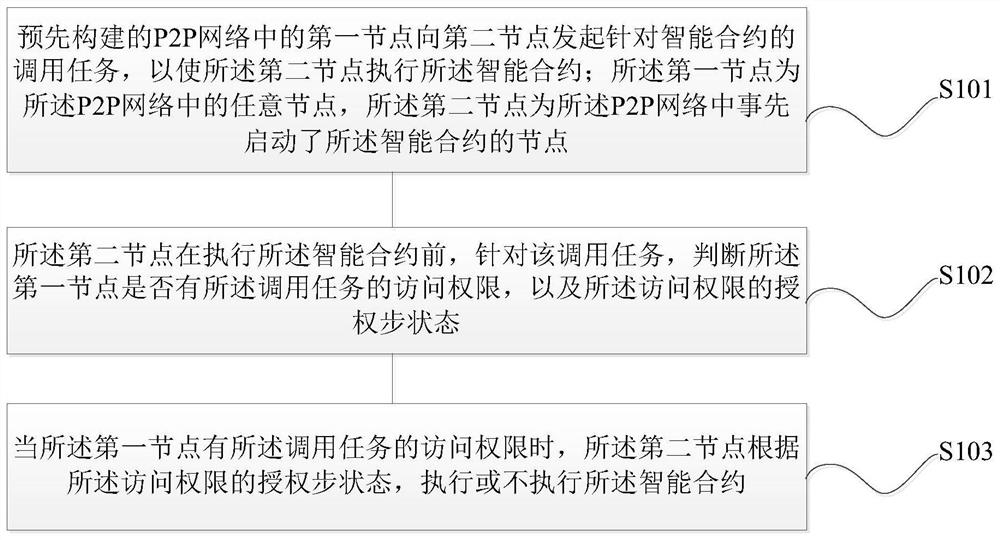
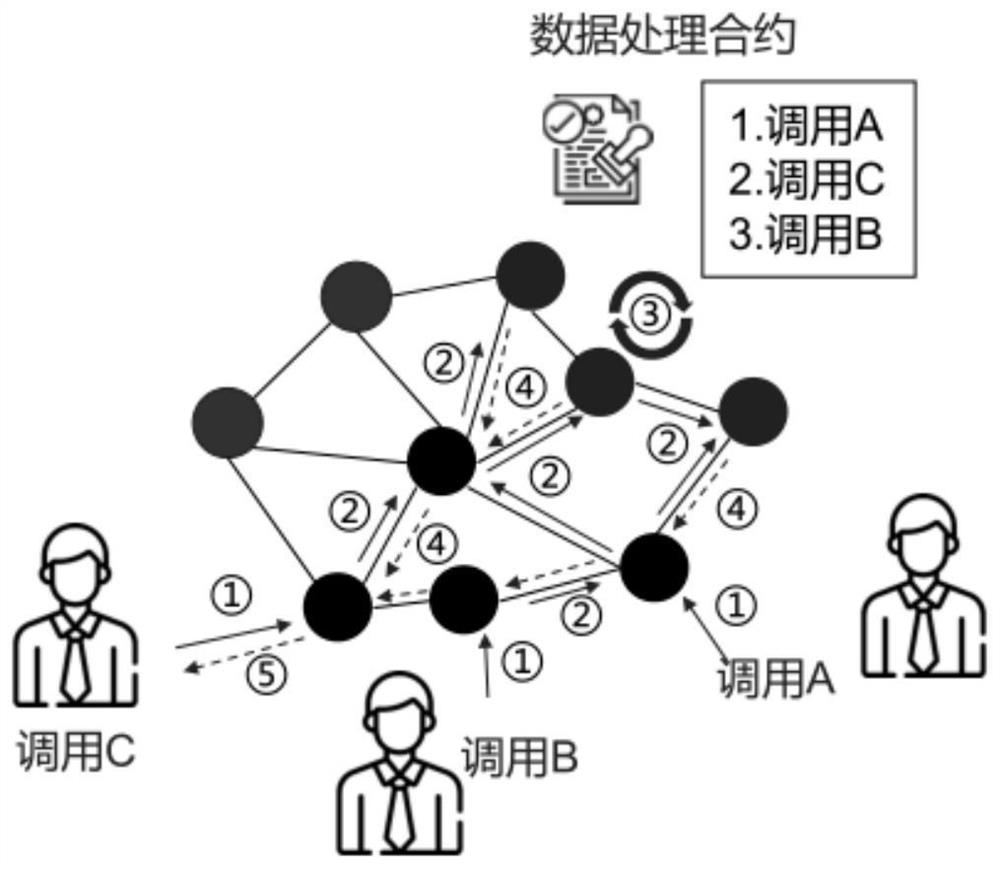
[0070] Aiming at the trusted computing problem in the big data scenario, the embodiment of the present invention is oriented to the big data scenario, and establishes a set of theory and trusted computing framework. It is assumed that the framework system consists of multiple participants to form a trusted computing network, including: data There are three roles: provider, node provider, and data user. Data users use the data of data providers through a network formed together. At the same time, assume: (1) There is a scalable distributed ledger that does not support double spending and cannot be tampered with. (2) Participants participate in the network with the motivation of "maximizing their own interests", that is, data provid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com