A kind of dazed transmission method and device based on elliptic curve
An elliptic curve and transmission method technology, applied in the field of data decryption, to achieve high-strength security, fast processing speed, and simplified calculations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0153] On the basis of research on the scheme of inadvertent electronic envelope based on RSA, the present invention proposes a dazed transmission method based on elliptic curve to improve it.
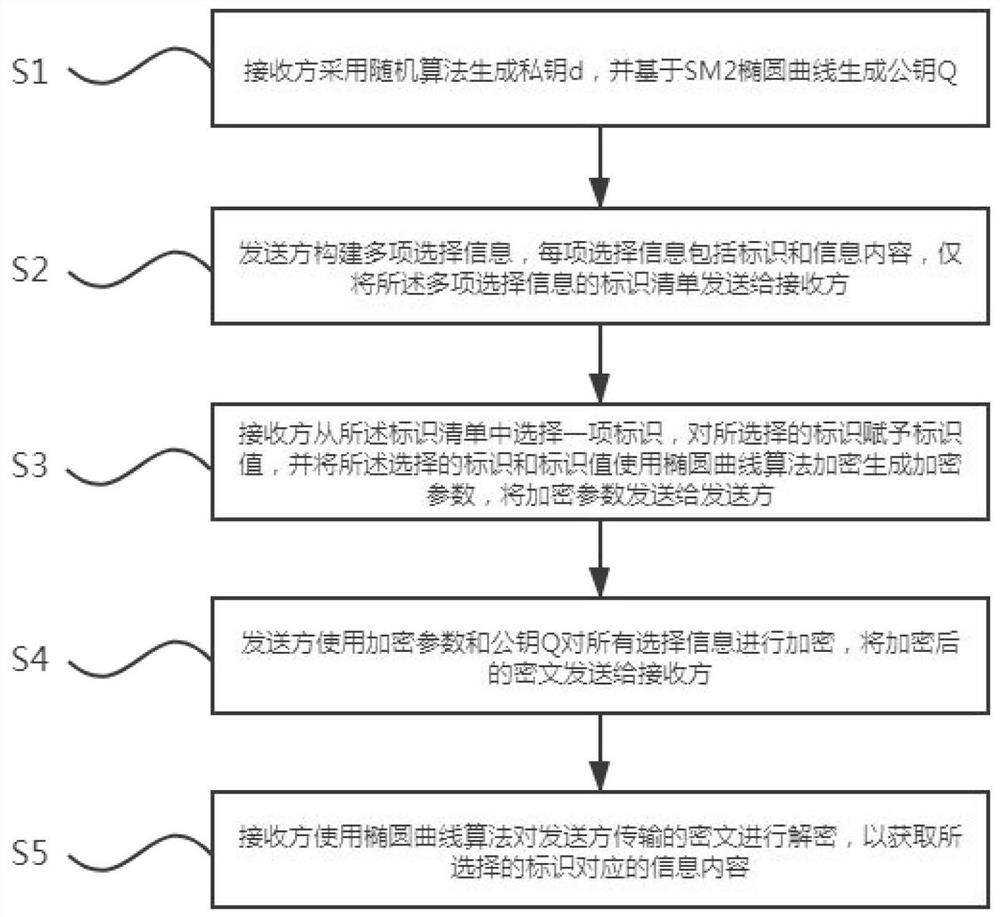
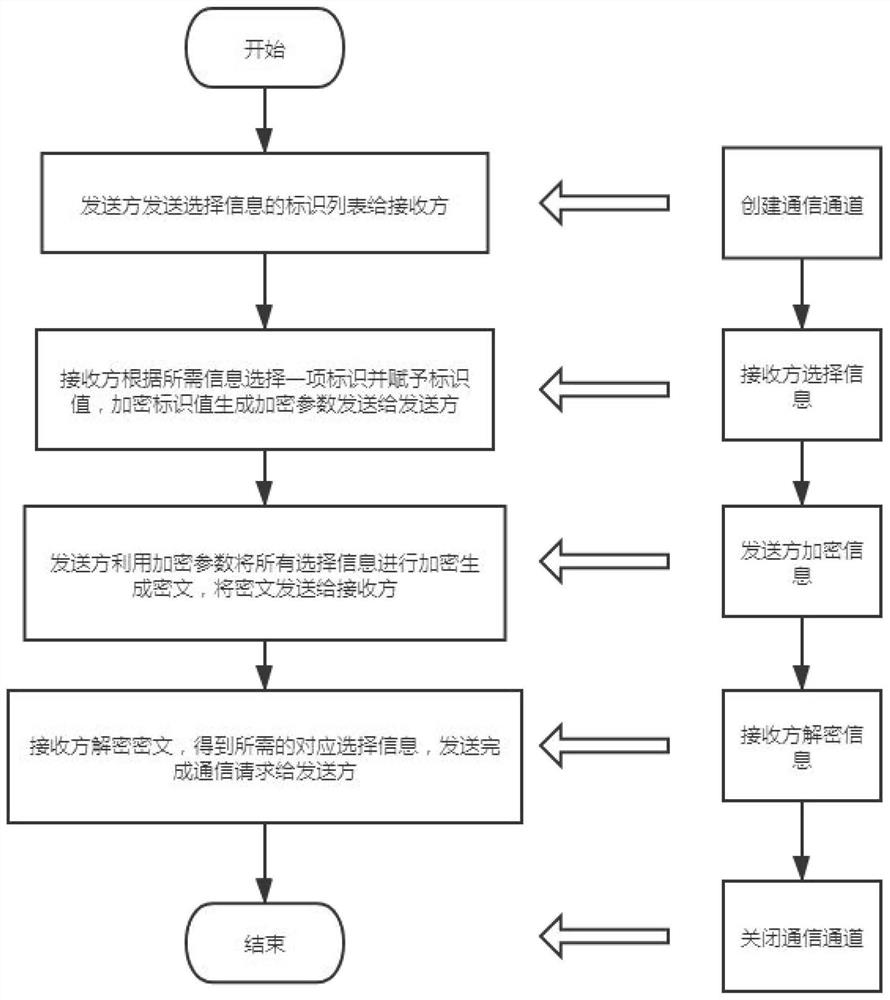
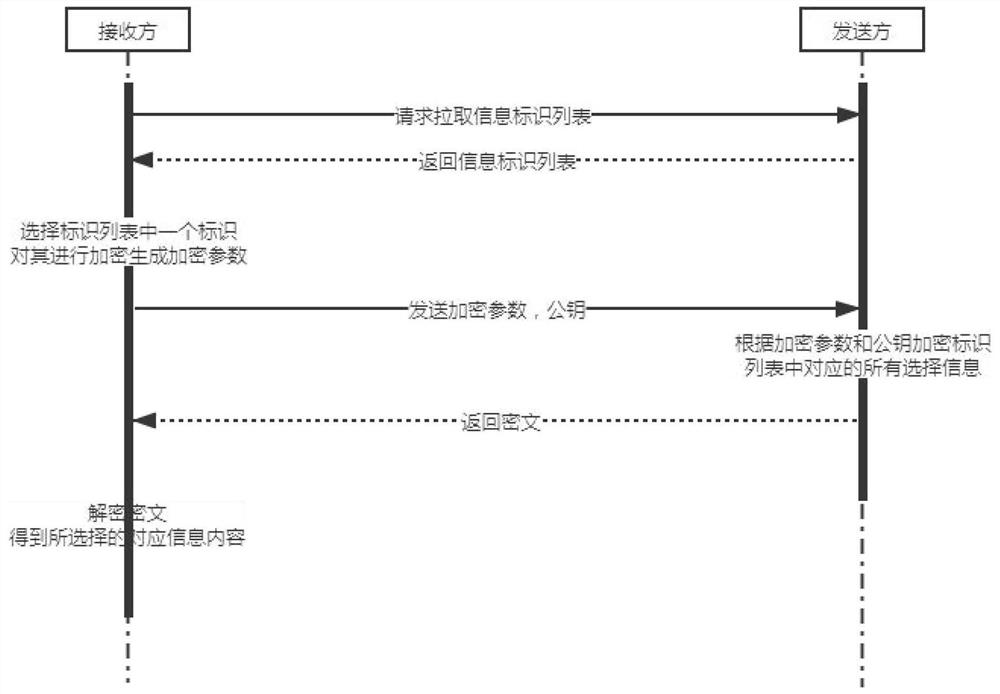
[0154] like figure 1 As shown, it is a flow chart of the method of the present invention. The present invention provides a method of dazed transmission based on elliptic curves, comprising the following steps:
[0155] S1: The recipient uses a random algorithm to generate a private key d, and generates a public key Q based on the SM2 elliptic curve;
[0156] S2: The sender constructs multiple choice information, each choice information includes identification and information content, and only sends the identification list of the multiple choice information to the receiver;
[0157] S3: The receiver selects an identifier from the identifier list, assigns an identifier value to the selected identifier, and encrypts the selected identifier and identifier value using an elliptic curve alg...
no. 3 example
[0220] In this embodiment, the key is encrypted and decrypted, which is realized by performing an XOR operation on the key, and the length of the selection information is extended. The difference from the first embodiment is that in this embodiment, in step S1, The receiver uses a random algorithm to generate the initial private key d, and generates the initial public key Q based on the elliptic curve algorithm, and uses another method in steps S4 and S5 to realize the process of this scheme. The specific steps are as follows:
[0221] S4": The sender uses the elliptic curve algorithm to generate a key pair for each piece of selection information, uses the public key in the key pair to encrypt the corresponding selection information, and uses the encryption parameters and the initial public key Q to encrypt each The private key in the key pair is encrypted, and the ciphertext is generated based on all encrypted selection information and private key and sent to the receiver:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com