Big data analysis device for information security operation and maintenance management
An information security and analysis device technology, applied in the field of information communication, can solve problems such as unpredictable severity, unclear operation identity, and out-of-control operation behavior, so as to achieve scientific and reasonable design, improve safety management, and improve safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The following examples are for illustrative purposes only and are not intended to limit the scope of the invention.
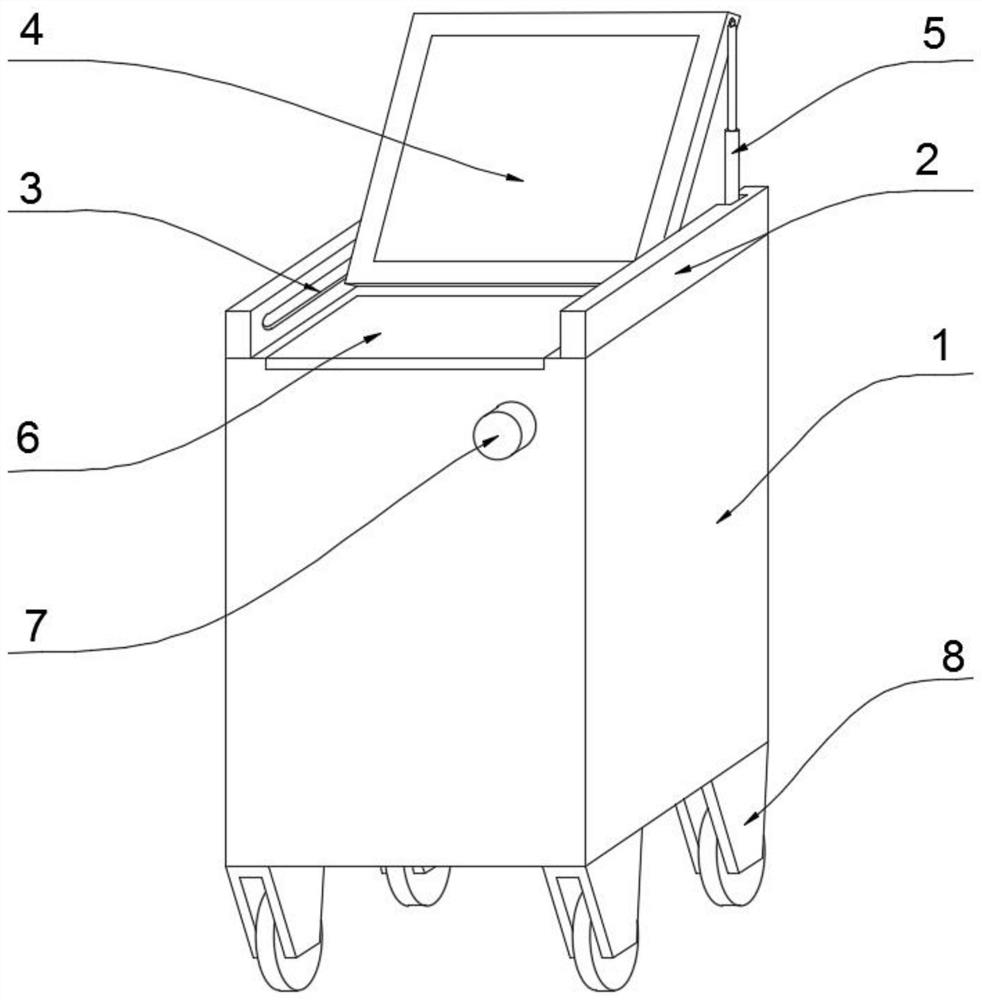
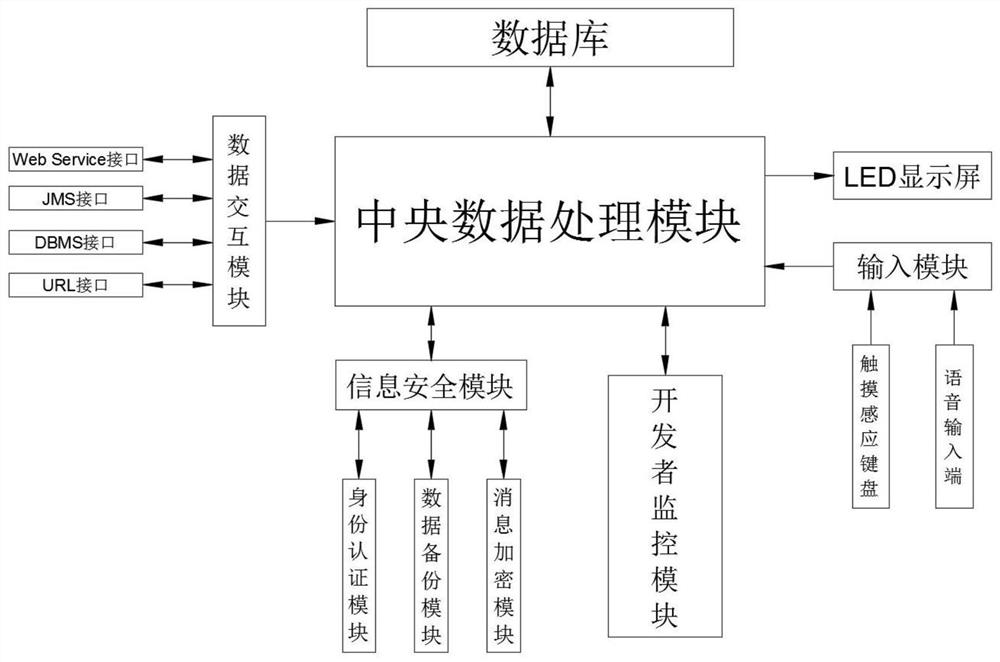
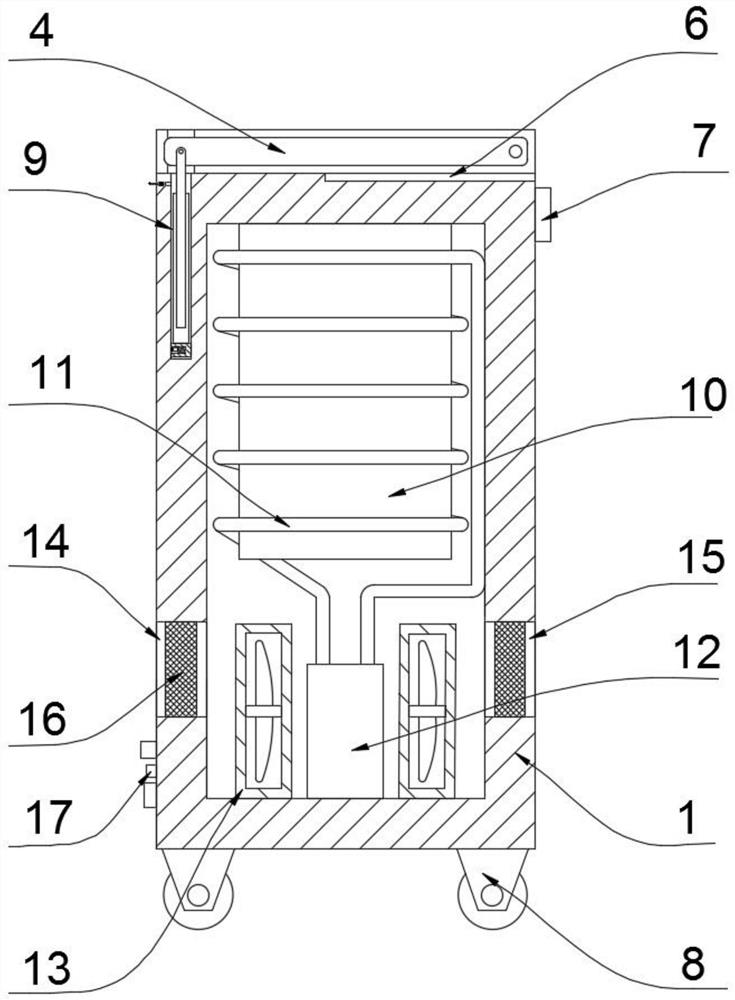
[0030] refer to Figure 1-5 , a big data analysis device for information security operation and maintenance management, including a box body 1, the box body 1 is connected with a data analysis processing device 10, and the data analysis processing device 10 includes a central data processing module, a database, a data interaction module, an information Security module, developer monitoring module, LED display 4 and input module;
[0031] The central data processing module analyzes the data reported by each module, deeply excavates security risks and potential failures, and reports them to the LED display 4. Its main functions are security risk analysis, correlation, fault location, vulnerability scanning, data mining and real-time monitoring Wait;
[0032] The database is used to store the analyzed data information, and the database is stored in the fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com