Data link anti-quantum computing communication method and system based on ID cryptography and symmetric key pool
A technology of quantum computing and communication methods, applied in the field of data link systems, can solve problems such as low security, large capacity of symmetric key pool, communication security threats, etc., to enhance the use security, security guarantee, and improve security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
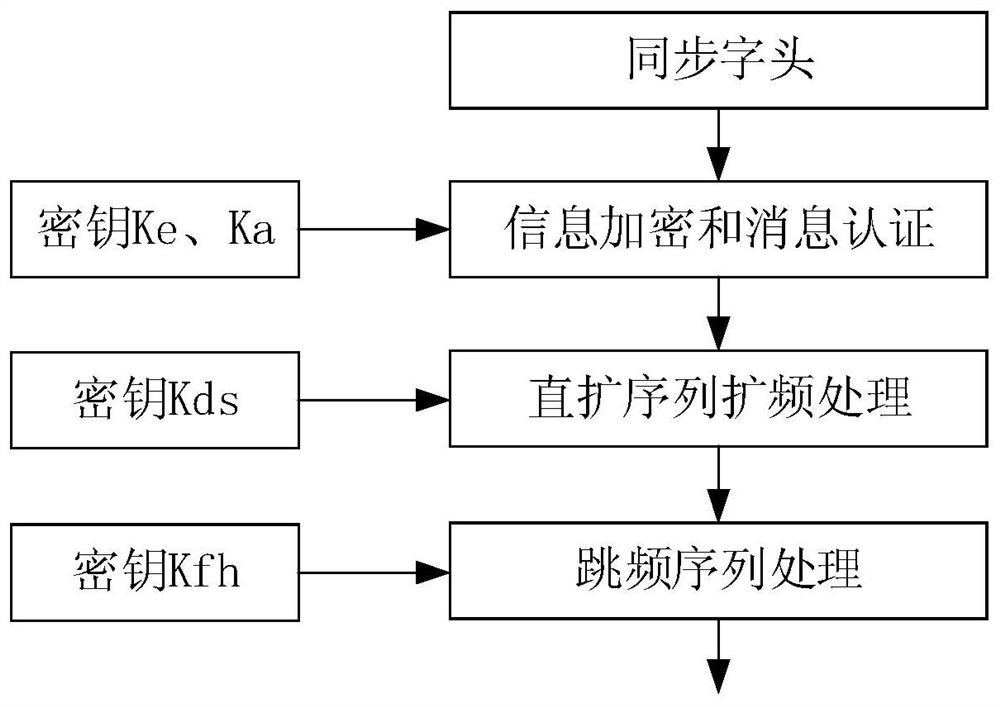
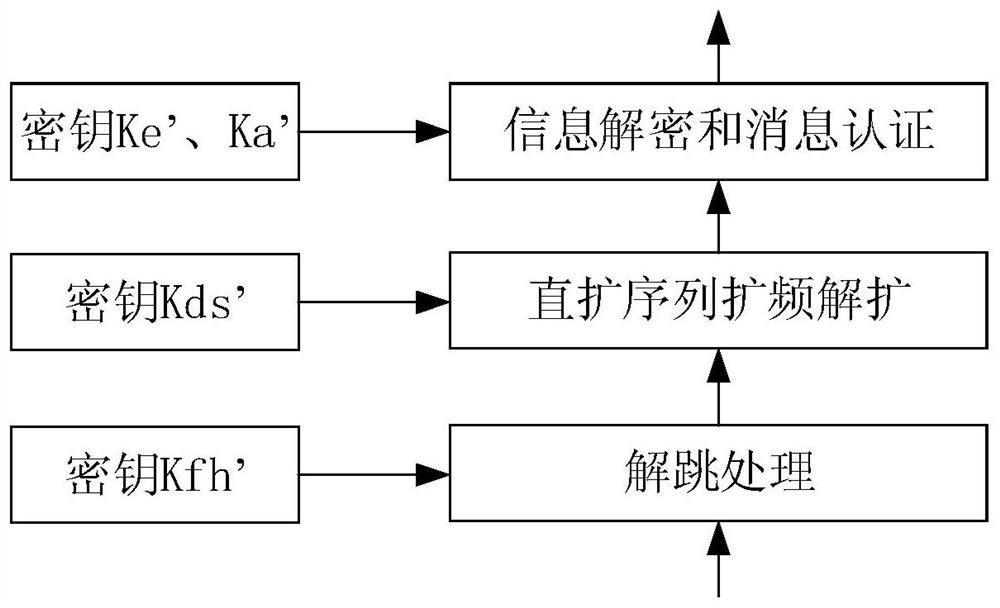
[0069] This embodiment proposes a data link anti-quantum computing communication method based on ID cryptography and symmetric key pool, including the following steps:
[0070] 1. Synchronize using the synchronization prefix method:
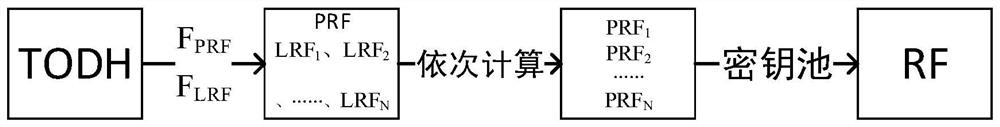
[0071] The sending end calculates the synchronization frequency. In order to improve the anti-reconnaissance performance of the synchronization head, the synchronization frequency changes with the change of the real-time information (TOD) of the system. TOD is the real-time information of the system, which is obtained by reading the local clock, and its accuracy is also determined by the local clock, which can be accurate to milliseconds or even microseconds. The clock information is divided into TODH and TODL according to the needs of the method, which represent the high byte of time and the low byte of time respectively. When we calculate the random code that determines the synchronization frequency, we can select a part of the real-time infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com