Trajectory law analysis method for realizing information visualization
An analysis method and trajectory technology, applied in the field of security and information, can solve the problems of low efficiency of security analysis, inability to efficiently analyze regular information, and work troubles of security staff, so as to improve the efficiency of security analysis and facilitate work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
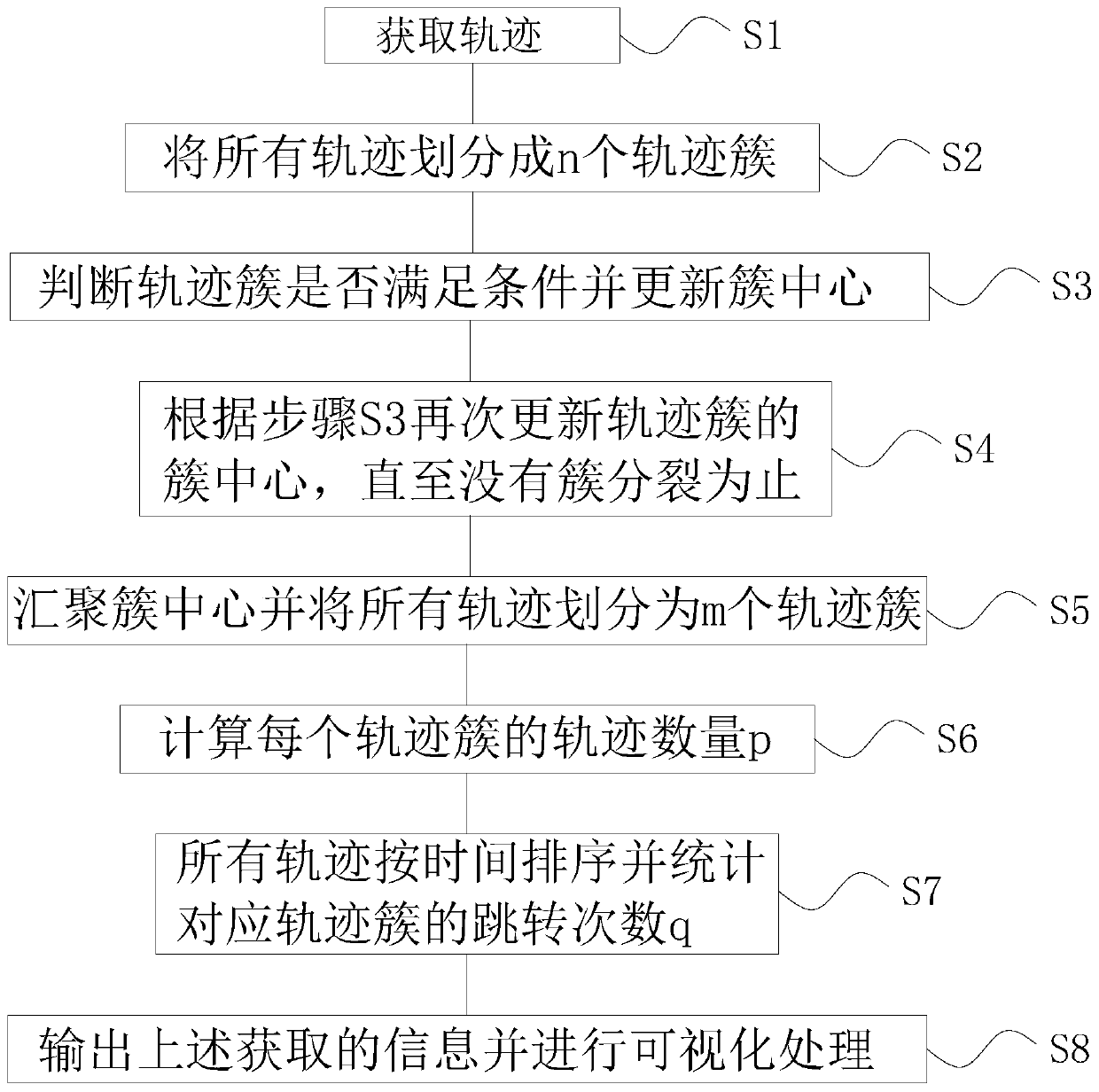
[0031] refer to figure 1 As shown, the present invention provides a trajectory law analysis method for realizing information visualization, comprising the following steps:
[0032] Step S1, obtaining all trajectories collected by the monitoring equipment;
[0033] Step S2, dividing all trajectories into n trajectory clusters;
[0034] Step S3, judging whether each trajectory cluster satisfies the condition, and updating the cluster center of each trajectory cluster;
[0035] Step S4, divide the cluster centers of n trajectory clusters into m cluster centers according to the cluster centers updated in step S3, until there is no cluster split;
[0036] Step S5, gather m cluster centers, and split all trajectories into m trajectory clusters;
[0037] Step S6, calculating the number p of trajectories for each trajectory cluster;
[0038] Ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com