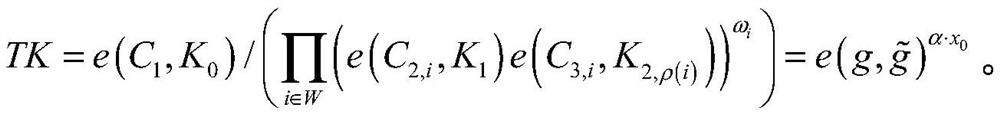An attribute-based secure communication method and system supporting ciphertext pattern matching
A pattern matching and secure communication technology, applied in the field of communication security, can solve the problems of reducing the efficiency of data sharing and query, unfavorable data sharing and query, etc., to achieve the effect of saving communication and computing costs and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
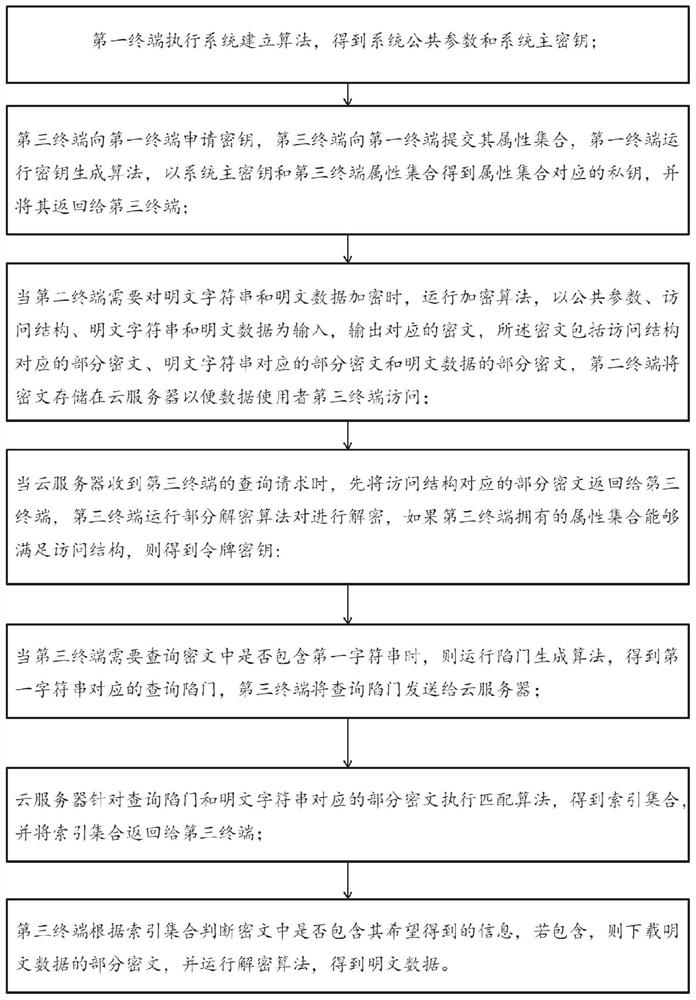
[0060] Embodiment 1 of the present disclosure provides an attribute-based secure communication method supporting ciphertext pattern matching, which is applied to a data query terminal;
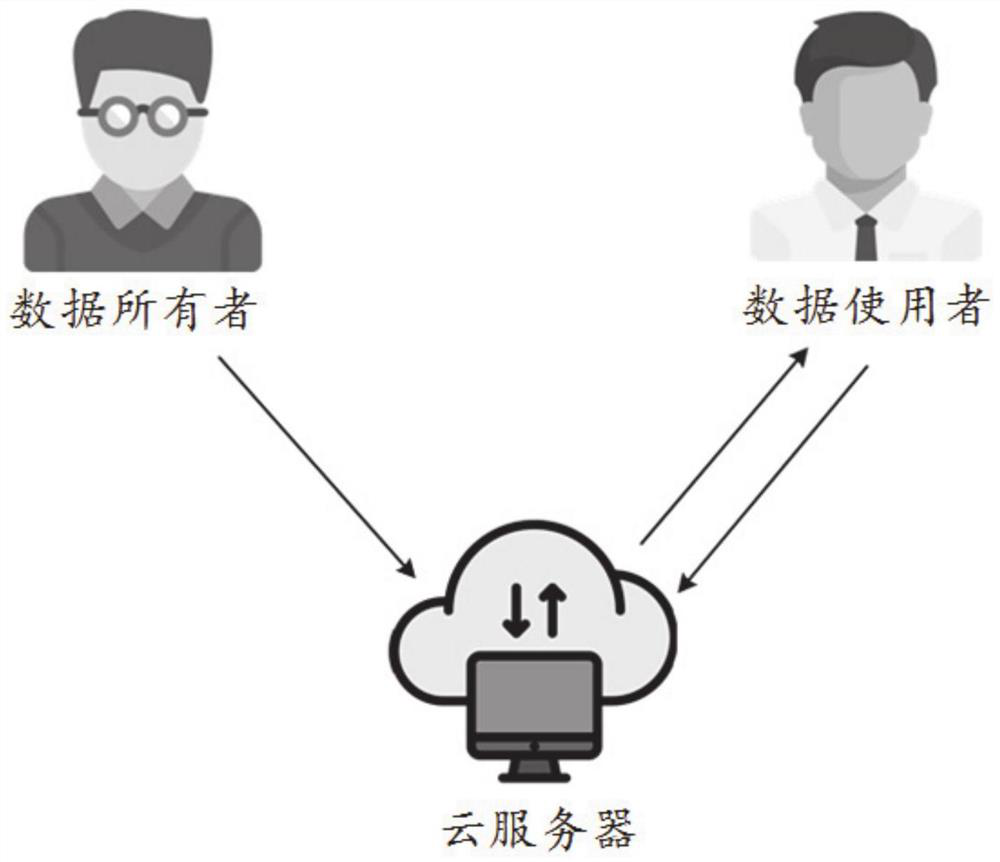
[0061] The data query terminal sends its own attribute set to the external encryption terminal, and receives the private key of its own attribute set returned by the external encryption terminal;
[0062] The data query terminal sends a data query request to the data storage terminal, obtains part of the ciphertext corresponding to the access structure in the ciphertext, and runs a partial decryption algorithm to decrypt it. If the attribute set owned by the data query terminal can satisfy the access structure, the token is obtained. key;
[0063] When the data query terminal needs to query whether the ciphertext contains the first string, it runs the trapdoor generation algorithm, and obtains the query trapdoor corresponding to the first string according to the private key and token secret ke...
Embodiment 2
[0108] Embodiment 2 of the present disclosure provides an attribute-based secure communication device supporting ciphertext pattern matching, including a processor;
[0109] The processor sends the device's own attribute set to the external encryption terminal, and receives the private key of the device's own attribute set returned by the external encryption terminal;
[0110] The processor sends a data query request to the data storage terminal, obtains part of the ciphertext corresponding to the access structure in the ciphertext, and runs a partial decryption algorithm to decrypt it. If the attribute set owned by the processor can satisfy the access structure, the token key is obtained ;
[0111] When the processor needs to query whether the ciphertext contains the first string, it runs the trapdoor generation algorithm, obtains the query trapdoor corresponding to the first string according to the private key and token secret key of its own attribute set, and sends the quer...
Embodiment 3
[0115] Embodiment 3 of the present disclosure provides an attribute-based secure communication method supporting ciphertext pattern matching, which is applied to a data storage terminal;
[0116] The data storage terminal obtains and stores the ciphertext obtained by encrypting public parameters, access structure, plaintext character strings and plaintext data sent by the external terminal, and the ciphertext includes part of the ciphertext and plaintext corresponding to the access structure Part of the ciphertext corresponding to the string and part of the ciphertext of the plaintext data;
[0117] The data storage terminal receives the query request from the data query terminal, and returns part of the ciphertext corresponding to the access structure to the data query terminal, so that the data query terminal can judge that its own attribute set can satisfy the access structure to obtain the token secret key ;
[0118] The data storage terminal acquires the query trapdoor c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com