Storage file and network data flow encryption communication detection method and system
A technology for encrypting communication and storing files, which is applied in the field of information security, can solve problems such as difficult implementation, and achieve the effect of enhancing feature expression ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
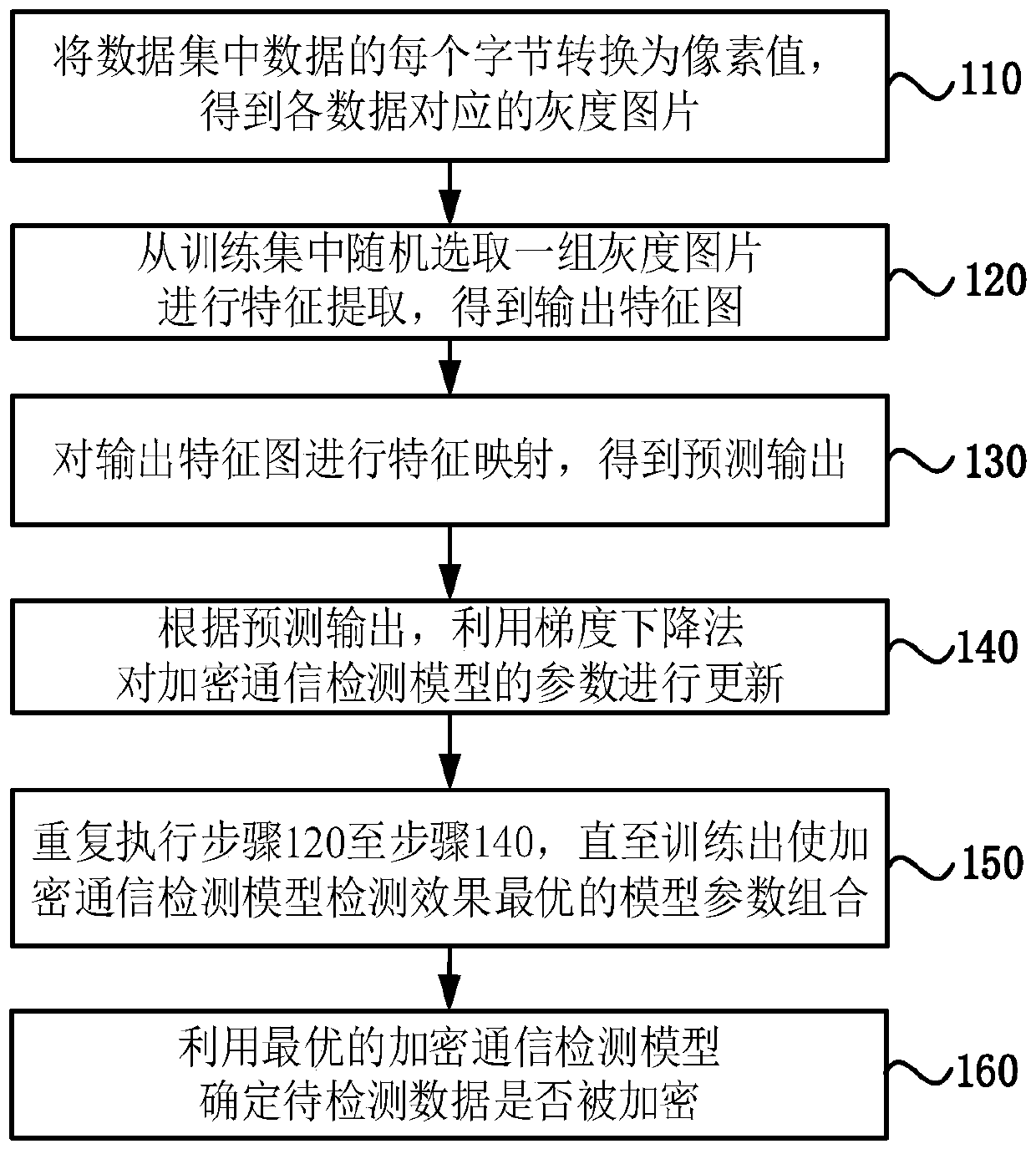
[0069] figure 1 It is a schematic flowchart of a storage file and network data stream encrypted communication detection method provided by the embodiment of the present invention. The method is implemented based on a deep convolutional neural network (CNN), and is suitable for detecting whether data is encrypted. Such as figure 1 As shown, the method may specifically include the following steps:
[0070] Step 110: Convert each byte of the data in the data set into a pixel value to obtain a grayscale image corresponding to each data.
[0071] In this embodiment, the file type corresponding to the data in the data set is at least one of storage files and network data stream files; the data type of storage files is at least one of video data, audio data and text data; network data stream The data type of the file is at least one of network browsing traffic data and FTP transmission traffic data. Optionally, after acquiring the data set, convert the data in the data set into a ...
Embodiment 2
[0157] According to the method of embodiment 1, build a kind of storage file and network data stream encryption communication detection system, this system comprises encryption communication detection model, preprocessing module and detection output module;
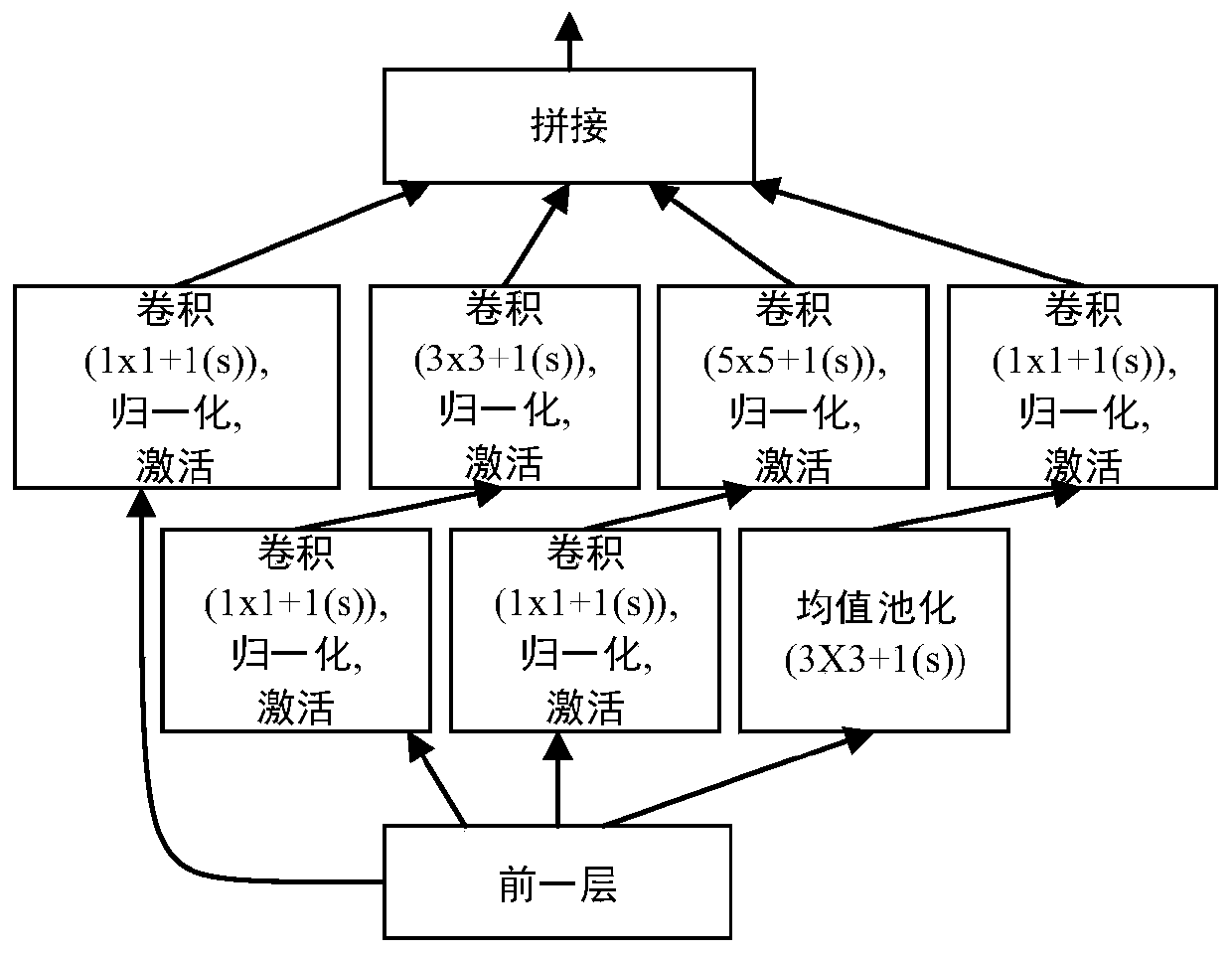
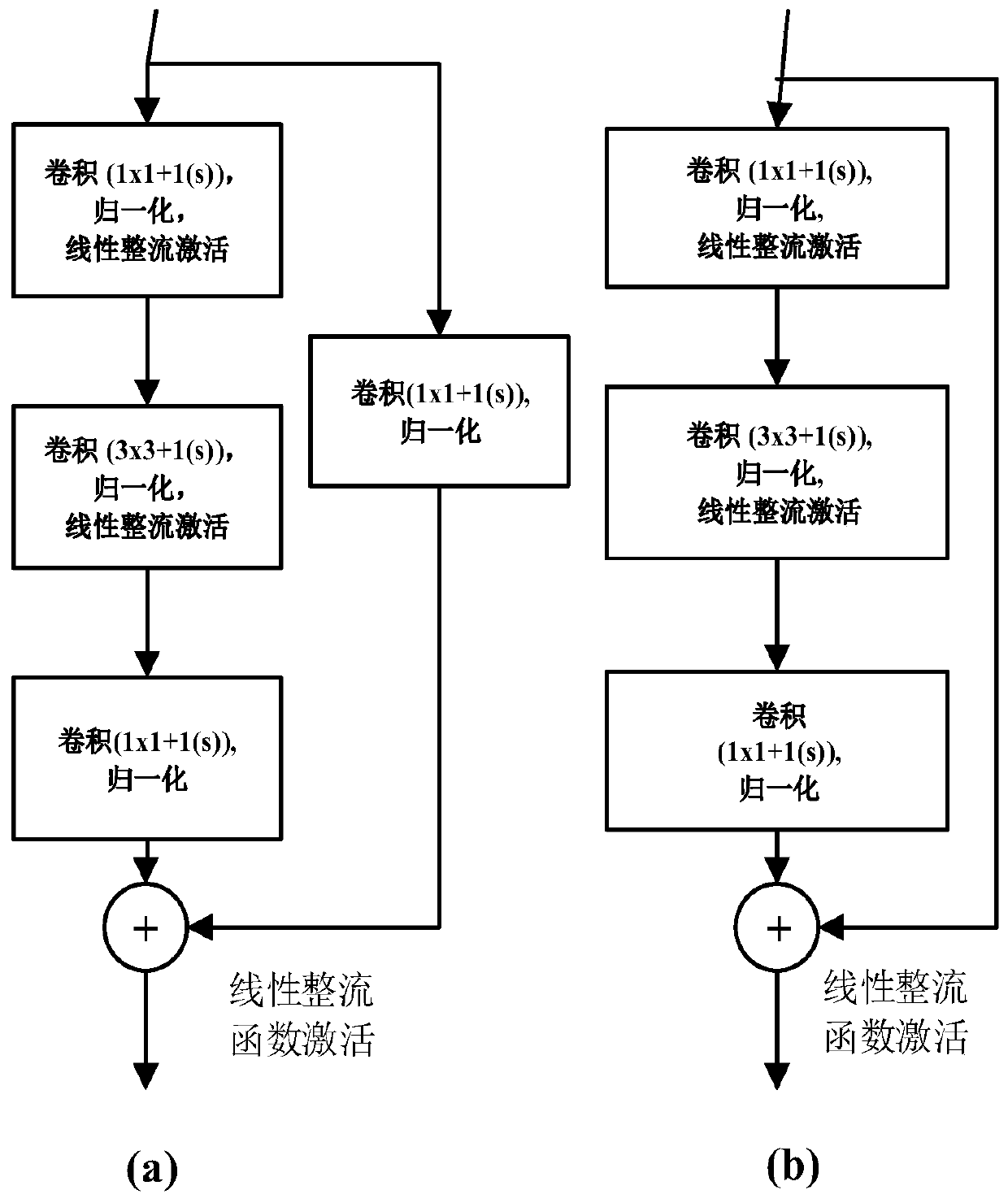
[0158] The encrypted communication detection model includes a feature extraction module and a feature mapping module; wherein, the feature extraction module is used to perform feature extraction on a two-dimensional grayscale image to obtain an information correlation feature map of the two-dimensional grayscale image; the feature The mapping module is used to perform feature mapping on the information correlation feature map to obtain the result of whether the data to be tested is encrypted;
[0159] The preprocessing module is used to perform byte conversion processing on the data to be detected to obtain a two-dimensional grayscale image corresponding to the detected data;
[0160] The detection output module is used t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com