File storage method, file downloading method, file processing method and related components
A file storage and file download technology, applied in electrical components, transmission systems, etc., can solve the problem of not being able to transfer files to intranet nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
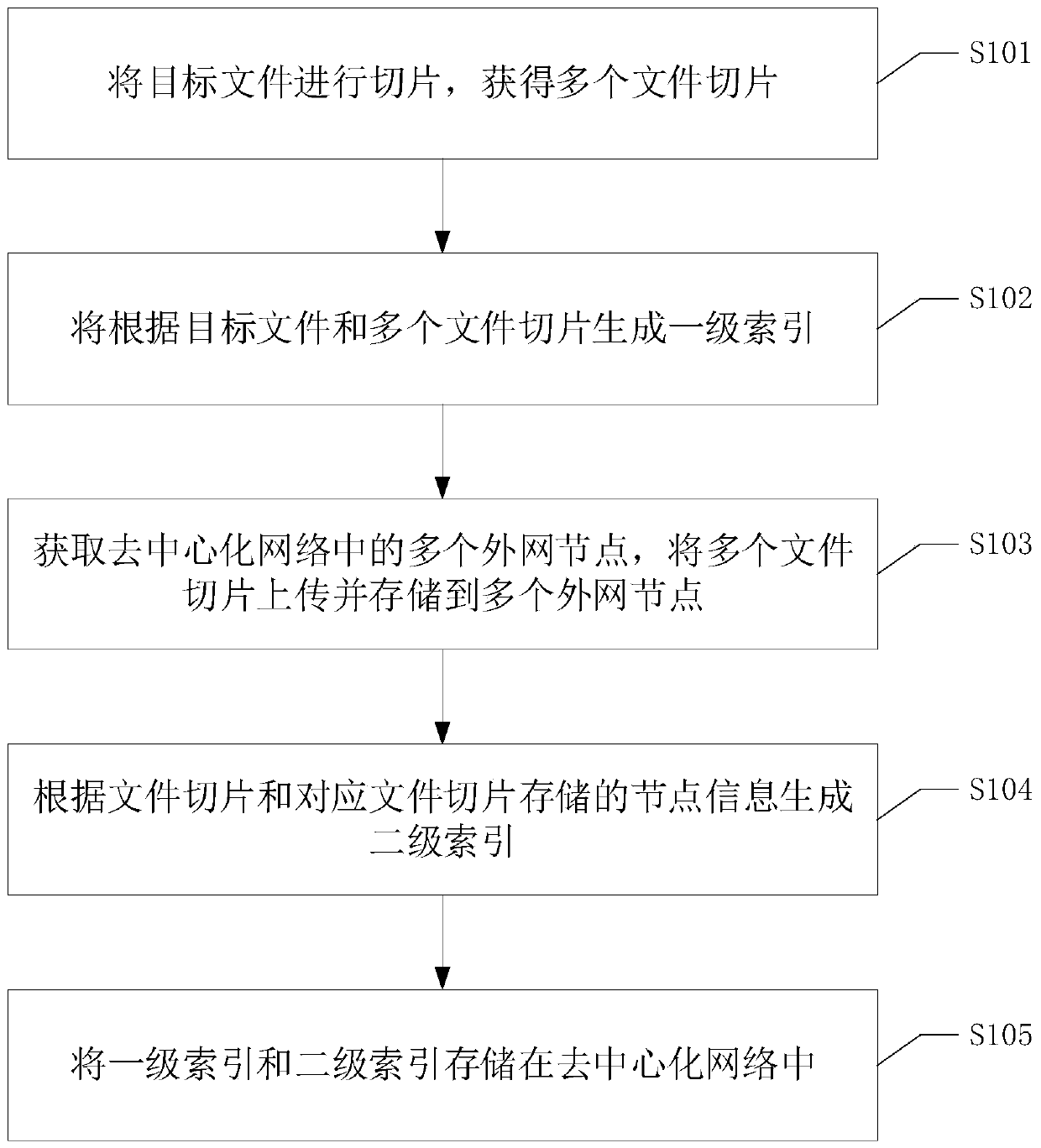
[0081] Please refer to figure 1 , figure 1 It is a flow chart of a file storage method in the embodiment of this application, the method can be applied to the nodes of the decentralized network, and the method includes the following steps:
[0082] S101. Slice the target file to obtain multiple file slices.
[0083] In this embodiment, the file size threshold that needs to be sliced can be set in advance, and then when the client determines that a file needs to be uploaded, if the file size is greater than the file size threshold, it is determined that the file needs to be sliced, that is, the target file is Files that need to be uploaded in slices. For example, when the minimum file slice is set to 32M, the file size threshold may be set to 32M.
[0084] Preferably, in order to avoid large file slicing, the number of slicing is too large, resulting in complicated uploading. In this embodiment, the number of slices can also be limited. Different file slice sizes can be ...
Embodiment 2
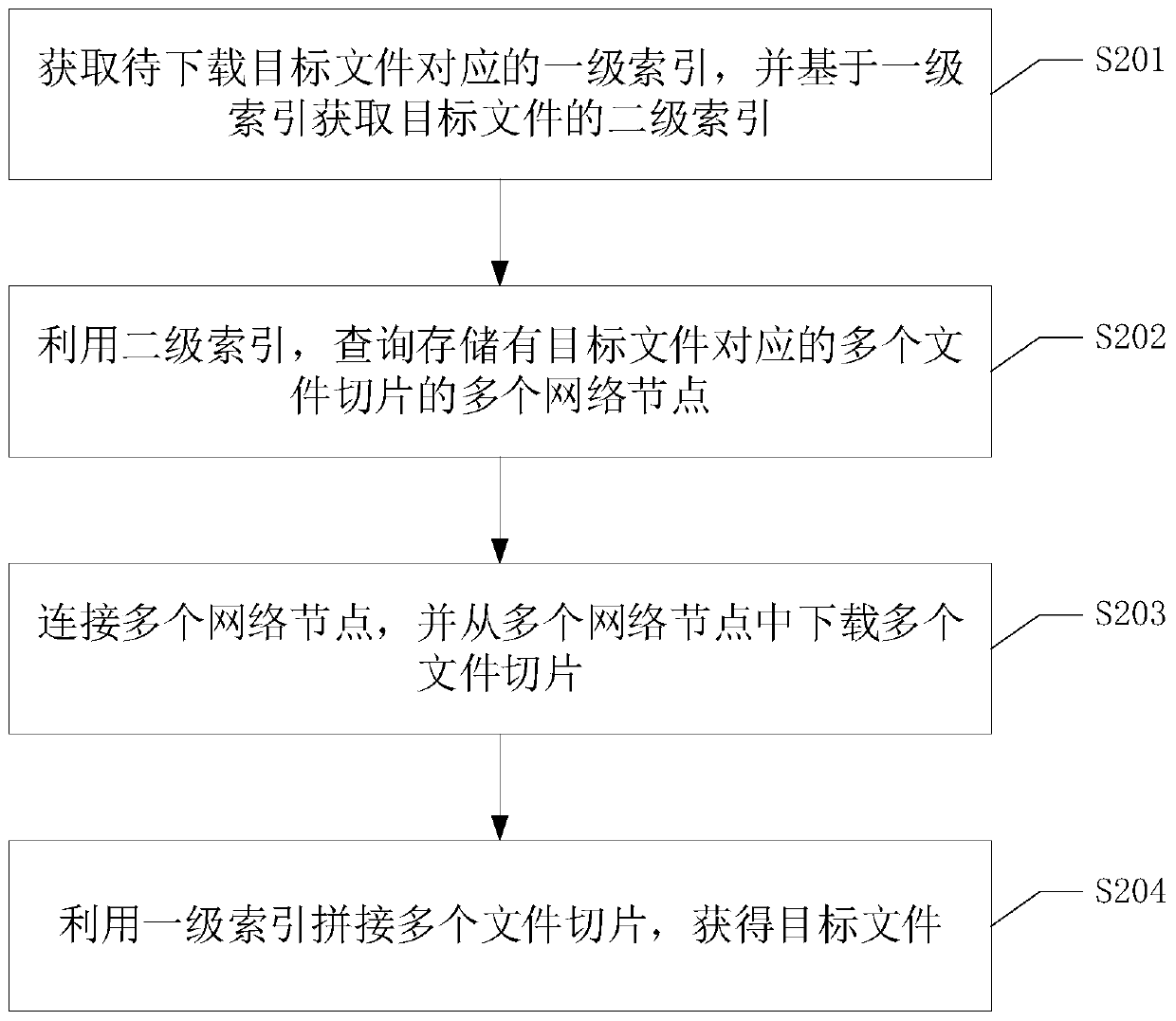
[0124] Please refer to figure 2 , figure 2 It is a flow chart of a file download method in the embodiment of this application, the method can be applied to the nodes of the decentralized network, and the method includes the following steps:
[0125] S201. Obtain a primary index corresponding to a target file to be downloaded, and obtain a secondary index of the target file based on the primary index.
[0126] In this method, the node of the decentralized network can obtain the corresponding first-level index of the file to be downloaded when receiving the client's target file download request, or when the node itself needs to download the target file.
[0127] Then, based on the primary index, the secondary index can be obtained. Wherein, both the first-level index and the second-level index can be represented by a key-value pair (key / value). For ease of description, the key of the first-level index is called the first key, the value of the first-level index is called the...
Embodiment 3
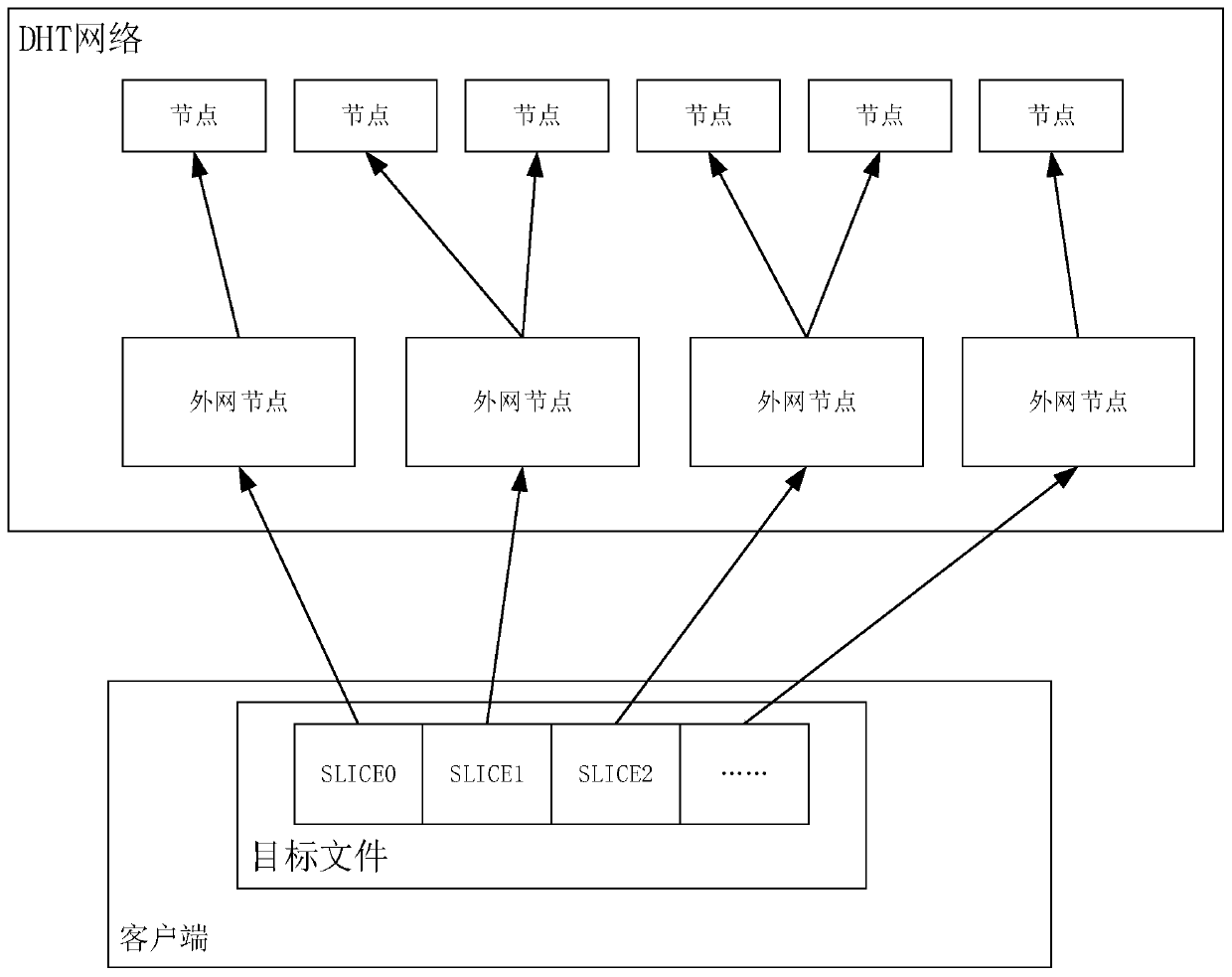
[0154] Please refer to Figure 4 , Figure 4 It is a flow chart of a file processing method in the embodiment of the present application. The method can be applied to external network nodes of a decentralized network. The method includes the following steps:
[0155] S401. Receive a file slice uploaded by a target node, and store the file slice.
[0156] A file slice is a slice of the target file.
[0157] S402. Feed back its own node information to the target node, so that the target node can generate a secondary index of the target file.
[0158] S403. Spreading the file slices to adjacent nodes.
[0159] In order to enable multiple nodes to store the file slices for multi-point download and improve the download speed.
[0160] Among them, the adjacent node can be a node adjacent to the external network node communication, such as the route hop count is 1 or less than a specified threshold such as 5.
[0161] Preferably, in order to spread the file slices according to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com