Quantum secret communication system based on secret sharing and communication method thereof
A quantum secure communication and secret sharing technology, which is applied in the field of quantum secure communication systems, can solve the problems of loss of key security, low validity of identity authentication and non-repudiation, and limited maximum number of connections, so as to avoid failure of identity authentication problems, improve the ability of key services, the effect of high effectiveness and non-repudiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
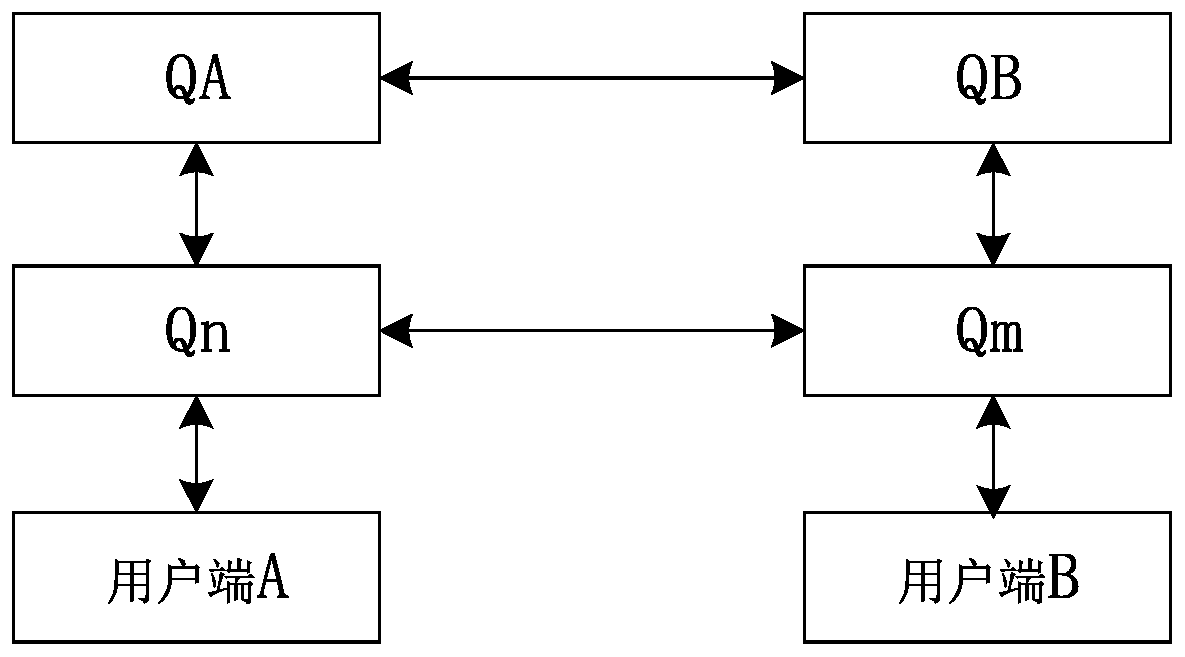
[0048] The networking designed in this embodiment has Num nodes, each node is a quantum communication service station, each quantum communication service station has a QKD device, and the QKD device is defined as Qn(n∈[0, Num-1]), A QKD channel is established between any two Qn, for example, the QKD device of node A is QA, and the QKD device of node B is QB. A QKD channel is established between QA and QB, so that a symmetric key pool can be formed through the QKD channel. And each Qn transmits its own public key to all other Qn through the QKD key during deployment. Therefore, the public keys of all other Qn are stored in the memory of each Qn.
[0049] The asymmetric algorithms used in this embodiment include identity-based cryptography and elliptic curve-based cryptography. The key management server in the quantum communication service station issues private keys to clients (ie nodes). The identity of the client is ID, the public key is PK, and the private key is SK.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com