A security access method and system for a device port
A security access and device port technology, applied in the field of network security, can solve problems such as the inability to eliminate security risks, and achieve the effect of avoiding attacks and strengthening operation and maintenance security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
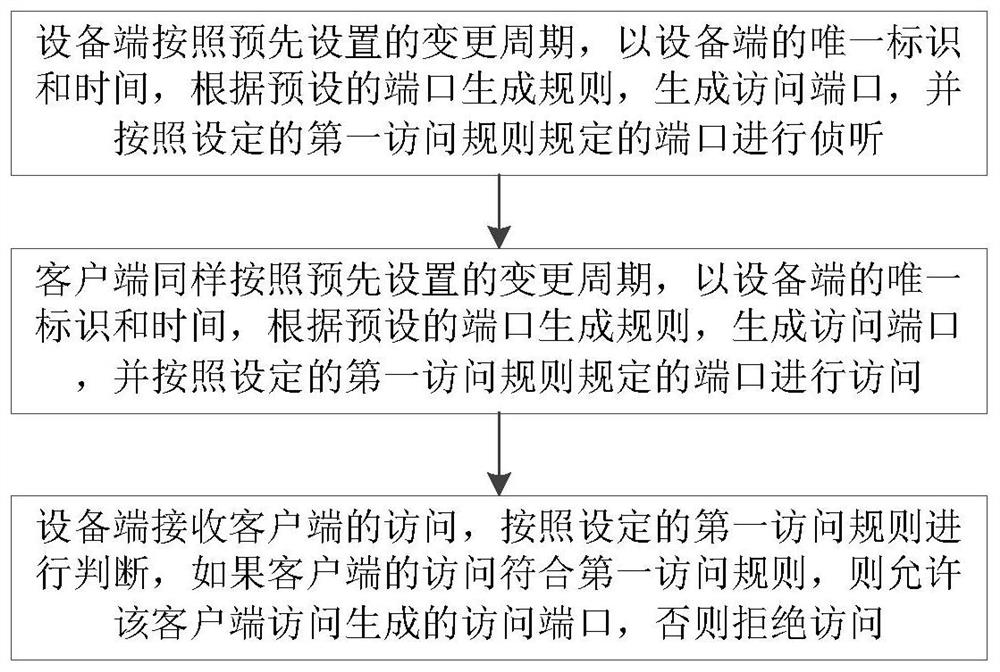
[0051] Embodiment 1. Obtain through the operation and maintenance server.
[0052]Set up an operation and maintenance server that both the device and the client can log in, such as an operation and maintenance server or other management server, to synchronize the unique identifier, time, and change cycle of the device. The specific process is as follows:
[0053] The device side reports the unique identifier and change cycle of the device side to the operation and maintenance server, and synchronizes the time;
[0054] The client accesses the operation and maintenance server, obtains the unique identifier of the device, the change cycle, and synchronizes the time.
Embodiment 2
[0055] Embodiment 2. Obtained by scanning a two-dimensional code or by manual input.
[0056] The operation and maintenance personnel need to know the specific rules in advance, input the unique identification and change cycle of the device to the client, and manually enter the time to synchronize with the device. That is, when the operation and maintenance personnel know the information such as the unique identifier of the device and the port change period, they can manually fill in the unique identifier, port change period, obtain the current time parameters locally, and generate the access port locally on the client side.
[0057] Preferably, the client of the present invention adopts the solution of Embodiment 1 to obtain the unique identifier, time, and change period of the device, which can effectively ensure the security of the port generation rule.
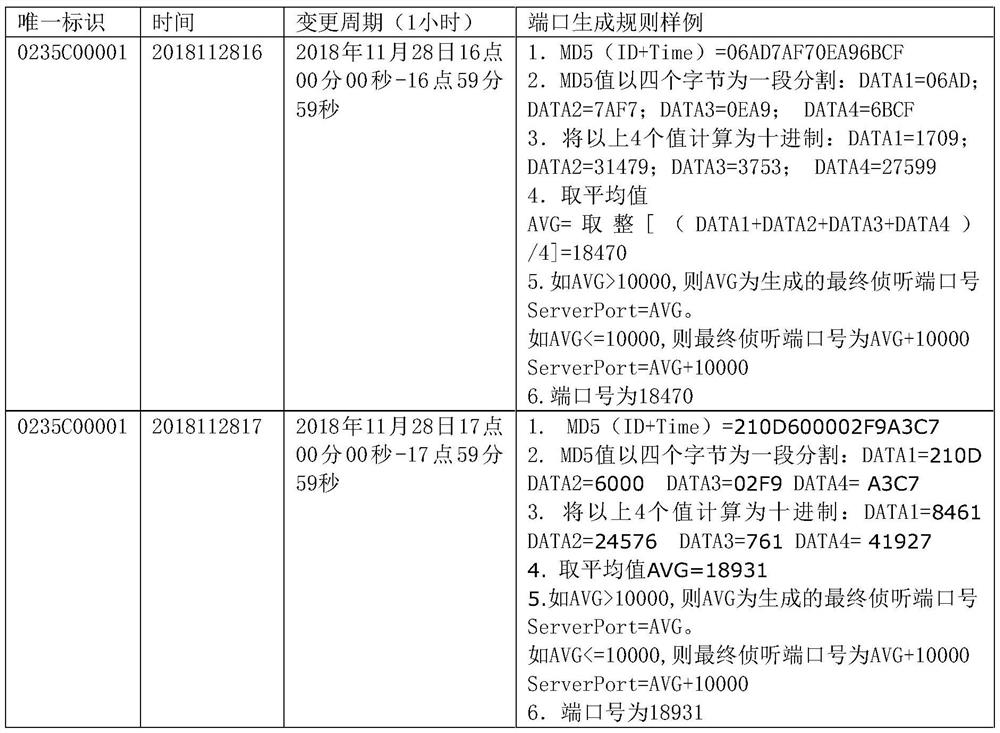
[0058] In an embodiment of the present invention, the port generation rules for the client and the device are shown in t...
Embodiment 3
[0067] Example 3, taking the first row of Table 1 as an example.
[0068] From 16:00 to 17:00 on November 28, 2018, DATA1=1709; DATA2=31479; DATA3=3753; DATA4=27599, with 1709, 31479, 3753, 275994 as the specific port sequence.
[0069] Then the device listens on four ports: 1709, 31479, 3753, and 275994.
[0070] The client needs to send TCP connection packets to the four ports 1709, 31479, 3753, and 27599 in sequence, and the connection packet time of each two ports can be set, for example, it is not allowed to exceed 5 seconds. That is, after sending a TCP connection packet to port 1709, a TCP connection packet needs to be sent to 31479 within 5 seconds, and so on.
[0071] The device determines that the client has initiated a TCP connection to the four ports in turn, and the connection sequence and connection interval meet the preset rules, and then issues firewall configuration rules to release the client's access to port 18470 on the device. After that, the client acce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com